12 Best Network Intrusion Detection Systems
After careful evaluation, I've curated the top 12 network intrusion detection systems to tackle major security concerns:
- Snort - Best for open-source enthusiasts
- Zeek - Best for comprehensive network analysis
- Security Onion - Best for integrated defense toolkit
- AlienVault OSSIM - Best for unified security management
- Darktrace - Best for AI-driven threat detection
- Corelight - Best for enterprises seeking scalability
- TippingPoint - Best for threat intelligence and response
- Symantec Network Security - Best for broad-based cybersecurity protection
- RSA NetWitness - Best for forensic investigation capabilities
- Vectra AI - Best for automated real-time attack detection
- Radware DefensePro - Best for DDoS attack mitigation
- CrowdStrike Falcon - Best for cloud-native cybersecurity protection
A network intrusion detection system (NIDS) is a comprehensive firewall that proactively monitors IP addresses and application layer traffic, detecting unauthorized access and potential cyberattacks.
With robust integration into operating systems and tools like OSSEC and antivirus software, it works in line to monitor both wired and wireless networks. Using packet sniffers, NIDS minimizes false positives while protecting sensitive data. Its logger function efficiently handles log files and is adaptable for on-premise or cloud usage.
Designed with a user-friendly interface, it allows quick remediation of data breaches, ensuring the integrity of your network. TLS and SSL ensure secure communication, while DNS aids in tracking network activities. This next-generation solution reduces the pain points of data breaches, unauthorized access, and constant false alarms.
What is a Network Intrusion Detection System
A network intrusion detection system (NIDS) serves as a vigilant guardian of network traffic, continuously monitoring and analyzing it for signs of intrusion or malicious activities. Utilizing a combination of signature-based, anomaly-based, and stateful protocol analysis, NIDS identifies potential threats and issues alerts when it detects suspicious activity.
It's a crucial tool used by organizations of all sizes, across various sectors, from healthcare and finance to e-commerce and government. They rely on NIDS to safeguard their digital environments, ensuring the integrity, confidentiality, and availability of their network and the valuable data it holds.
Overviews of the 12 Best Network Intrusion Detection System Tools
1. Snort - Best for open-source enthusiasts
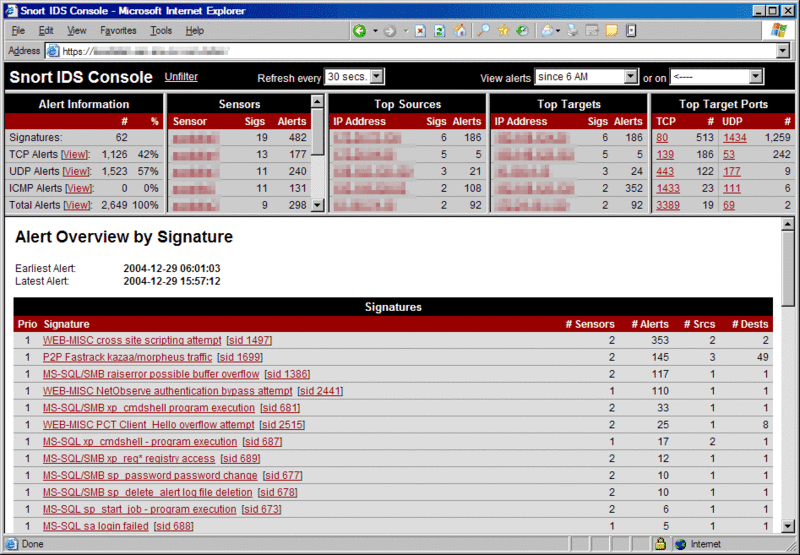
Snort is a robust open-source network intrusion detection system that inspects network traffic in real-time to detect potential threats. As an open-source tool, Snort offers flexible, customizable features that cater well to tech-savvy users who prefer hands-on control over their network security.
Why I Picked Snort:
I chose Snort because of its rich heritage and strong community support, making it a tried-and-true solution in the realm of open-source network security. Its openness means users have the freedom to tweak the system as they see fit, providing a level of customization that is hard to match. That's why I believe it is best for open-source enthusiasts who appreciate control and flexibility.
Standout Features & Integrations:
Snort boasts a rich array of features, including real-time traffic analysis and packet logging. It utilizes a variety of detection methods, such as signature, anomaly-based detection, and policy-based techniques, to provide comprehensive security. As for integrations, Snort benefits from its open-source nature, boasting compatibility with a wide range of other security tools. Its flexibility allows it to work well with systems like Security Onion and various SIEM systems for enhanced threat detection and response.
Pricing:
Snort itself is available for free as an open-source software. However, getting access to up-to-date rule sets comes with a cost. The Snort Subscriber Rule Set License starts from $29.99/year (billed annually).
