Best Encryption Software Shortlist
After extensive analysis, I’ve handpicked the 12 best encryption software, summarizing the main use case or feature it’s best for:
With so many different encryption software available, figuring out which is right for you is tough. You know you want to facilitate your app development process, but need to figure out which tool is best to help you out. I've got you! In this post I'll help make your choice easy, sharing my personal experiences using dozens of different drag-and-drop app builders with large teams and projects, with my picks of the best drag-and-drop app builders.
Why Trust Our Encryption Software Reviews
We’ve been testing and reviewing encryption software since 2023. As IT specialists ourselves, we know how critical and difficult it is to make the right decision when selecting software.
We invest in deep research to help our audience make better software purchasing decisions. We’ve tested more than 2,000 tools for different IT use cases and written over 1,000 comprehensive software reviews. Learn how we stay transparent & our hybrid cloud solution review methodology.
Best Encryption Software Summary
| Tools | Price | |
|---|---|---|
| 1Password | From $2.99/user/month | Website |
| Keeper Security | Keeper Security's pricing starts from $2.91/user/month, billed annually. | Website |
| ESET PROTECT Complete | Pricing upon request | Website |
| Boxcryptor | From $3/user/month, billed annually | Website |
| NordLocker | From $3.99/user/month, billed annually | Website |
| GnuPG (GNU Privacy Guard) | GnuPG is completely free, aligning with its open-source principles. | Website |
| Rohos Disk Encryption | starting price of $35/user as a one-time fee. | Website |
| Sophos SafeGuard Encryption | Pricing information for Sophos SafeGuard Encryption is not readily available on their website. For detailed pricing information, it is recommended to contact Sophos directly. | Website |
| 7-Zip | 7-Zip is open-source software and is free for users. | Website |
| Secure IT | starting price of $29.95 | Website |
| CryptoForge | offers a one-time payment option at $39.70 per user | Website |
| Kruptos 2 Professional | priced at $10.99 for a single-user license (one-time fee). | Website |

Compare Software Specs Side by Side
Use our comparison chart to review and evaluate software specs side-by-side.
Compare SoftwareHow To Choose an Encryption Software
As you're shortlisting, trialing, and selecting encryption software, consider the following:
- What problem are you trying to solve - Start by identifying the encryption feature gap you're trying to fill to clarify the features and functionality the tool needs to provide.
- Who will need to use it - To evaluate cost and requirements, consider who'll be using the platform and how many licenses you'll need. You'll need to evaluate if it'll just be the IT team, or the whole organization that will require access. When that's clear, it's worth considering if you're prioritizing ease of use for all, or speed for your technical power users.
- What other tools it needs to work with - Clarify what tools you're replacing, what tools are staying, and the tools you'll need to integrate with. This could include your existing security infrastructure, various data sources, and your overall tech stack. You might also need to decide if the tools will need to integrate together, or alternatively, if you can replace multiple tools with one consolidated encryption software.
- What outcomes are important - Consider the result that the tool needs to deliver to be considered a success. Think about what capability you want to gain, or what you want to improve, and how you will be measuring success. You could compare encryption software features until you’re blue in the face, but if you aren’t thinking about the outcomes you want to drive, you could be wasting a lot of valuable time.
- How it would work within your organization - Consider the solutions alongside your workflows and security protocols. Evaluate what's working well, and the areas that are causing issues that need to be addressed. Remember every business is different — don’t assume that because a tool is popular that it'll work in your organization.
