12 Best Privileged Access Management Solutions Shortlist
After careful evaluation, I've curated the 12 best privileged access management solutions to fill the gaps in your tech security. Let's dive in!
- Broadcom - Best for integrated IT infrastructure
- Wallix - Best for real-time monitoring and control
- One Identity - Best for mitigating insider threats
- StrongDM - Best for privileged session management
- BeyondTrust - Best for extensive threat analytics
- Nokia - Best for large-scale network environments
- Auth0 - Best for seamless user experience
- SailPoint - Best for access risk management
- CyberArk - Best for its comprehensive solution suite
- Keeper Security - Best for small to mid-sized businesses
- ManageEngine PAM360 - Best for its 360-degree security approach
- Delinea - Best for efficient privilege management
As someone deeply involved in IT, I understand the crucial role that privileged access management solutions play in managing and securing privileged credentials. With an ever-growing attack surface due to the proliferation of endpoint devices, SaaS applications, and APIs, managing access becomes a pivotal part of ensuring your IT environment is secure. I've personally felt the reassurance that comes from knowing a solution like Centrify can implement the principle of least privilege, manage service accounts, and secure SSH keys effectively.
I trust that by taking a look at the software solutions I recommend, you'll find the right tool to manage access for your end users and applications on MAC or any platform, because I've been there, and I know what works.
What Are Privileged Access Management Solutions?
Privileged access management solutions are a vital component of an organization's cybersecurity framework, designed to control, manage, and monitor privileged user access to critical systems and data. These solutions are extensively employed by businesses of all sizes - from small start-ups to global corporations, IT administrators, security teams, and virtually anyone responsible for safeguarding sensitive digital assets.
I've experienced how these solutions significantly reduce the risk of security breaches by implementing a zero trust model and enforcing the least privilege. The ability to perform just-in-time privileged access, combined with MFA for secure access, is a game-changer for IT teams. I've seen firsthand how these tools ease the pain of privileged account management, remediation, and the lifecycle of identity access management (IAM). So when Gartner suggests endpoint privilege management, I've been in the trenches and understand why it's essential to safeguard against threats like malware.
The primary objective of these tools is to protect information systems from potential threats, including data breaches and other cyber attacks, by ensuring that access to sensitive data is limited to authorized personnel, thereby reducing the risk of unauthorized access and misuse. They not only offer robust security but also streamline the process of managing privileges, making them an indispensable tool in today's digital age.
Overviews of the 12 Best Privileged Access Management Solutions
1. Broadcom - Best for integrated IT infrastructure
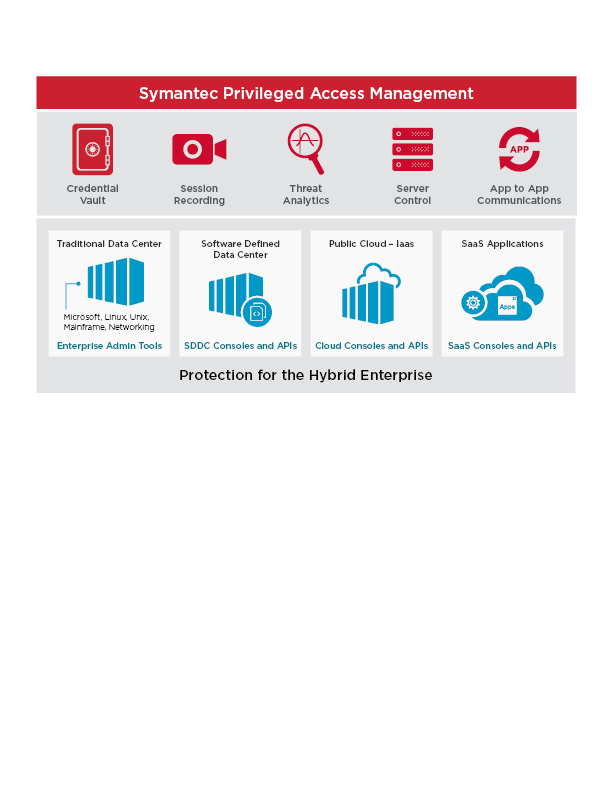
Broadcom's privileged access management solution brings to the table a versatile, scalable approach to IT security. Primarily, it provides an integrated framework that supports an extensive range of IT infrastructures. This aspect makes it stand out, aligning perfectly with organizations seeking cohesive solutions for complex, multi-layered IT setups.