Pros:
- Strong community support
- High level of customization
- Comprehensive detection methods
Cons:
- Steep learning curve for newcomers
- Requires manual setup and configuration
- Up-to-date rule sets come at a cost
2. Zeek - Best for comprehensive network analysis
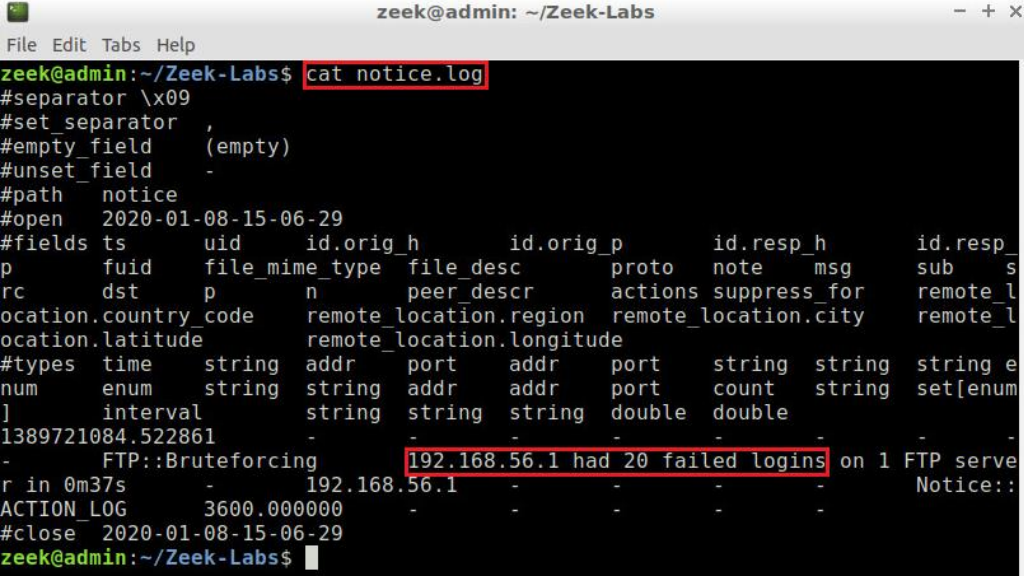
Zeek, formerly known as Bro, is an open-source network intrusion detection system that provides a high-powered platform for network traffic analysis. Its ability to transform raw network traffic into high-fidelity logs, files, and custom insights makes it an excellent choice for those looking for an in-depth understanding of their network.
Why I Picked Zeek:
When I was selecting tools, Zeek caught my eye due to its unique focus on transforming network traffic data into comprehensive, actionable information. This thorough analysis is the cornerstone of Zeek's capability, providing users with rich insights about their networks that many other NIDS don't offer. Therefore, I deem Zeek as best for comprehensive network analysis, given its superior data transformation capabilities.
Standout Features & Integrations:
Zeek's script interpreter is one of its most distinguishing features. It allows users to write scripts that guide the analysis of network traffic, providing unparalleled control over the process. Additionally, Zeek offers file extraction capabilities, further enhancing its analysis. As an open-source platform, Zeek can integrate with a variety of other tools. Most notably, it often pairs with ELK Stack for log management, enhancing its capabilities for thorough network analysis.
Pricing:
While Zeek's open-source software is available free of charge, they also offer enterprise-level support and training services. The pricing for these additional services is available upon request.
Pros:
- Rich, comprehensive network traffic analysis
- High flexibility through its scripting language
- Extracts files from network traffic for in-depth review
Cons:
- Requires technical expertise to use effectively
- No built-in GUI, relies on third-party tools
- Commercial support and training come at an additional cost
3. Security Onion - Best for integrated defense toolkit
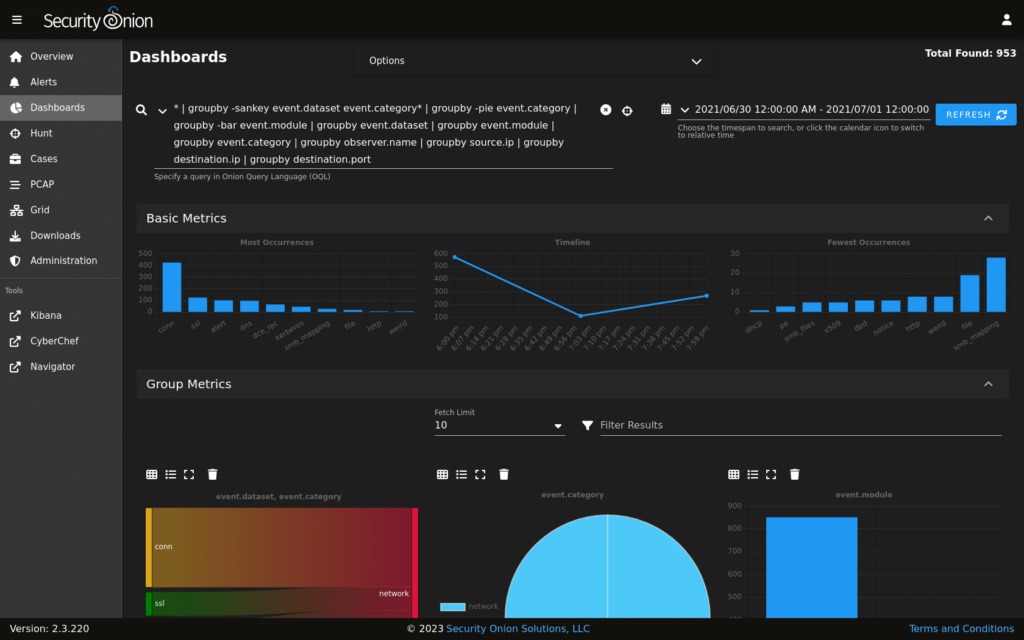
Security Onion is a Linux distro for intrusion detection, network security monitoring, and log management. It provides an all-in-one security system, packing various powerful tools into one package, thus forming an integrated defense toolkit perfect for organizations seeking a unified solution.
