12 Best XDR Software Shortlist
After conducting a comprehensive assessment, I have compiled these top 12 XDR software options for my shortlist:
- ExtraHop - Best for network-based threat detection
- InsightIDR - Best for incident response teams requiring user behavior analytics
- Cortex XDR - Best for unified threat detection and response across networks, clouds, and endpoints
- SentinelOne Singularity - Best for autonomous endpoint protection against all attack vectors
- Cynet 360 AutoXDR - Best for automated threat discovery and response
- Wiz - Best for multi-cloud visibility and security analytics
- IBM Security QRadar SIEM - Best for large-scale threat management and forensic analysis
- CrowdStrike Falcon Endpoint Protection Platform - Best for AI-driven protection against malware and ransomware
- Microsoft Defender for Cloud - Best for Azure-based environments needing threat protection
- Sophos Intercept X: Next-Gen Endpoint - Best for advanced endpoint protection with deep learning technology
- Trend Micro Vision One (XDR) - Best for risk visibility and correlated threat detection across different security layers
- Microsoft 365 Defender - Best for comprehensive protection across Microsoft 365 apps and services
With XDR security, you can quickly identify the root cause of security incidents and prioritize risk-based responses. This centralized visibility allows you to swiftly adjust workflows and SOC capabilities, making it a valuable solution for those struggling with siloed security tools and responding to threats promptly. XDR security addresses these pain points and offers a more efficient and cohesive approach to safeguarding digital assets.
Their use becomes particularly valuable in complex next-generation IT environments with diverse technology stacks, where isolated security tools can struggle to provide a comprehensive picture of the threat landscape. By integrating multiple security capabilities into a single platform, XDR software provides visibility into threats across the entire IT infrastructure, facilitating faster and more efficient responses.
What is XDR Software?
Extended Detection and Response (XDR) software is a security technology designed to provide unified threat detection and response across various network endpoints, servers, and cloud workloads. Typically adopted by enterprise security teams, XDR solutions help identify, prevent, and respond to various security threats.
Extended Detection and Response (XDR) software is an integrated security platform that consolidates and correlates data from multiple sources, including firewall and antivirus systems, to prevent, detect, and respond to cyber-attacks. The primary value of an XDR platform lies in its ability to cover a broader attack surface, managed services, integrate various network security tools, and provide managed detection and response services (MDR).
Overview of the 12 Best XDR Software
1. ExtraHop - Best for network-based threat detection
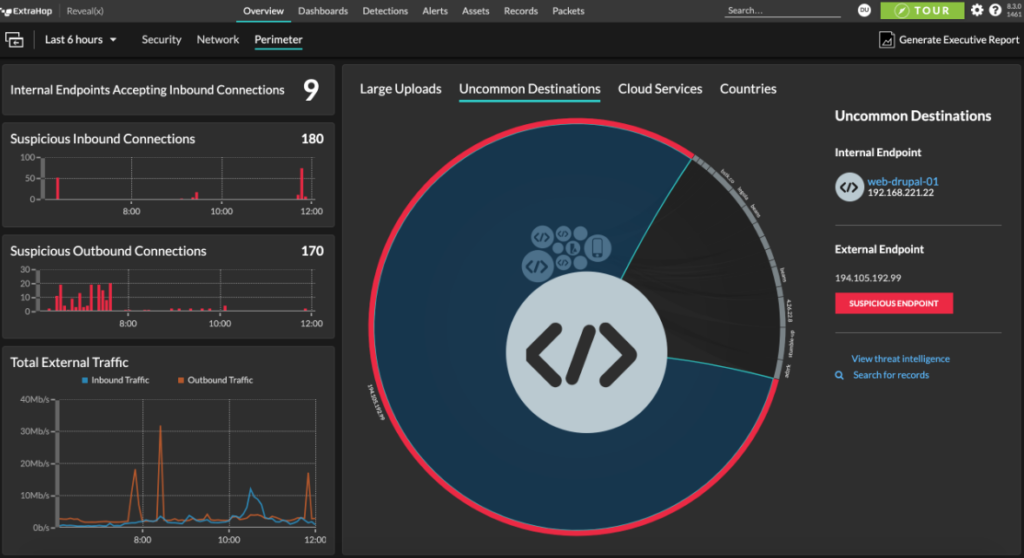
ExtraHop is a network detection and response (NDR) platform that focuses on the security of your network traffic. The tool offers real-time threat detection and automatic responses to abnormalities, making it ideal for network-based threat detection.
Why I Picked ExtraHop:
I chose ExtraHop because of its advanced machine-learning capabilities, allowing for an in-depth network traffic analysis. Its ability to automatically respond to detected threats also sets it apart from many other security tools. ExtraHop is "best for network-based threat detection" as it excels in uncovering hidden dangers and providing security insights within network traffic.