Why I Picked Broadcom:
I selected Broadcom for its adaptability and seamless integration into diverse IT landscapes. In comparison to other tools, Broadcom demonstrates a unique capability to handle a variety of infrastructures. When it comes to IT environments with multiple layers and complexities, I firmly believe Broadcom fits the bill as the "best for integrated IT infrastructure".
Standout Features & Integrations:
Broadcom shines in its capacity to deliver role-based access control, extensive auditing, and session recording. It enables organizations to manage privileged accounts while ensuring a secure environment.
Its integration capacity is equally impressive, with the ability to seamlessly sync with many other software like ServiceNow, making it a perfect fit for organizations operating on diverse platforms.
Pricing:
Pricing upon request
Pros:
- Offers an integrated solution for complex IT infrastructures
- Provides role-based access control
- Offers comprehensive auditing and session recording
Cons:
- Pricing information is not readily available
- Might be overwhelming for small businesses with simpler IT structures
- Learning curve may be steep for those unfamiliar with integrated solutions
2. Wallix - Best for real-time monitoring and control
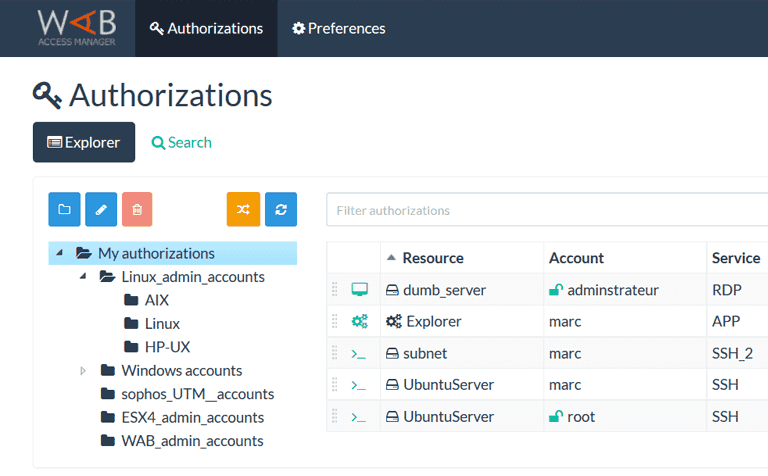
Wallix offers a robust privileged access management solution, designed to maintain a watchful eye on your system's access points. It prides itself on its real-time monitoring capabilities, providing granular control over every privileged session.
Why I Picked Wallix:
In comparing and weighing various tools, I found Wallix to possess exceptional strength in real-time monitoring and control. It stands apart from others with its swift response to potential threats and a keen focus on active control.
Its capacity to provide real-time surveillance and in-depth control, in my judgment, makes Wallix the "best for real-time monitoring and control."
Standout Features & Integrations:
Key features of Wallix include real-time alerting, session shadowing, and granular access control. These features ensure immediate response to potential threats and effective management of privileged sessions. As for integrations, Wallix smoothly cooperates with key IT solutions such as ITSM tools and SIEMs, enhancing its functionality and ease of use.
Pricing:
Pricing upon request
Pros:
- Offers real-time alerting and session shadowing
- Provides granular control over privileged sessions
- Integrates smoothly with key IT solutions
Cons:
- Pricing information is not readily available
- Might require technical expertise to fully exploit its capabilities
- Smaller businesses might find the features overwhelming
3. One Identity - Best for mitigating insider threats
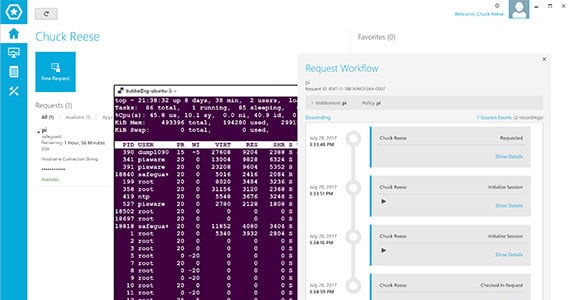
One Identity brings a laser-focused approach to managing and monitoring privileged access, designed to tackle internal threats head-on. With an emphasis on preventing unauthorized internal access, One Identity truly excels in mitigating insider threats.
Why I Picked One Identity:
I chose One Identity because of its strength in handling potential internal threats. When I assessed and compared different tools, One Identity stood out for its exceptional focus on managing insider risks.
It is my strong opinion that this tool is "best for mitigating insider threats" due to its in-depth approach to managing and monitoring internal accesses.