Why I Picked Security Onion:
Security Onion's comprehensive suite of security tools earned its spot on my list. It integrates several powerful open-source tools into a single platform, thus streamlining the network security process. With its holistic approach to network defense, it stands out as the best for anyone in need of an integrated defense toolkit.
Standout Features & Integrations:
Security Onion includes a wide range of tools like Elasticsearch, Logstash, Kibana, Suricata, Zeek (formerly known as Bro), Wazuh, and many others. This combination provides full packet capture, network-based and host-based intrusion detection systems, and robust log management. The integrated suite means that each tool within Security Onion can work seamlessly with the others, creating a cohesive and comprehensive security platform.
Pricing:
The open-source version of Security Onion is available free of charge. However, they offer additional services such as training, support, and hardware appliances, for which the pricing is available upon request.
Pros:
- Integrates multiple powerful security tools into one platform
- Covers full packet capture, NIDS, HIDS, and log management
- Strong community and commercial support available
Cons:
- Can be complex to set up and manage
- Potentially overwhelming for newcomers
- Advanced features and support require additional payment
4. AlienVault OSSIM - Best for unified security management
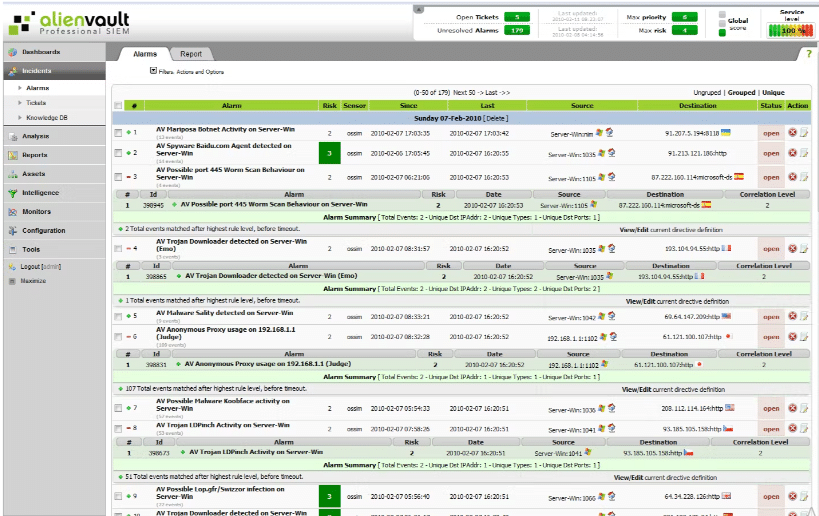
AlienVault OSSIM is an open-source security information and event management (SIEM) system that combines network visibility, log management, intrusion detection, and compliance into one unified platform. It's perfect for those seeking a centralized security platform to manage various security tasks simultaneously.
Why I Picked AlienVault OSSIM:
AlienVault OSSIM made my list because of its ability to merge diverse security technologies into a single, unified platform. It sets itself apart with a broad range of integrated security functionalities, including asset discovery, vulnerability assessment, and intrusion detection. Thus, it's best for organizations in need of unified security management.
Standout Features & Integrations:
AlienVault OSSIM stands out with its features, such as asset discovery, vulnerability assessment, and behavioral monitoring. Its integrated threat intelligence from AlienVault Labs and the AlienVault Open Threat Exchange (OTX) provides real-time information on emerging threats. As for integrations, it allows you to centralize data from existing security tools for better visibility and control.
Pricing:
AlienVault OSSIM is open-source and free to use. However, for additional capabilities and commercial support, AlienVault offers AlienVault USM, which is priced upon request.