Standout Features & Integrations:
ExtraHop offers advanced threat detection with real-time insights, machine learning-driven anomaly detection, and automated response capabilities. Its features also include comprehensive visibility, which aids in forensic investigations and compliance. In terms of integrations, ExtraHop works well with a range of platforms, including ServiceNow, Phantom, and Ansible, enhancing its ability to automate responses.
Pricing:
Pricing upon request
Pros:
- Advanced threat detection capabilities
- Comprehensive visibility into network traffic
- Effective integrations with other platforms
Cons:
- Pricing information is not publicly available
- May require technical expertise to fully utilize
- Lacks support for non-network endpoints
2. InsightIDR - Best for incident response teams requiring user behavior analytics
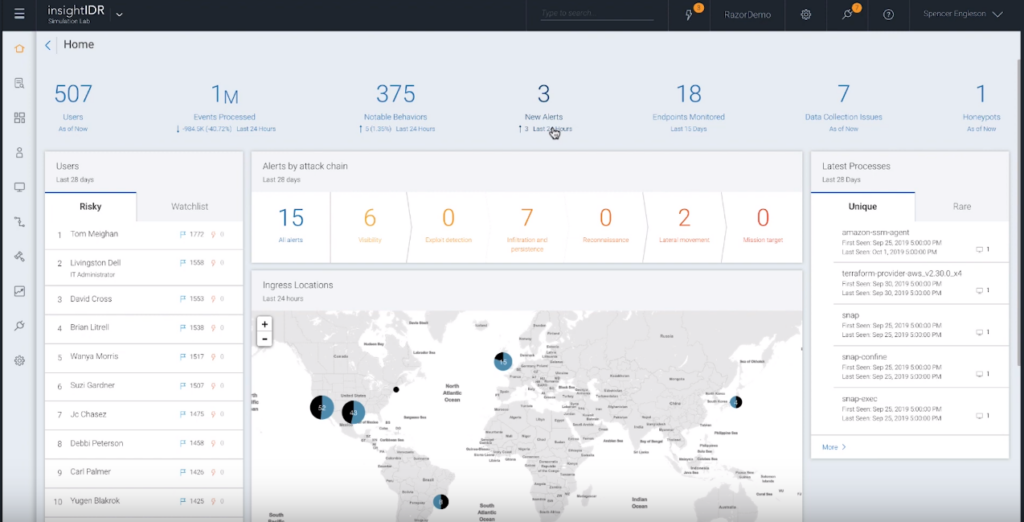
InsightIDR is a security information and event management (SIEM) solution that identifies and investigates suspicious user behavior. It offers robust user behavior analytics, incident detection, and response tools, positioning it perfectly for incident response teams.
Why I Picked InsightIDR:
I picked InsightIDR because it excels in user behavior analytics, which is crucial in identifying insider threats and compromised accounts. It’s comprehensive incident detection and response capabilities further differentiate it from other tools. Therefore, I determined InsightIDR is "best for incident response teams requiring user behavior analytics" because it enables teams to identify and respond to security incidents quickly.
Standout Features & Integrations:
InsightIDR offers automated detection and response capabilities, along with detailed investigation timelines, which are essential for managing incidents effectively. It also provides built-in user behavior analytics that helps identify abnormal user activity. InsightIDR integrates well with other Rapid7 solutions and popular third-party platforms, like AWS, Azure, and Cisco, to provide comprehensive coverage across diverse IT environments.