Standout Features & Integrations:
One Identity's key features include advanced behavioral analytics, real-time alerts, and a secure vault for storing sensitive credentials. These features help to detect abnormal user behavior and prevent potential internal breaches. It integrates seamlessly with a wide variety of systems, databases, applications, and cloud environments, providing a comprehensive solution for your security needs.
Pricing:
Pricing upon request
Pros:
- Advanced behavioural analytics to detect potential insider threats
- Provides real-time alerts on suspicious activities
- Integrates with various systems, databases, applications and cloud environments
Cons:
- Pricing information is not publicly available
- It may require a certain level of technical expertise to fully exploit its features
- Smaller companies may find the platform to be more advanced than needed
4. StrongDM - Best for privileged session management
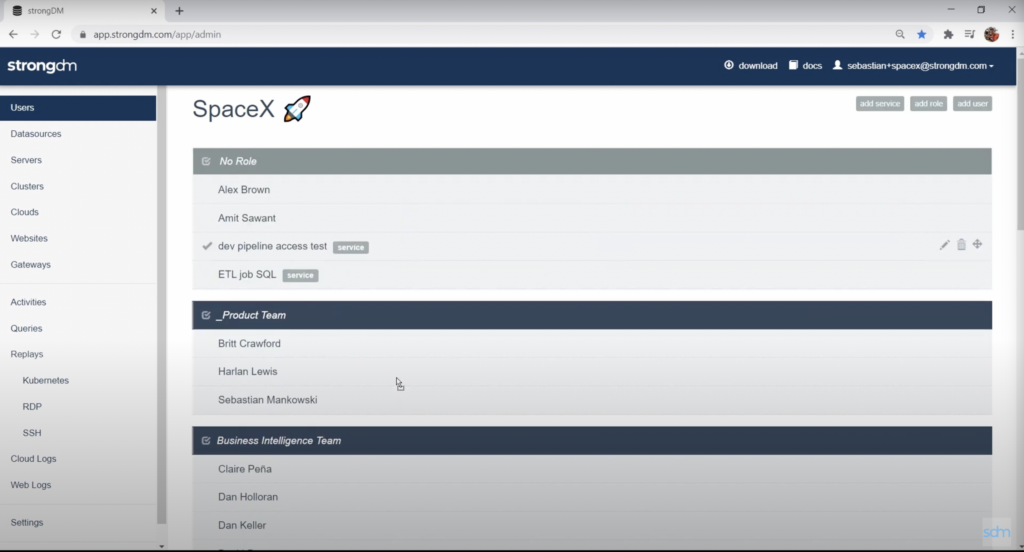
StrongDM acts as a single access point for your entire infrastructure, managing and auditing all access and permissions. Its main strength lies in its exemplary privileged session management, making it a standout in that regard.
Why I Picked StrongDM:
In the course of my assessment, I selected StrongDM for its superior capabilities in managing privileged sessions. Comparatively, it provides an unparalleled combination of control, visibility, and ease of use in session management. I deem StrongDM as "best for privileged session management" because it focuses on session control, not just access control.
Standout Features & Integrations:
StrongDM's standout features include granular permissions, real-time session control, and comprehensive audit trails, providing full visibility over privileged sessions. This tool also impresses with its broad range of integrations. It supports a variety of protocols and integrates with popular Identity Providers, configuration management databases, and notification tools, among others.
Pricing:
From $50/user/month
Pros:
- Granular permissions provide detailed control over user access
- Offers real-time session management and comprehensive audit trails
- Wide range of integrations with other software platforms
Cons:
- The starting price point may be higher than other tools in the market
- The interface could be overwhelming for less technical users
- Extensive features may be more than what smaller teams require
5. BeyondTrust - Best for extensive threat analytics
BeyondTrust is a comprehensive privileged access management solution that offers privileged password and session management, secure remote access, and vulnerability management. Its edge lies in delivering extensive threat analytics, which significantly enhances its ability to mitigate potential security risks.
Why I Picked BeyondTrust:
I chose BeyondTrust as part of this list because of its prowess in the area of threat analytics. Its ability to provide granular insights sets it apart from other solutions. Based on my evaluation, BeyondTrust qualifies as the "best for extensive threat analytics" as it offers an exceptional level of detail in threat detection and monitoring, which is critical in today's cybersecurity landscape.