Pros:
- Integrates multiple security functionalities into a single platform
- Provides real-time threat intelligence
- Centralizes data from multiple sources for better visibility
Cons:
- May require technical expertise to fully utilize
- Some advanced features only available in the paid version
- Commercial support costs extra
5. Darktrace - Best for AI-driven threat detection
Darktrace delivers enterprise-wide cyber defense through AI technology and machine learning. Its focus on providing organizations with self-learning AI allows for the detection of unusual network behavior and emerging threats, making it an ideal choice for proactive and AI-driven threat detection.
Why I Picked Darktrace:
In selecting Darktrace for this list, I considered its unique approach to threat detection, leveraging self-learning AI that adapts and learns from your network behavior. This autonomous response technology allows it to react to threats in seconds, making it a stand-out choice. In my opinion, Darktrace is "Best for..." AI-driven threat detection due to this focus on machine learning and quick response.
Standout Features & Integrations:
Darktrace's key features include its Enterprise Immune System, which learns normal 'patterns of life' to detect deviations indicative of a threat, and Darktrace Antigena, an AI response solution that reacts to in-progress cyber threats. Regarding integrations, Darktrace can work alongside your existing security tools, enhancing your defenses by integrating its AI-powered insight into other parts of your security ecosystem.
Pricing:
Darktrace's pricing model isn't publicly available. It's likely dependent on factors such as the size of your network and specific business needs.
Pros:
- Leverages self-learning AI for adaptive threat detection
- Autonomous response technology reacts to threats in real-time
- Can integrate with existing security tools
Cons:
- Pricing isn't transparent
- May have a steep learning curve for non-technical users
- Could be overkill for smaller organizations
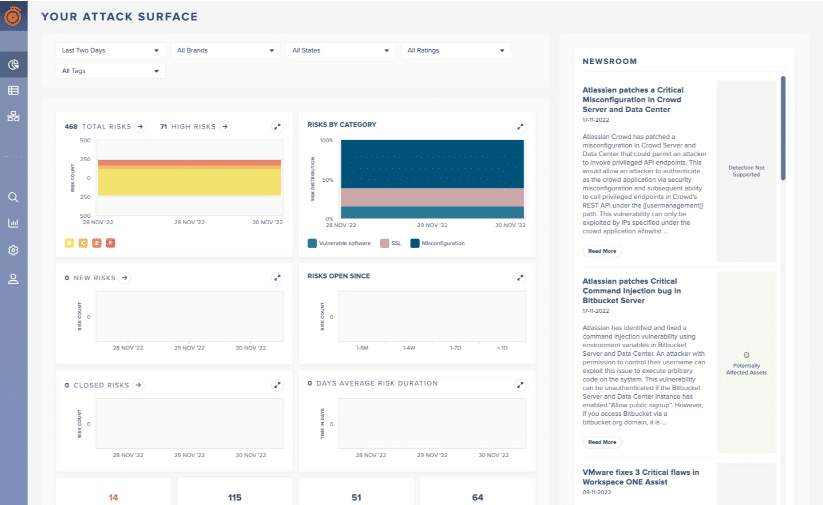
6. Corelight - Best for enterprises seeking scalability
Corelight delivers powerful network traffic analysis through its high-performance data-forwarding capabilities. With its comprehensive visibility and expansive scalability, Corelight is well-suited for large enterprises aiming for seamless network security scaling.
Why I Picked Corelight:
In choosing Corelight, I focused on its impressive scalability and robust network visibility. The ability to handle massive volumes of data and convert them into actionable insights sets it apart from many other tools. Given these attributes, I decided that Corelight stands out as the "Best for..." enterprises seeking scalability.
Standout Features & Integrations:
Corelight offers an extensive array of features, including real-time data streaming, comprehensive protocol coverage, and file extraction capabilities. It also provides robust integrations, such as compatibility with major SIEM platforms like Splunk and ELK Stack, allowing seamless data forwarding and analytics.
Pricing:
Corelight's pricing model isn't publicly disclosed, with costs likely to be tailored based on the specific requirements and scale of the business.
Pros:
- Offers extensive scalability for large enterprises
- Provides comprehensive visibility into network traffic
- Compatible with major SIEM platforms
Cons:
- Pricing information isn't publicly available
- Might be too complex for small organizations
- Could require technical expertise to operate effectively
7. TippingPoint - Best for threat intelligence and response
TippingPoint is a network security solution that focuses on providing a proactive approach to threat intelligence and response. With its advanced threat protection system, TippingPoint can identify, analyze, and react to potential threats in real time, making it an excellent choice for organizations prioritizing threat intelligence and response.
Why I Picked TippingPoint:
In my selection process, I was impressed by TippingPoint's robust capabilities in threat intelligence and response. Its proactive approach and real-time analysis stand out in the realm of network security. Considering these aspects, I firmly believe TippingPoint is the "Best for..." threat intelligence and response.