Pricing:
Pricing upon request
Pros:
- Advanced user behavior analytics
- Comprehensive incident detection and response capabilities
- Broad range of integrations
Cons:
- Pricing is not publicly disclosed
- Could be complex to set up for less tech-savvy users
- Some users report the need for frequent rule adjustments to avoid false positives
3. Cortex XDR - Best for unified threat detection and response across networks, clouds, and endpoints
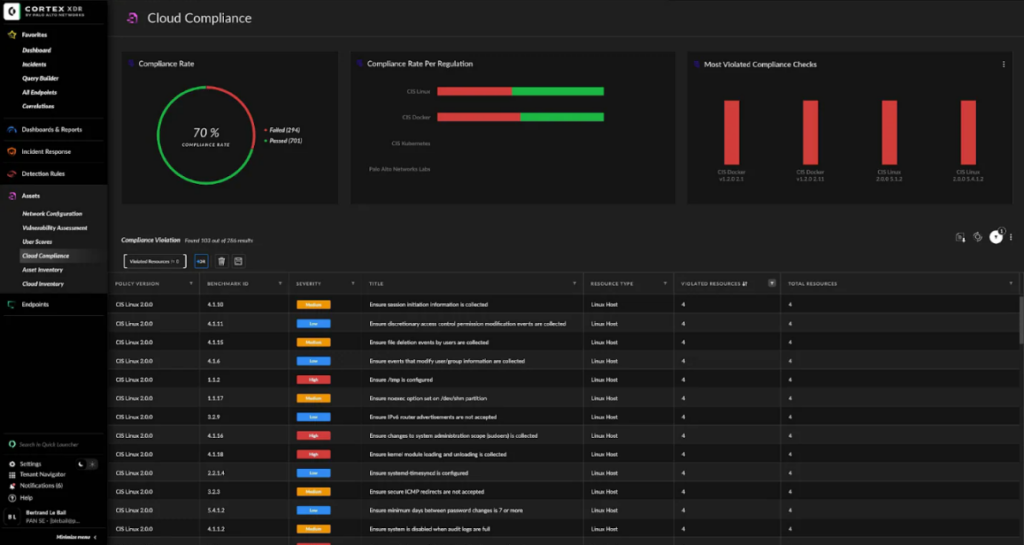
Cortex XDR is an extended detection and response platform that provides a unified approach to threat detection and response across networks, clouds, and endpoints. This cohesive security tool enables organizations to correlate data from diverse sources to detect complex threats, which aligns with its positioning as best for unified threat detection and response.
Why I Picked Cortex XDR:
I selected Cortex XDR for its integrated approach to security, capable of unifying threat detection and response across various environments. This comprehensive capability differentiates Cortex XDR from many security tools focusing on specific domains. I believe Cortex XDR is "best for unified threat detection and response across networks, clouds, and endpoints" due to its ability to correlate data across these sources, allowing for a holistic view of the organization's security posture.
Standout Features & Integrations:
Cortex XDR offers advanced features such as behavioral threat detection, automated security operations, and integrated case management. These features make it highly capable of detecting and responding to threats across diverse environments. As for integrations, Cortex XDR can be incorporated with a wide range of Palo Alto Networks products and other third-party solutions, which helps to enhance its security coverage.
Pricing:
Pricing upon request
Pros:
- Unified threat detection and response across various environments
- Advanced behavioral threat detection capabilities
- Comprehensive integrations with Palo Alto Networks products and other solutions
Cons:
- No publicly available pricing information
- May have a steep learning curve for users new to the platform
- Can be complex to deploy in large or heterogeneous environments
4. SentinelOne Singularity - Best for autonomous endpoint protection against all attack vectors
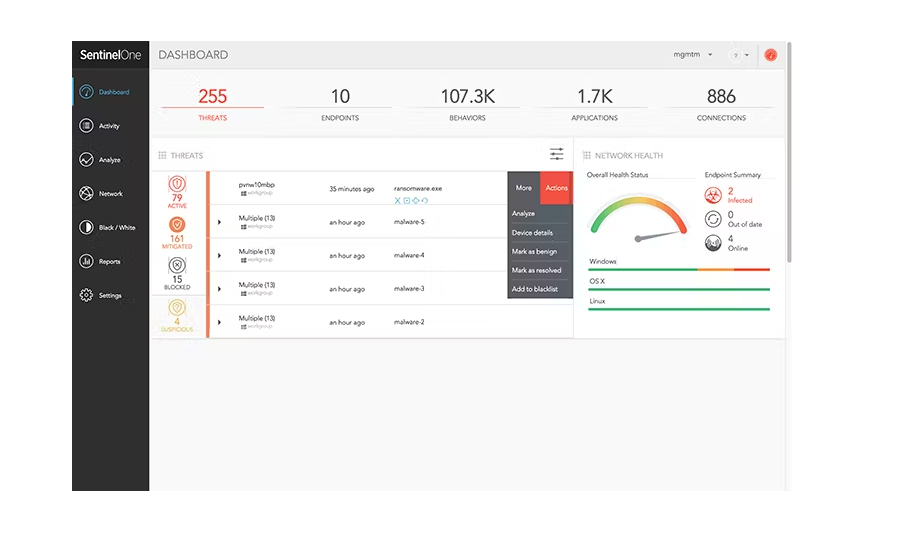
SentinelOne Singularity is an endpoint protection platform that leverages artificial intelligence to identify and mitigate threats. With a primary focus on providing autonomous endpoint security, SentinelOne Singularity positions itself as best for robust protection against all attack vectors.
Why I Picked SentinelOne Singularity:
I picked SentinelOne Singularity because of its strong focus on endpoint protection, backed by machine learning capabilities. Its emphasis on autonomous protection sets it apart from many other solutions in the market. Considering its capabilities, I believe SentinelOne Singularity is "best for autonomous endpoint protection against all attack vectors" because of its ability to automatically detect, respond to, and even prevent a wide range of threats.