Standout Features & Integrations:
BeyondTrust's features such as advanced reporting, dashboarding capabilities, and real-time analytics are truly noteworthy. These contribute to providing an in-depth analysis of potential threats. BeyondTrust also offers integrations with a broad array of systems and applications, ranging from ITSM tools like ServiceNow to SIEM solutions like Splunk, further enhancing its utility.
Pricing:
From $50/user/month (billed annually)
Pros:
- Advanced threat analytics capability provides extensive insights
- Broad integration with various systems and applications
- Robust reporting and dashboarding features
Cons:
- Higher starting price point may deter smaller organizations
- The learning curve might be steep for non-technical users
- The configuration process can be complex for some setups
6. Nokia - Best for large-scale network environments
Nokia offers a Privileged Access Security solution designed to manage, control, and monitor privileged access in network environments. What makes this tool highly effective is its ability to scale and handle the complexity inherent in large network environments, thereby setting a high standard in terms of capability and performance.
Why I Picked Nokia:
I selected Nokia for this list because of its proven efficiency in managing vast and complex network environments. Its resilience, coupled with the capability to scale, is what makes it stand out.
Given these characteristics, I believe Nokia is the "best for large-scale network environments" as it's designed to efficiently manage and monitor privileged access in highly intricate and large-scale networks.
Standout Features & Integrations:
Key features of Nokia include privileged user and password management, role-based access control, and audit trail capabilities. It also provides advanced security features such as threat detection and response. As for integrations, Nokia works seamlessly with other Nokia network management and security solutions, thereby providing a comprehensive and unified approach to network security.
Pricing:
Pricing upon request
Pros:
- Highly scalable, ideal for large-scale network environments
- Advanced security features for threat detection and response
- Works well with other Nokia network management and security solutions
Cons:
- Pricing information is not readily available
- The platform might be overkill for smaller network environments
- Limited third-party integrations as compared to other tools
7. Auth0 - Best for seamless user experience
Auth0 provides identity management solutions that focus on providing a simplified and streamlined user experience. This platform integrates with numerous systems and applications, offering a unified login experience that enhances user satisfaction while maintaining high levels of security.
Why I Picked Auth0:
Auth0 found its way to my selection due to its emphasis on user experience. It provides an interface that is intuitive and straightforward, making it easier for users to manage their credentials.
I identified Auth0 as the "Best for seamless user experience" because it simplifies the often complex process of identity management while ensuring a user-friendly approach.
Standout Features & Integrations:
Auth0 comes with features such as Single Sign-On (SSO), multifactor authentication, and breach password detection. Its Universal Login feature stands out as it allows a uniform and consistent login experience across various applications and platforms.
In terms of integrations, Auth0 connects with a wide range of applications including Salesforce, Slack, Zoom, and more, allowing users to maintain a consistent identity across multiple platforms.
Pricing:
Pricing for Auth0 starts from $23/user/month (billed annually).
Pros:
- User-friendly interface that enhances user experience
- Universal Login feature provides consistent login across platforms
- Wide range of integrations with popular applications
Cons:
- May be costly for smaller organizations
- Configuration can be complex for certain use cases
- Limited features in the lower pricing tiers
8. SailPoint - Best for access risk management
SailPoint provides a comprehensive identity management platform that includes access risk management features. By leveraging artificial intelligence to automate and streamline access-related tasks, SailPoint helps organizations identify and mitigate risks associated with user access.
Why I Picked SailPoint:
When selecting SailPoint, I was drawn to its robust capabilities in managing access risk, a critical aspect in today's cyber landscape. The platform's ability to analyze and manage access-related risks sets it apart from its competitors, thus my reasoning for deeming it as the "Best for access risk management".
SailPoint's advanced analytics and intelligent insights enable it to preemptively address access risk before it translates into a real threat.
Standout Features & Integrations:
SailPoint's features include automated access certification, policy management, and password management. However, its risk-based approach to identity governance stands out, using AI and machine learning to identify and manage risks.
SailPoint integrates seamlessly with platforms such as Microsoft Azure, AWS, and Google Cloud, providing robust identity governance across diverse IT environments.
Pricing:
SailPoint's pricing starts from $10/user/month (billed annually).