Standout Features & Integrations:
TippingPoint offers robust features like the Threat Protection System and the Digital Vaccine service for real-time threat intelligence. It integrates well with other security products from TrendMicro, providing an interconnected defense system.
Pricing:
TippingPoint pricing is not publicly disclosed, indicating that it could vary based on specific business needs and the scale of deployment.
Pros:
- Proactive approach to threat intelligence and response
- Integrates well with other TrendMicro products
- Real-time threat analysis and protection
Cons:
- Pricing information isn't publicly available
- Could have a steep learning curve for beginners
- Lack of integrations with non-TrendMicro products
8. Symantec Network Security - Best for broad-based cybersecurity protection
Symantec Network Security, a product by Broadcom, delivers a comprehensive set of cybersecurity solutions that secure the entirety of an enterprise's network. It offers a holistic approach to network security, making it optimal for organizations seeking broad-based cybersecurity protection.
Why I Picked Symantec Network Security:
During my evaluation, Symantec Network Security stood out due to its expansive, all-encompassing approach to cybersecurity. Unlike other solutions that may focus on specific aspects of security, Symantec provides a wide-ranging suite of tools for robust protection. With this comprehensive perspective in mind, I determined that Symantec Network Security is "Best for..." broad-based cybersecurity protection.
Standout features & integrations:
Symantec Network Security offers a broad array of features, including intrusion prevention, web filtering, and malware analysis. It's known for its integration capabilities with a wide variety of systems, enabling businesses to protect their existing infrastructure without major changes.
Pricing:
The exact pricing for Symantec Network Security is not publicly disclosed, which means it is likely to be customizable based on a business's specific needs and scale of deployment.
Pros:
- Offers a comprehensive set of cybersecurity solutions
- Seamless integration with a variety of systems
- Strong focus on both detection and prevention of threats
Cons:
- No public pricing information available
- May be overly complex for smaller organizations
- Integration with non-Broadcom products may require additional configuration
9. RSA NetWitness - Best for forensic investigation capabilities
RSA NetWitness is a threat detection and response platform that focuses on providing in-depth visibility across a network. Its forensic investigation tools allow enterprises to efficiently respond to threats, which is why it shines for businesses requiring sophisticated investigation capabilities.
Why I Picked RSA NetWitness:
I selected RSA NetWitness for its robust forensic investigation capabilities. The tool offers an array of features designed specifically for thorough threat investigation, distinguishing it from other network security solutions. Accordingly, I judged RSA NetWitness as the "Best for..." businesses in need of potent forensic investigation tools.
Standout features & integrations:
RSA NetWitness offers valuable features such as network forensics, endpoint detection, and automated threat responses. These features, when combined, provide a comprehensive view of the network's security landscape. Its notable integrations include RSA Archer for IT risk management and other third-party solutions like Splunk, FireEye, and Palo Alto Networks.
Pricing:
Exact pricing for RSA NetWitness is not directly provided, as it tends to be customized to each organization’s specific needs.
Pros:
- Exceptional forensic investigation capabilities
- Offers integrations with both RSA and third-party solutions
- Comprehensive feature set that includes network forensics and automated threat responses
Cons:
- Pricing is not publicly disclosed
- Could be complex for smaller organizations to utilize effectively
- The broad feature set may be more than what some businesses require
10. Vectra AI - Best for automated real-time attack detection
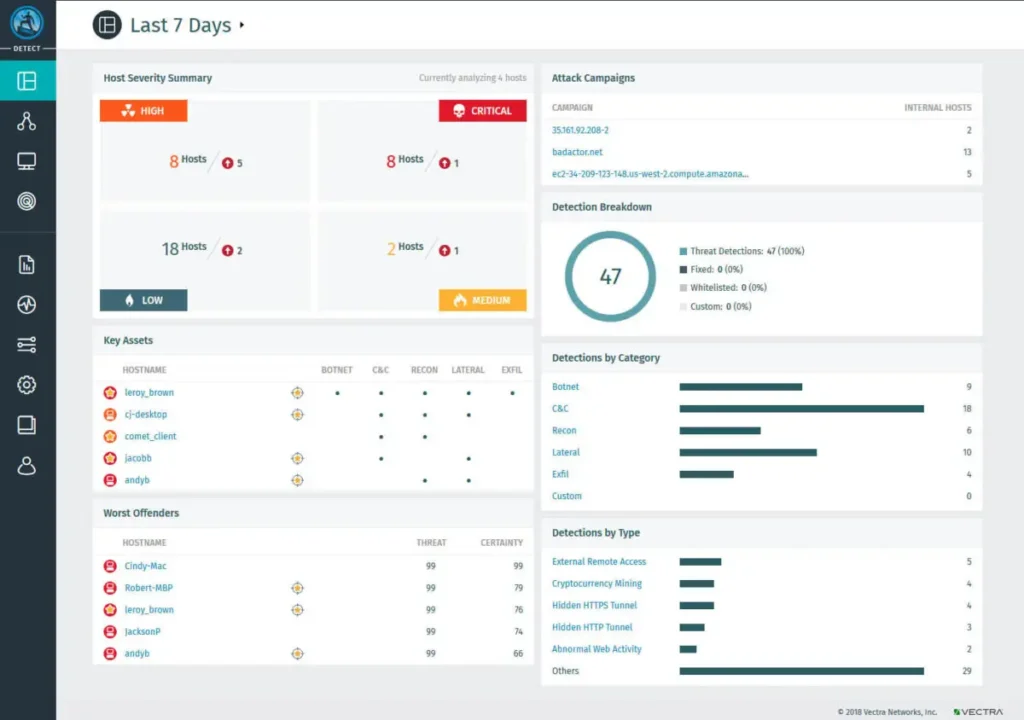
Vectra AI is a network detection and response (NDR) solution that harnesses artificial intelligence to identify and combat threats in real-time. Given its emphasis on automation and immediate threat identification, it stands as a prime choice for organizations seeking effective real-time attack detection.