Standout Features & Integrations:
Some of the key features of SentinelOne Singularity include active EDR (endpoint detection and response), autonomous AI, and IoT discovery. These features work together to provide a comprehensive, self-sufficient approach to endpoint protection. The platform offers integrations with leading solutions like Okta, AWS, and Azure, allowing businesses to extend their security posture to other critical parts of their infrastructure.
Pricing:
Pricing upon request
Pros:
- Autonomous endpoint protection against a wide range of threats
- Integrated AI for improved threat detection and response
- Broad range of integrations with leading solutions
Cons:
- Lack of transparency regarding pricing
- May require technical expertise to leverage all features
- The AI-driven approach might raise false positives
5. Cynet 360 AutoXDR - Best for automated threat discovery and response
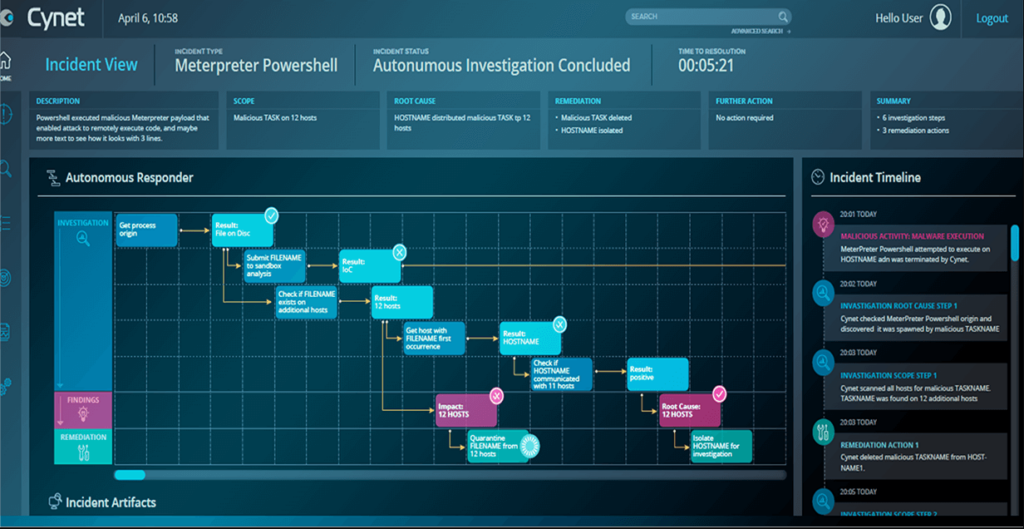
Cynet 360 AutoXDR is a cybersecurity solution that automates threat discovery and response, providing comprehensive coverage for endpoints, networks, and users. By incorporating machine learning and behavioral analysis, it seeks to identify and respond to threats swiftly and effectively, making it ideal for automated threat discovery and response.
Why I Picked Cynet 360 AutoXDR:
In making my selection, Cynet 360 AutoXDR stood out due to its high level of threat discovery and response automation, significantly reducing the manual work involved in these tasks. The product's inbuilt artificial intelligence gives it an edge in accurately identifying threats. It is best for automated threat discovery and response due to these qualities and the potential to minimize the time between a threat's discovery and its neutralization.
Standout Features & Integrations:
Cynet 360 AutoXDR's key features include advanced threat detection, automated response, and user behavior analytics. These collectively provide a rounded security solution that can identify threats, analyze user behavior for anomalies, and automatically execute responses. Cynet 360 AutoXDR is compatible with major IT systems for integrations, making it an adaptable solution for different IT environments.