Best Encryption Software Reviews
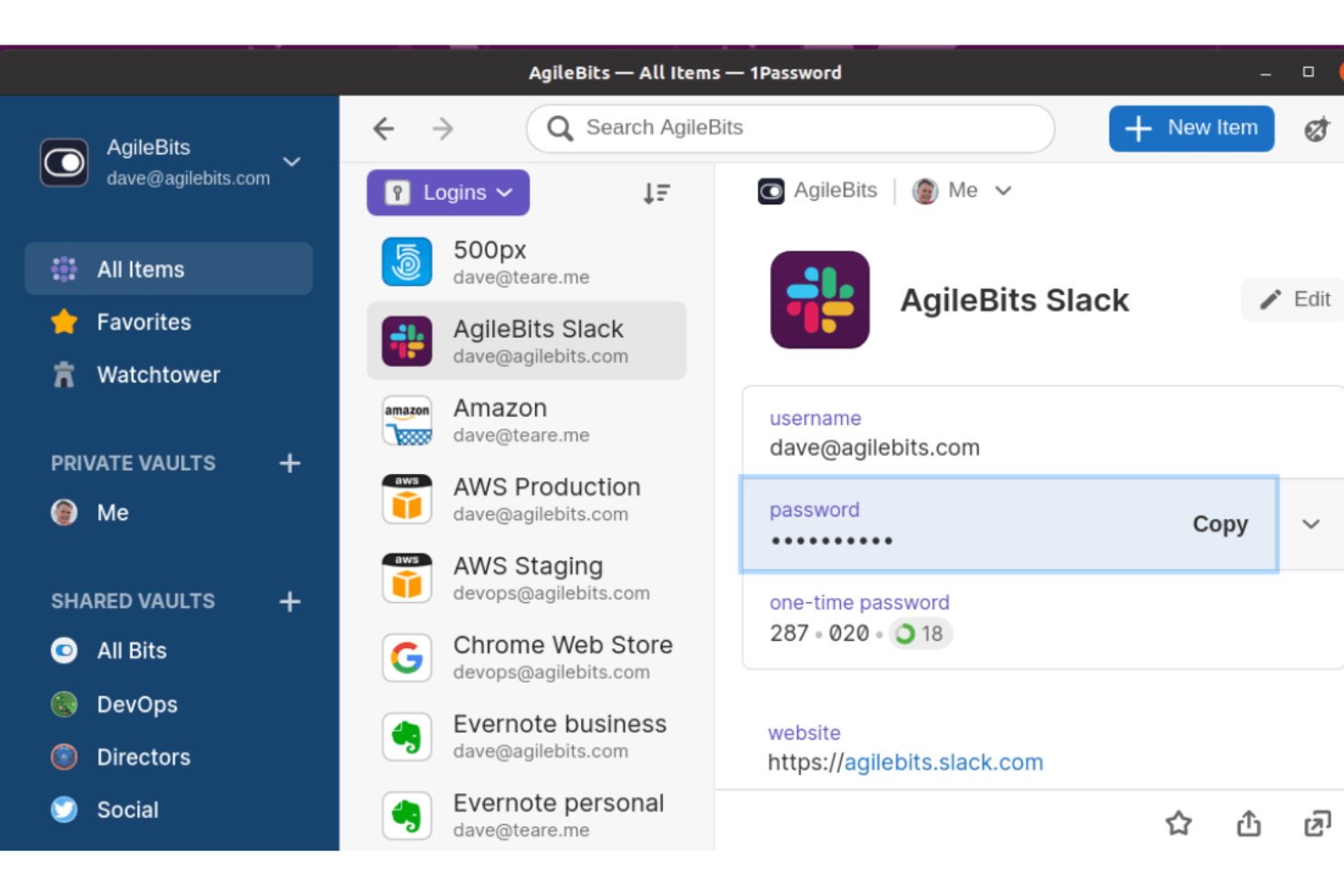
1Password is a password manager that helps users securely store and manage their passwords and other sensitive information. It can generate strong, unique passwords for each site or service and store them in an encrypted format. Users can then access their passwords and other data, like credit card information and secure notes, by using a single master password.
Why I Picked 1Password: 1Password utilizes ES-256-bit encryption, a standard widely recognized and used by the U.S. government for securing top-level classified information. This robust security framework ensures that all stored data, from passwords to secure notes, remains protected against hacking attempts and breaches. Additionally, 1Password's watchtower service enhances its security credentials by actively monitoring for password breaches or security vulnerabilities, alerting users immediately when action is needed.