Why I Picked Vectra AI:
I chose Vectra AI due to its strong focus on real-time, automated threat detection. The tool applies AI to detect anomalous network behavior promptly and automatically, which sets it apart in the field of network security tools. Thus, in my opinion, Vectra AI is "Best for..." organizations that prioritize swift, automated detection of potential threats.
Standout features & integrations:
Vectra AI's standout features include its real-time threat detection, AI-driven threat hunting, and its capability for automated response. It provides network-based detection, enriches security incidents with unique context, and offers robust reporting.
Importantly, Vectra AI integrates well with security information and event management (SIEM) solutions like Splunk, QRadar, and Chronicle, as well as endpoint detection and response (EDR) systems such as Crowdstrike and Carbon Black.
Pricing:
Vectra AI operates on a customized pricing model that varies based on the specific needs of the organization.
Pros:
- Robust real-time threat detection
- Utilizes AI for efficient threat hunting and response
- Provides valuable integrations with SIEM and EDR solutions
Cons:
- Pricing is not directly disclosed, which can be unclear for potential customers
- The tool's high level of automation might limit manual control
- Its comprehensive functionality may be overwhelming for small organizations
11. Radware DefensePro - Best for DDoS attack mitigation
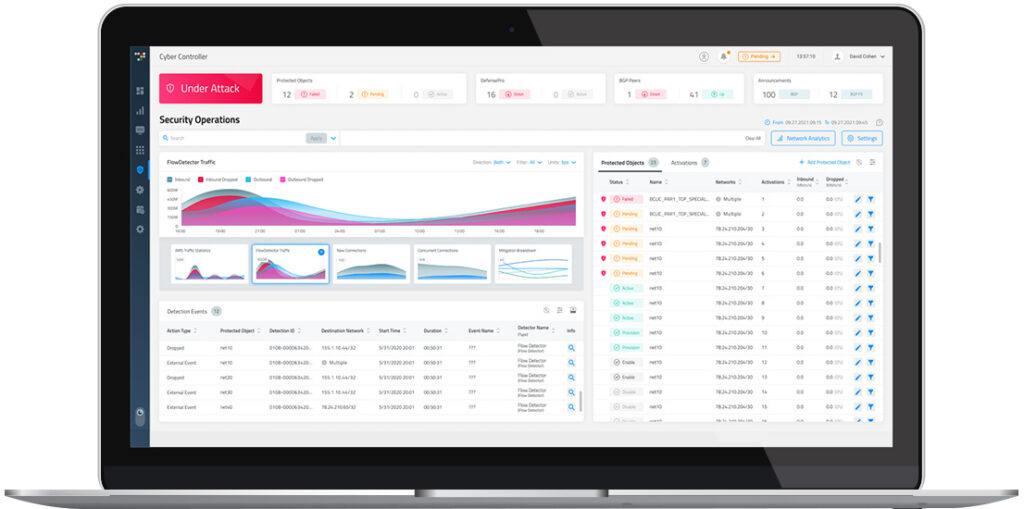
Radware DefensePro is a renowned cybersecurity solution that specializes in mitigating Distributed Denial of Service (DDoS) attacks. With its focus on ensuring uninterrupted service availability even under severe DDoS attacks, it earns its place as an optimal choice for organizations seeking dedicated DDoS protection.
Why I Picked Radware DefensePro:
I selected Radware DefensePro for its dedicated and robust approach to combating DDoS attacks. It has the ability to detect and mitigate multi-vector DDoS attacks in real time, which makes it distinct in the cybersecurity landscape. Therefore, based on my judgment, Radware DefensePro is the "Best for..." organization looking to ensure service availability during DDoS attacks.