Pricing:
Pricing upon request
Pros:
- High level of automation in threat discovery and response
- Comprehensive security coverage for endpoints, networks, and users
- Compatibility with major IT systems
Cons:
- Pricing details are not openly available
- High automation might limit manual control
- Might require technical expertise to fully harness its potential
6. Wiz - Best for multi-cloud visibility and security analytics
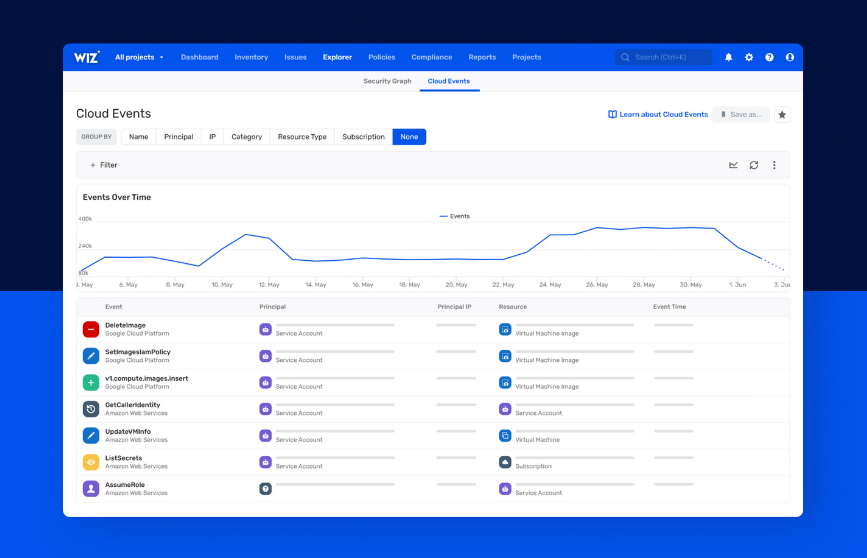
Wiz is a cloud security platform that delivers full-stack visibility and comprehensive security analytics across multiple cloud infrastructures. It aims to simplify cloud security by providing insights and identifying vulnerabilities in real-time, making it an optimal choice for teams requiring multi-cloud visibility and security analytics.
Why I Picked Wiz:
I picked Wiz for its innovative approach to multi-cloud visibility and security analytics. Its ability to provide deep insights into complex multi-cloud infrastructures sets it apart from many other tools on the market. In my opinion, Wiz is best suited for multi-cloud visibility and security analytics due to its robust security analysis capabilities and ease of use, especially when dealing with complex cloud architectures.
Standout Features & Integrations:
Wiz offers several standout features, including full-stack visibility, real-time vulnerability detection, and advanced security analytics. These features ensure a comprehensive and detailed view of the security landscape across multiple clouds. Wiz also integrates with major cloud platforms like AWS, Azure, and Google Cloud, along with many standard DevOps tools, providing an adaptable solution for diverse IT environments.
Pricing:
Pricing upon request
Pros:
- Comprehensive visibility across multiple clouds
- Real-time vulnerability detection
- Integration with major cloud and DevOps tools
Cons:
- Pricing details are not openly available
- May require a certain level of expertise to maximize its features
- As a focused tool, it may not cover all aspects of cybersecurity outside cloud environments
7. IBM Security QRadar SIEM - Best for large-scale threat management and forensic analysis
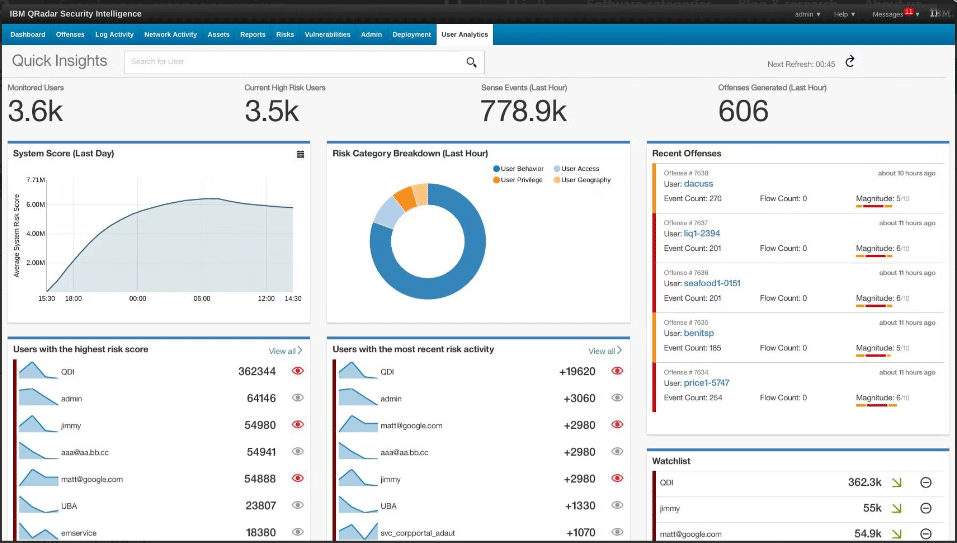
IBM Security QRadar SIEM is a security information and event management system that consolidates log events and network flow data from thousands of devices, endpoints, and applications distributed throughout a network. With its ability to correlate this information and identify potential threats, QRadar is best suited for large-scale threat management and forensic analysis.
Why I Picked IBM Security QRadar SIEM:
I selected IBM Security QRadar SIEM for its comprehensive threat detection and response capabilities, especially for large-scale environments. What sets QRadar apart is its ability to gather and correlate data from various sources, making it efficient for forensic analysis. Given its feature-rich platform and scalability, I believe QRadar is best for large-scale threat management and forensic analysis.