Pros:
- Strong focus on access risk management
- AI-powered risk analysis capabilities
- Robust integrations with popular cloud platforms
Cons:
- Higher price point compared to some competitors
- The interface may seem complex for some users
- Customization might require technical knowledge
9. CyberArk - Best for its comprehensive solution suite
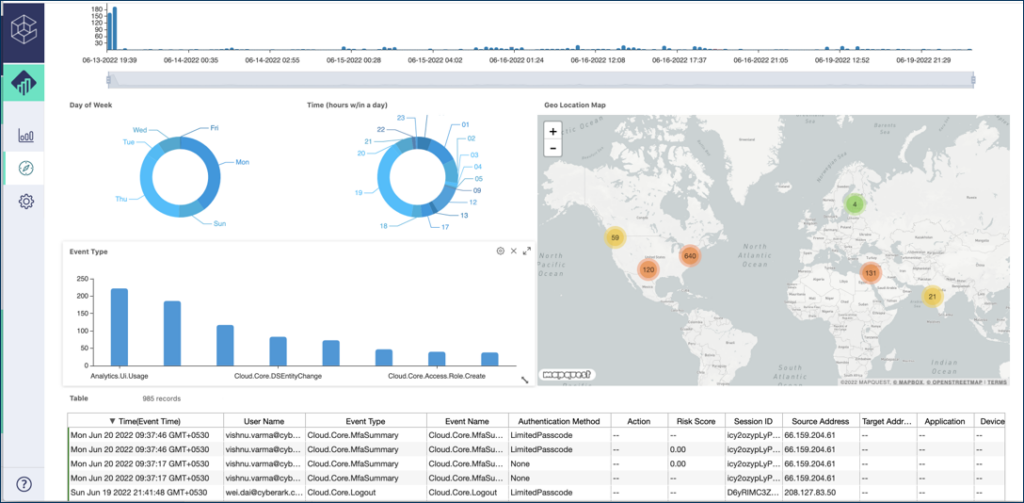
CyberArk is an established name in the field of privileged access management, offering a vast suite of solutions aimed at securing businesses across multiple platforms and environments. Its comprehensive nature ensures that organizations can manage, control, and monitor privileged accounts, thereby minimizing potential security vulnerabilities.
Why I Picked CyberArk:
I selected CyberArk for this list due to its broad range of offerings that together constitute a comprehensive solution suite. This holistic approach sets CyberArk apart, making it well-suited to companies looking for an encompassing platform rather than piecemeal solutions.
This breadth of features and services is why I believe CyberArk to be the "Best for its comprehensive solution suite."
Standout Features & Integrations:
CyberArk's features extend from privileged account discovery, provisioning, and de-provisioning to session isolation, monitoring, and threat analytics. Its privilege cloud stands out as a significant offering, providing privileged access security as a service. CyberArk integrates with a host of applications and platforms, including Windows, Unix/Linux, databases, virtual environments, and network devices.
Pricing:
Pricing for CyberArk begins from $10/user/month (billed annually).
Pros:
- Comprehensive suite of privileged access management tools
- Strong emphasis on threat analytics
- Extensive range of integrations
Cons:
- The user interface could be more intuitive
- Pricing might be steep for smaller organizations
- The setup process can be complex
10. Keeper Security - Best for small to mid-sized businesses
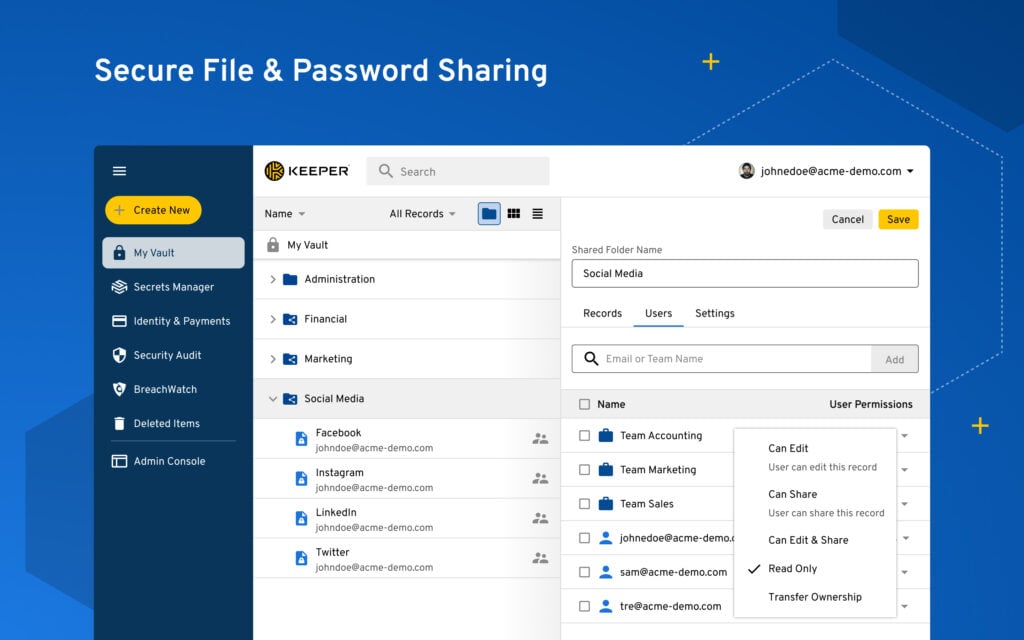
Keeper Security is a robust password management and digital vault solution that aids in creating, storing, and managing passwords securely. The simplicity of its design combined with a feature-rich environment makes it an optimal choice for small to mid-sized businesses.