Standout features & integrations:
Key features of Radware DefensePro include real-time DDoS attack detection, multi-layered protection, and machine-learning-powered threat analysis. The system’s ability to protect against a wide variety of attacks, from volumetric to encrypted attacks, is impressive. As for integrations, Radware DefensePro can be incorporated into a broader Radware security ecosystem, interfacing with tools such as Radware's Alteon and AppWall for a comprehensive security setup.
Pricing:
The pricing for Radware DefensePro is typically customized based on an organization's specific needs and requirements.
Pros:
- Dedicated protection against multi-vector DDoS attacks
- Real-time detection and mitigation of attacks
- Can integrate with other Radware security tools for a holistic data security approach
Cons:
- Pricing information is not transparently provided
- Could be over-specialized for organizations seeking a more general security solution
- Its comprehensive features may present a steep learning curve for users
12. CrowdStrike Falcon - Best for cloud-native cybersecurity protection
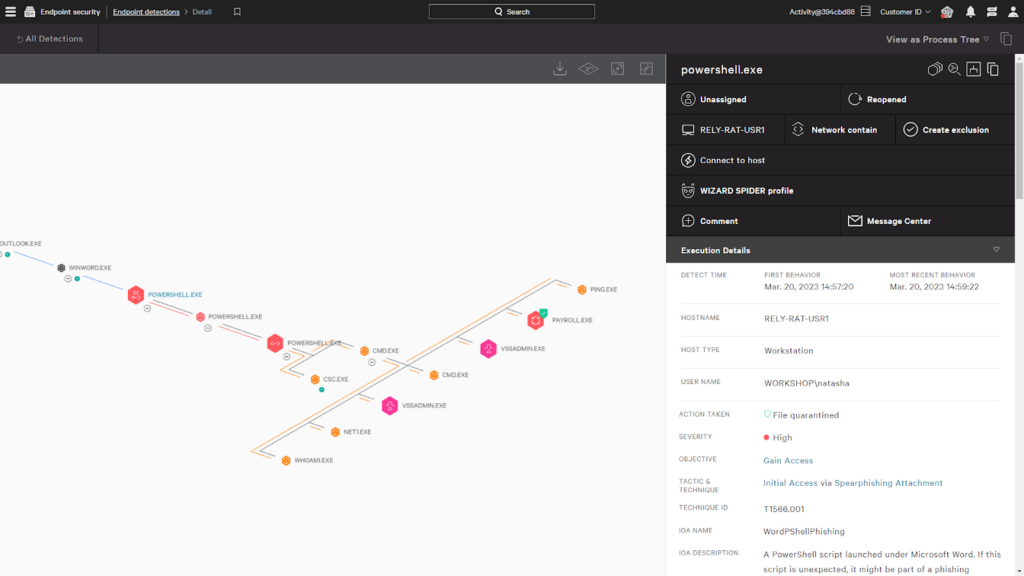
CrowdStrike Falcon is a cybersecurity platform designed to provide comprehensive cloud-native protection. With the ability to safeguard cloud-based infrastructures from various cyber threats, CrowdStrike Falcon is the ideal choice for organizations prioritizing robust, cloud-native cybersecurity defenses.
Why I Picked CrowdStrike Falcon:
I selected CrowdStrike Falcon because it demonstrates a strong focus on cloud-native protection. The tool's ability to leverage the power of AI to detect and respond to threats in real-time places it in a unique position compared to other cybersecurity solutions. Hence, it is my determined opinion that CrowdStrike Falcon is the "Best for..." cloud-native cybersecurity protection.
Standout features & integrations:
Among the most significant features of CrowdStrike Falcon are its artificial intelligence-based threat detection, real-time threat response, and comprehensive visibility across cloud networks. It also boasts a cloud-based architecture, making it scalable and easy to deploy. In terms of integrations, CrowdStrike Falcon can connect with a variety of platforms and tools, including major cloud providers like AWS, GCP, and Azure, as well as SIEM solutions and IT operations tools.
Pricing:
The pricing for CrowdStrike Falcon starts from $8.99/user/month (billed annually).
Pros:
- Comprehensive cloud-native protection
- AI-powered real-time threat detection and response
- Integrates with a wide variety of platforms and tools
Cons:
- Pricing can be high for small to mid-size organizations
- Requires annual commitment for pricing
- May require advanced technical knowledge for effective use
Other Network Intrusion Detection System Tools
Below is a list of additional network intrusion detection system tools that I shortlisted but did not make it to the top 12. Definitely worth checking them out.