Standout Features & Integrations:
QRadar offers advanced threat detection, AI-powered insights, and extensive forensics capabilities. Its incident overview feature visually represents incidents, which can be invaluable during threat hunting. The system integrates with numerous IBM solutions and other third-party applications, broadening its reach across different facets of a network.
Pricing:
Pricing upon request
Pros:
- Robust threat detection and response capabilities
- Scalable to accommodate large-scale environments
- Extensive integrations with IBM solutions and other third-party applications
Cons:
- Pricing information isn't publicly available
- May require technical expertise to operate efficiently
- The user interface may be complex for some users
8. CrowdStrike Falcon Endpoint Protection Platform - Best for AI-driven protection against malware and ransomware
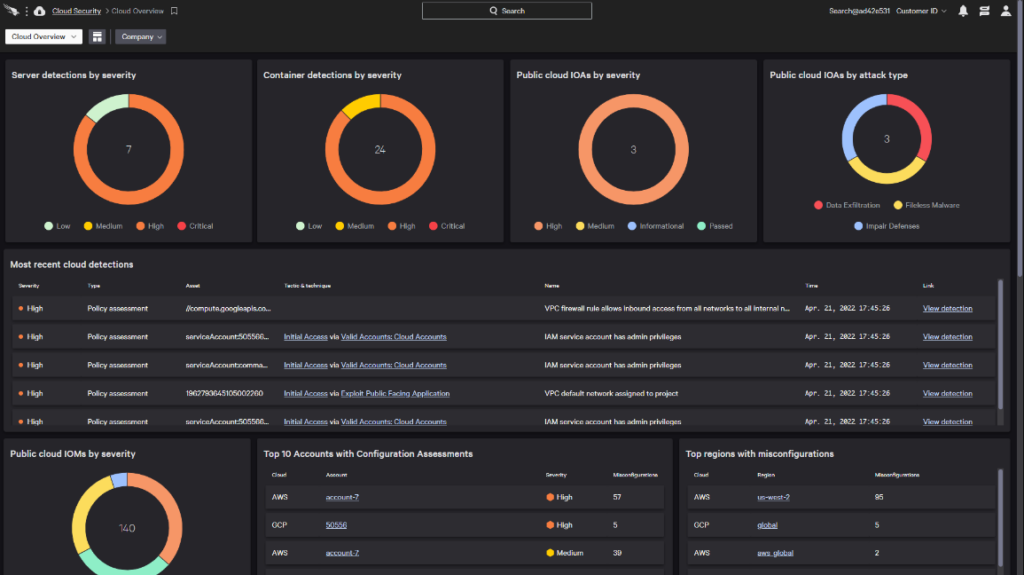
CrowdStrike Falcon Endpoint Protection Platform is a cloud-native solution designed to stop breaches by preventing and responding to all types of attacks. It employs AI to provide superior malware and ransomware protection, hence, it is the top choice for AI-driven protection against such threats.
Why I Picked CrowdStrike Falcon Endpoint Protection Platform:
I chose CrowdStrike Falcon because of its unique combination of technology, threat intelligence, and flexible response options. It stands out due to its AI capabilities, which enable superior malware and ransomware detection and prevention. Given these features, the tool is particularly adept at providing AI-driven protection against malware and ransomware.
Standout Features & Integrations:
Falcon offers features like AI-powered malware and ransomware protection, threat hunting, and comprehensive visibility across the IT environment. Its cloud-native architecture allows it to integrate well with other cloud-based systems and provides extensive APIs for custom integrations.
Pricing:
Pricing upon request
Pros:
- Advanced AI capabilities for malware and ransomware protection
- Extensive visibility across the IT environment
- Cloud-native solution offering scalability and ease of integration
Cons:
- Pricing information isn't publicly available
- May require technical expertise to fully leverage its features
- Some users have reported false positives with its detection system
9. Microsoft Defender for Cloud - Best for Azure-based environments needing threat protection

Microsoft Defender for Cloud is a security management tool that provides threat protection for workloads running in Azure, other clouds, and on-premises. It is designed for Azure environments and brings robust threat protection capabilities to these specific workspaces, making it ideal for such environments.
Why I Picked Microsoft Defender for Cloud:
In selecting Microsoft Defender for Cloud, I considered its native Azure integration and comprehensive threat protection features. This tool is ability to offer security management for Azure-based environments differentiates it. Therefore, it is the best option for Azure-based setups that require effective threat protection.
Standout Features & Integrations:
Microsoft Defender for Cloud offers continuous security assessment, advanced threat protection, and just-in-time access. Importantly, it natively integrates with Azure services, providing a unified security management experience.