Why I Picked Keeper Security:
I chose Keeper Security for this list because of its simplicity and versatility which I believe are well-aligned with the needs of smaller businesses. Its capability to easily manage and secure digital credentials, as well as its straightforward setup and maintenance processes, separates it from the crowd.
Therefore, Keeper Security rightfully takes the spot of "Best for small to mid-sized businesses."
Standout Features & Integrations:
Keeper Security offers a set of features like secure record sharing, a password generator, a digital vault, and secure file storage. It also provides a feature called BreachWatch, which continuously scans the dark web for compromised credentials. Its integrations include popular platforms such as Google Drive, Dropbox, and Slack, thereby increasing its usability across different work environments.
Pricing:
Pricing for Keeper Security starts from $3.75/user/month (billed annually).
Pros:
- Intuitive user interface and easy setup
- Strong encryption standards for enhanced security
- BreachWatch feature provides an additional layer of security
Cons:
- Advanced features come with higher-priced tiers
- Lacks some of the more comprehensive features found in other tools
- Customer support has room for improvement
11. ManageEngine PAM360 - Best for its 360-degree security approach
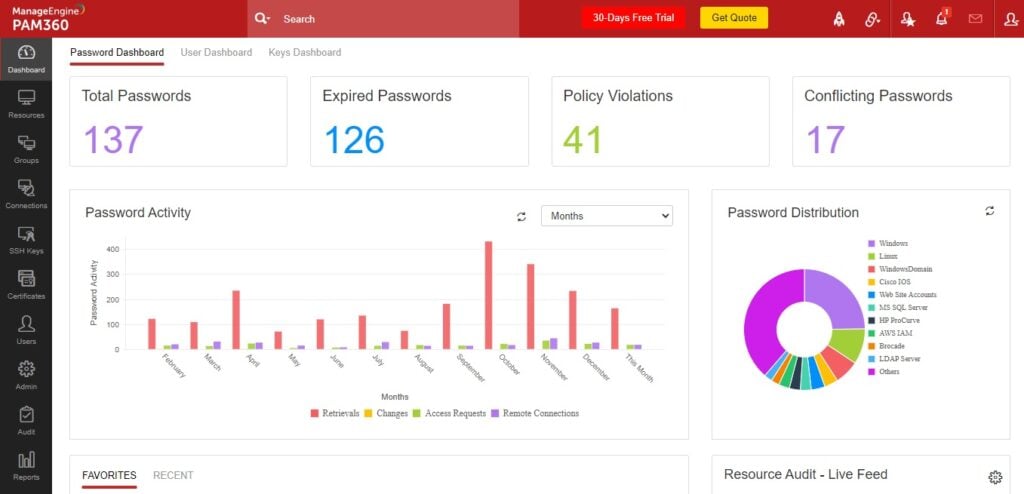
ManageEngine PAM360 is a comprehensive privileged access security solution that focuses on offering complete visibility and control over privileged accounts. Its 360-degree approach ensures a well-rounded security strategy, making it ideal for businesses wanting to fortify their defenses at all levels.
Why I Picked ManageEngine PAM360:
I selected ManageEngine PAM360 for its all-encompassing security strategy. This platform goes beyond standard access management, offering holistic visibility and control over privileged accounts.
I believe its unique approach to security, covering all corners, makes it the top choice for organizations wanting a 360-degree security solution.
Standout Features & Integrations:
Some of ManageEngine PAM360's notable features include password management, remote session management, and access control based on roles. It also boasts of an AI-powered anomaly detection engine that identifies and mitigates potential risks. Integrations with systems like Active Directory, SIEM solutions, and ticketing systems expand its capabilities and fit into various IT environments.