- VM-Ware NXS - Good for multi-cloud networking and security
- WatchGuard Firebox - Good for unified security platform management
- Network Detective Pro - Good for network risk assessment and management
- Cynet 360 - Good for advanced threat detection and response
- Inspection Support Network - Good for business management in inspection industries
- PRTG Network Monitor - Good for comprehensive network monitoring and fault detection
Selection Criteria
Having worked with numerous cybersecurity tools, I have accumulated a wealth of experience in identifying the most effective solutions. I have tested each of the tools mentioned, and my favorites are based on rigorous evaluation in the context of real-world scenarios.
Core Functionality
When assessing cybersecurity software, the following core functions should be in place:
- Threat Detection: The software should be able to identify possible threats to a network or system in real time.
- Incident Response: Once a threat has been detected, the software should be able to respond quickly to minimize potential damage.
- Vulnerability Assessment: The software should be capable of performing regular checks on the network to identify any weaknesses that could be exploited by hackers.
Key Features
There are several key features to look for in cybersecurity tools:
- Automated Alerts: These allow IT teams to respond promptly to threats. The alerts should be detailed, providing actionable information about the nature of the threat and its location.
- User Behavior Analytics: This uses machine learning to identify normal and abnormal behavior within your network, making it easier to spot malicious activities.
- Integration: The software should be able to integrate with existing systems and tools to provide comprehensive coverage and streamline workflows.
Usability
The design and ease of use of cybersecurity tools can significantly impact their effectiveness:
- Intuitive Interface: The software should be easy to navigate, with key information clearly displayed. The interface should allow users to quickly access different features and perform various actions without requiring deep technical knowledge.
- Effective Onboarding: Onboarding should be swift, with guidance offered via tutorials or customer support to help users understand how to get the most from the tool.
- Customer Support: Access to reliable, prompt, and knowledgeable customer support is essential. This ensures that any issues or questions that arise can be dealt with quickly, reducing downtime and maintaining the tool's effectiveness.
People Also Ask (FAQs)
What are the benefits of using Network Intrusion Detection System (NIDS) tools?
NIDS tools offer various advantages, including real-time detection of harmful network activities for swift mitigation, and they use advanced algorithms and machine learning for improved accuracy. They provide automated alerts for timely threat responses and integrate well with existing systems. Additionally, they help maintain regulatory compliance as some industries require their use for protecting sensitive data.
How much do NIDS tools typically cost?
The cost of NIDS tools can vary widely depending on the vendor, the features included, and the organization's size or network they're protecting. Some vendors offer pricing on a per-user basis, while others might charge based on the size of the network or the amount of data processed. Prices can range from as low as $20 per month per user to several thousands of dollars per year for enterprise-scale solutions.
What are the typical pricing models for NIDS tools?
NIDS tools often use subscription-based pricing models, where customers pay a monthly or yearly fee to use the software. These fees usually cover customer support and regular updates to the software. Some vendors may also offer a perpetual license model, where customers make a one-time payment to use the software indefinitely. This latter model typically involves additional fees for support and updates.
What is the cheapest NIDS tool available?
As of my last update, the cheapest NIDS tool with solid functionality is Snort, which is open-source and free-to-use software.
What is the most expensive NIDS tool available?
Pricing information for some NIDS tools isn't always publicly available as they offer custom quotes based on the specific needs of an organization. However, tools such as FireEye Network Security are known to be on the higher end of the pricing scale, costing several thousands of dollars annually.
Are there any free NIDS tools available?
Yes, there are free NIDS tools available. As mentioned earlier, Snort is one of the most well-known and widely-used free NIDS tools. It's open-source, which means it's freely available for anyone to use and modify. However, it's worth noting that free tools may not offer the same level of support or features as paid solutions.
Other Related Network Software Reviews
Summary
In conclusion, selecting the best network intrusion detection system involves careful consideration of several critical factors. It's not merely about picking the most popular tool but choosing the one that offers the functionality and features most suited to your specific needs and context.
Key Takeaway 1: Understand Your Needs - It's crucial to grasp the specific demands of your use case. Do you require real-time threat detection, robust forensic capabilities, or superior DDoS mitigation? Different tools excel in different areas, making a clear understanding of your requirements vital for the best choice.
Key Takeaway 2: Consider Usability and Support - User experience matters significantly in this field. The tools should not only offer robust functionality but also be intuitive to use, making onboarding easier. Furthermore, solid customer support can make a huge difference, especially in scenarios where immediate response is necessary.
Key Takeaway 3: Pricing Models and Budget - Various tools have different pricing models, with some providing a subscription service while others require a one-time fee. Understand these models and align your choice with your budget. However, remember that the most expensive tool isn't necessarily the best. Value for money is key, and sometimes, even less costly options can provide excellent service.
What Do You Think?
I’ve done my best to compile a comprehensive list, but I know that the cybersecurity landscape is constantly evolving, and there may be other excellent network intrusion detection systems out there that I've missed.
If you have any recommendations or think there's a tool I should take a look at, please let me know in the comments. I’m always open to suggestions and appreciate your input!