Pricing:
Starting from $15/user/month (billed annually)
Pros:
- Native integration with Azure services
- Comprehensive threat protection
- Continuous security assessment capability
Cons:
- The tool is tailored to Azure, so it may not be as effective in non-Azure environments
- Pricing could be high for smaller teams or startups
- As a robust tool, it could have a steep learning curve for some users
10. Sophos Intercept X: Next-Gen Endpoint - Best for advanced endpoint protection with deep learning technology

Sophos Intercept X: Next-Gen Endpoint is a top-tier security tool leveraging deep learning technology for proactive threat detection and response. With its focus on utilizing advanced technologies for threat protection, it is particularly suitable for organizations needing sophisticated endpoint protection measures.
Why I Picked Sophos Intercept X: Next-Gen Endpoint:
I picked Sophos Intercept X for its remarkable utilization of deep learning in endpoint security. Its unique approach to endpoint protection, which involves the application of cutting-edge artificial intelligence technologies, set it apart in my selection process. Hence, I consider it to be the best for those in need of advanced endpoint protection powered by deep learning technology.
Standout Features & Integrations:
Sophos Intercept X provides critical features like exploit prevention, active adversary mitigation, and deep learning malware detection. It also integrates well with Sophos' suite of products and services, enabling a comprehensive security posture for organizations.
Pricing:
Starting from $20/user/month
Pros:
- Advanced deep learning technology for proactive threat detection
- Comprehensive suite of endpoint protection features
- Excellent integration with other Sophos products and services
Cons:
- Pricing might be a bit steep for smaller businesses
- The tool's advanced features could have a learning curve for some users
- While its deep learning approach is powerful, it might be overkill for businesses with simpler security needs
11. Trend Micro Vision One (XDR) - Best for risk visibility and correlated threat detection across different security layers
Trend Micro Vision One (XDR) offers extended detection and response solutions, providing high visibility and coordinated threat detection across various security layers. Given its ability to provide deep insight into potential risks and its excellent correlation capabilities, it fits organizations needing comprehensive risk visibility and threat correlation.
Why I Picked Trend Micro Vision One (XDR):
I selected Trend Micro Vision One due to its robust risk visibility and correlation features. It provides security insights across different layers, making it stand out from the pack. Therefore, it's best for those seeking to enhance their ability to detect correlated threats across different security layers.
Standout Features & Integrations:
Trend Micro Vision One offers advanced features like risk insight, prioritized alerts, and automated security operations. It integrates well with various platforms, including cloud infrastructures like AWS and Azure and endpoint platforms like Microsoft Defender.
Pricing:
From $25/user/month (billed annually)
Pros:
- Excellent risk visibility and correlation of threat detection
- Rich integration options with various platforms
- Advanced features like automated security operations
Cons:
- The cost might be high for smaller organizations
- Some users might find the platform complex due to its extensive features
- Lack of month-to-month billing option may not suit all businesses
12. Microsoft 365 Defender - Best for comprehensive protection across Microsoft 365 apps and services

Microsoft 365 Defender is a unified enterprise defense suite that provides comprehensive protection for all Microsoft 365 apps and services. Its extensive coverage across the Microsoft 365 ecosystem makes it especially suitable for organizations heavily using these services.
Why I Picked Microsoft 365 Defender:
I picked Microsoft 365 Defender because it offers a comprehensive, unified solution tailored explicitly for Microsoft 365 applications. Its standout characteristic is its integration and protection across the entire Microsoft 365 ecosystem. Therefore, I believe it's best for those requiring a robust defense mechanism, specifically for Microsoft 365 apps and services.
Standout Features & Integrations:
Microsoft 365 Defender offers automated threat investigation and remediation, advanced hunting for looking into security breaches, and threat analytics for insights into potential risks. It integrates perfectly with Microsoft 365 services, including Teams, SharePoint, and Exchange, enhancing the overall security profile of these applications.
Pricing:
From $20/user/month
Pros:
- Comprehensive protection across all Microsoft 365 services
- Advanced features like automated threat investigation and remediation
- Perfect integration with all Microsoft 365 apps
Cons:
- Might be overkill for organizations not heavily using Microsoft 365
- Pricing could be prohibitive for smaller organizations
- The learning curve could be steep for those unfamiliar with Microsoft 365 services
Other Noteworthy XDR Software
Below is a list of additional XDR software that I shortlisted but did not make it to the top 12. Definitely worth checking them out.