Pricing:
ManageEngine PAM360's pricing starts from $7.95/user/month (billed annually).
Pros:
- Offers a comprehensive suite of security tools
- AI-powered anomaly detection for proactive risk mitigation
- Strong integrations with popular IT management systems
Cons:
- The user interface might be complex for beginners
- Reporting features could be more robust
- Higher pricing compared to some other tools in the market
12. Delinea - Best for efficient privilege management
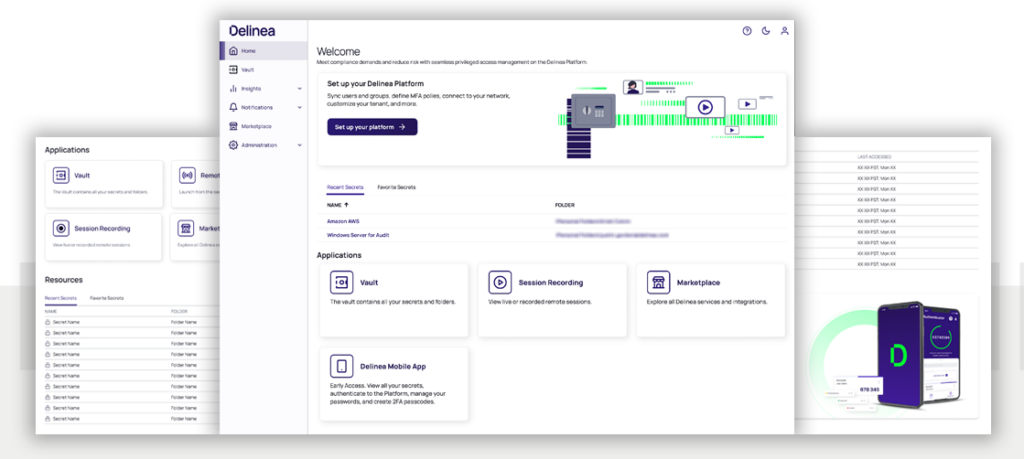
Delinea is a security software platform designed to help organizations manage privileged access. This platform streamlines the management of privileges in an organization's IT environment, making it a top choice for businesses aiming for efficient privilege management.
Why I Picked Delinea:
In my assessment, I selected Delinea due to its strong focus on efficient privilege management. This software's ability to streamline privilege management and reduce potential access risks distinguishes it from other solutions in the market.
Hence, I hold the view that it's the most appropriate choice for businesses seeking optimal efficiency in managing privileged access.
Standout Features & Integrations:
Key features of Delinea include comprehensive visibility into privileged access, automated privilege elevation, and rotation, as well as advanced session monitoring capabilities. Its integration with third-party IT management and security tools like SIEM solutions, ITSM tools, and vulnerability scanners further enhances its capabilities.
Pricing:
Pricing for Delinea starts at $10/user/month (billed annually).
Pros:
- Comprehensive visibility into privileged access
- Efficient management of user privileges
- Strong integrations with popular IT management systems
Cons:
- The learning curve might be steep for some users
- Pricing could be on the higher end for smaller businesses
- Limited options for customizability
Other Privileged Access Management Solutions
Below is a list of additional privileged access management solutions that I shortlisted, but did not make it to the top 12. Definitely worth checking them out.
- Microsoft Entra Verified ID - Good for leveraging the Microsoft ecosystem for identity verification
- JumpCloud - Good for comprehensive device management across different operating systems
- Workato - Good for secure integration and automation with AWS Secrets Manager
- IBM Security Verify Privilege - Good for implementing risk-based session monitoring
- Azure AD (Microsoft Entra ID) - Good for seamless integration with Microsoft services
- Ekran - Good for video recording of privileged sessions
- Idency - Good for integration with Thycotic Secret Server on-premise
- PrivX - Good for lean and scalable privilege management
- Arcon - Good for maintaining IT security governance
- Osirium PAM - Good for securing privileged IT tasks
- Okta - Good for identity management in large organizations
- Omada - Good for robust Identity Governance and Administration
- SafeNet Trusted Access - Good for cloud-based access management
- Silverfort - Good for risk-based multi-factor authentication
- Duo - Good for user-friendly two-factor authentication
Selection Criteria For the Best Privileged Access Management Solutions
In my experience of evaluating and testing numerous privileged access management (PAM) solutions, there were several key criteria that really mattered when choosing the best software in this field. I've tried out over 20 tools, focusing particularly on functionality, features, and usability specific to privileged access management.