- VMware Carbon Black Cloud - Good for cloud-native endpoint protection
- CYREBRO - Good for centralized and simplified security operations
- LogRhythm SIEM - Good for detecting and responding to threats in real-time
- Bitdefender GravityZone - Good for small businesses needing robust security
- NetWitness Platform XDR - Good for comprehensive threat detection and response
- Armor Anywhere - Good for scalable and flexible cloud security
- Qomplx - Good for managing cybersecurity, risk, and insurance
- Symantec Storage Protection - Good for safeguarding cloud storage resources
- B1 Platform by CloudCover - Good for optimizing cloud costs and usage
- ContraForce - Good for leveraging machine learning in cyber threat detection
- Cybereason Defense Platform - Good for proactive protection against cyber threats
- Sophos Cloud Optix - Good for visibility and threat response in cloud environments
- Cisco SecureX - Good for integrated security across all defenses
- ESET Protect Elite - Good for multi-layered protection across devices and networks
- Prisma Cloud - Good for security and compliance across the entire DevOps lifecycle
Selection Criteria for Choosing XDR Software
When selecting endpoint security software, I hold specific criteria in high regard. I've tested each of these tools and, based on that hands-on experience, determined what makes some solutions stand out from the rest. After sifting through dozens of endpoint security tools, I specifically honed in on core functionality, key features, and usability.
Core Functionality
- Detect and Neutralize Threats: The tool should be able to identify both known and unknown threats and take immediate action to prevent damage.
- Real-time Monitoring: It should monitor the system for unusual activities that could signify a breach.
- Comprehensive Reports: The software should provide detailed reports on security incidents to help understand the threat landscape and improve the security posture.
Key Features
- Machine Learning Capabilities: These help the software to learn from previous attacks and adapt to prevent similar threats in the future.
- Integration with Other Security Tools: This ensures that the endpoint security solution can work in sync with the existing security infrastructure.
- Sandboxing: This feature allows suspicious files to be tested in an isolated environment to determine if they are a threat.
Usability
- User-friendly Interface: For this type of software, an interface that's easy to navigate is crucial, so administrators can quickly respond to threats.
- Comprehensive Training Resources: Given the complexity of endpoint security software, it should come with detailed guides, tutorials, or even a training program for onboarding users.
- Efficient Customer Support: Prompt and knowledgeable customer service is essential to resolve any technical issues that might arise.
Most Common Questions Regarding XDR Software (FAQs)
What are the benefits of using XDR software?
Extended Detection and Response (XDR) software offers several benefits to organizations. It provides comprehensive visibility across all endpoints, helping detect and respond to threats in real time. It utilizes machine learning and AI to learn from previous attacks and improve the defense against future threats. The software also integrates with existing security infrastructure for threat response. Additionally, XDR software simplifies security operations by consolidating various security products into one platform, reducing complexity and improving efficiency.
How much do these XDR tools typically cost?
The cost of XDR tools can vary widely depending on the specific features, the size of the organization, and the number of users. Some providers offer pricing on a per-user basis, while others may provide a flat fee for unlimited users.
What are the pricing models for XDR software?
Most XDR vendors offer subscription-based pricing, often with monthly or annual billing options. Some vendors might also offer volume discounts for larger organizations or longer-term contracts.
What is the typical range of pricing for XDR software?
Pricing for XDR software typically starts around $5 per user per month for basic plans and can go up to $50 or more per user per month for more comprehensive plans.
What is the cheapest and most expensive XDR software?
The pricing of XDR tools can vary significantly based on the features and the size of the organization. For instance, Microsoft 365 Defender is one of the more affordable options, with prices starting at $20/user/month. On the other hand, solutions like Trend Micro Vision One can be more expensive, with prices starting at around $50/user/per month.
Are there any free options for XDR software?
While free options are available for some security software types, XDR solutions typically do not offer a free version due to the complexity and advanced features they provide. However, many vendors offer free trials so you can evaluate the software before purchasing.
Other XDR Software-Related Reviews
Summary
To wrap up, XDR software is crucial in enhancing cybersecurity by offering real-time threat detection and response across all endpoints. Each software option comes with its unique set of features, integration capabilities, and pricing models, all of which should factor into your decision-making process.
Key takeaways:
- Define Your Needs: With various XDR tools available, it's vital to identify your specific requirements. Look for solutions aligning with your organization's size, industry, and security infrastructure.
- Consider the Key Features: While all XDR tools promise improved security, the provided features can vary. Core functionalities such as real-time threat detection, AI and machine learning capabilities, and deep integration with existing tools are crucial.
- Understand the Pricing Models: The cost of XDR software can range widely, and choosing a solution that fits within your budget without compromising on crucial features is essential. Remember to consider the immediate cost and the potential long-term value when evaluating options.
What do you think?
I hope you find this guide helpful in your quest for the best XDR software for your organization. Remember, the right solution can provide immense value in terms of security, productivity, and peace of mind. As cybersecurity continues to evolve, so too will these tools.
Your experiences and perspectives can enrich this discussion even further. So, if there are any tools that you believe should have made this list, I invite you to share them.