Core Functionality
Privileged access management tools should allow for:
- Privilege Elevation: Granting elevated access rights to users on a need-to-have basis.
- Session Monitoring: Overseeing privileged sessions for potential security threats.
- Access Control: Regulating who has access to what, based on roles and responsibilities.
- Password Vaulting: Secure storage and management of privileged credentials.
Key Features
When it comes to PAM solutions, the following features stand out:
- Multi-factor Authentication: An additional layer of security where users are required to provide two or more verification factors to gain access.
- Risk-Based Analytics: Real-time risk assessment based on user behavior and access patterns.
- Integration Capabilities: Ability to integrate with various other systems for broader access control.
- Audit Trails: Detailed logs of all privileged sessions for compliance and investigation purposes.
Usability
For a PAM solution, usability refers to:
- Intuitive UI: Given the complex nature of privileged access, the UI should be straightforward, allowing admins to easily assign and manage access rights.
- Smooth Onboarding: The solution should provide comprehensive guidance for new users, especially given the security implications of incorrect setup.
- Efficient Customer Support: The vendor should offer reliable customer support for any issues or questions that arise.
- Configurable Role-based Access: An important feature for employee management, the tool should allow easy configuration of access rights based on roles.
- Training Program: Considering the complexity of enterprise solutions, a learning library or training program for onboarding users would be advantageous.
People Also Ask
What are the benefits of using Privileged Access Management (PAM) solutions?
Privileged access management solutions provide numerous benefits including:
- Enhanced Security: They prevent unauthorized access and mitigate risks associated with privileged accounts, thus enhancing overall security.
- Compliance Assurance: These tools provide detailed audit trails and reporting capabilities to ensure compliance with various regulations.
- Improved Efficiency: Automating privileged access management frees up resources and reduces the risk of human error.
- Risk Analysis: PAM solutions can identify suspicious behavior and provide real-time risk analysis to prevent potential breaches.
- Integration Capabilities: They can integrate with existing systems, offering broader access control and streamlining various processes.
How much do Privileged Access Management tools typically cost?
Pricing for privileged access management tools can vary significantly based on the complexity of the tool, the number of users, and the specific features offered. The cost can range anywhere from around $5 per user per month for more basic solutions, up to several hundred dollars per user per month for advanced, enterprise-level tools.
What are the typical pricing models for these tools?
The most common pricing models for PAM tools are subscription-based, typically charged on a per-user, per-month basis. Some vendors offer tiered pricing models with varying levels of features and functionality. Others may charge a flat rate for a certain number of users or privileges.
Which are the cheapest and most expensive PAM software?
The cheapest PAM solution featured in this list is Microsoft Azure AD, which starts at $6/user/month. The most expensive software is typically enterprise-level solutions like CyberArk, which can run into several hundred dollars per user per month.
Are there any free Privileged Access Management solutions?
While there are few completely free PAM solutions, several providers do offer limited free versions or free trials of their software. These can be a good way to evaluate a tool’s capabilities before committing to a full, paid subscription. It's also worth noting that open-source solutions like OpenIAM are available, but they require more technical expertise to implement and maintain.
Other Cybersecurity Software Reviews
Summary
In summary, selecting the right privileged access management (PAM) solution is a critical decision for businesses of all sizes. PAM tools offer enhanced security by preventing unauthorized access, mitigating risk associated with privileged accounts, and ensuring compliance.
They vary in features, integrations, usability, and pricing, so it's essential to consider your specific needs and budget when making a choice.
Here are three key takeaways from this buyer's guide to assist in your decision-making process:
- Identify Your Needs: Determine your organization's specific requirements for privileged access management. Consider factors like the number of users, the level of access control required, and the integrations needed with other systems.
- Evaluate Features and Usability: Look for PAM solutions that offer the core functionalities and features needed for your use case. Ease of use, a clean user interface, and strong customer support are also important considerations.
- Consider Pricing Carefully: PAM tools come with various pricing models. Understand the total cost of ownership, considering not just the base price but also potential additional costs for setup, integrations, or scaling up as your business grows. It's also worth exploring free trials or free versions to evaluate a tool before committing to a purchase.
What Do You Think?
While this guide offers a comprehensive overview of some top privileged access management solutions, there are undoubtedly other notable tools out there that I may have missed. I invite you to share your experiences or suggest other PAM tools in the comments section below. Your insights can greatly benefit others in their journey toward finding the perfect PAM tool for their