1Password Complete Standout Features and Integrations
Features include unobtrusive background updates, sensitive document storage, smart suggestions, secure sharing, and data recovery in the event of a power outage or interruption. 1Password also offers cross-platform compatibility for seamless synchronization between iOS, Android, Windows, and Mac devices, which means you can access your information wherever you go.
Integrations include Okta, Azure, OneLogin, Google Workspace, Slack, GitLab, Splunk, Datadog, Duo, JumpCloud, Elastic, Panther, Sumo Logic, Kubernetes, Ansible, Go, Node, Python, and more.
Pros and cons
Pros:
- AES 256-bit encryption
- Automatic form filling
- Sync between devices
Cons:
- Limited availability of customer support
- No free plan
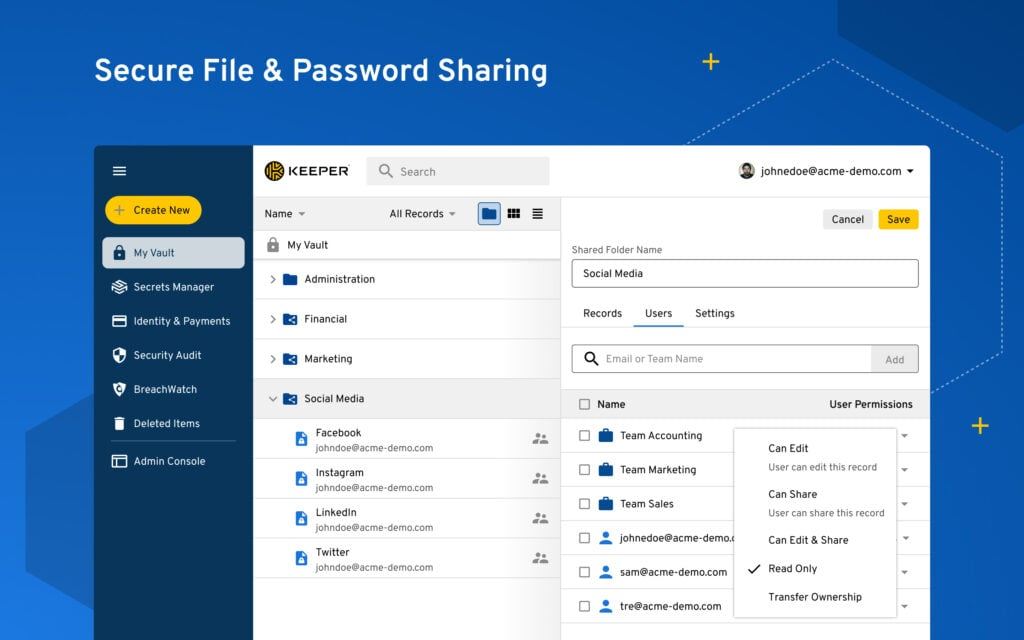
Keeper Security is an advanced encryption software solution that excels at safeguarding and managing passwords. Its distinctive focus on password encryption and management ensures a secure digital environment, particularly for those who juggle multiple online accounts.
Why I Picked Keeper Security: Keeper Security is my selection due to its robust encryption methods specifically tailored for password management. In a digital world where every user juggles multiple passwords across platforms, Keeper Security stands out with its emphasis on not just password encryption but also password management. I firmly believe it's the best for users grappling with the challenges of managing multiple passwords securely.
Standout features & integrations:
Keeper Security utilizes AES 256-bit encryption to protect your password information. It also features an auto-fill function for ease of use and a secure digital vault for storing sensitive documents.
With its integration capabilities, Keeper can sync across all devices and platforms, including major operating systems such as Apple iOS and Android.
Pros and cons
Pros:
- Syncs across all devices and platforms.
- Uses AES 256-bit encryption for maximum security.
- Offers robust password management.
Cons:
- Some advanced features require separate purchase.
- Auto-fill function may not work perfectly on all websites.
- Requires annual commitment for the best pricing.
Best for a seamless blend of data protection and threat prevention
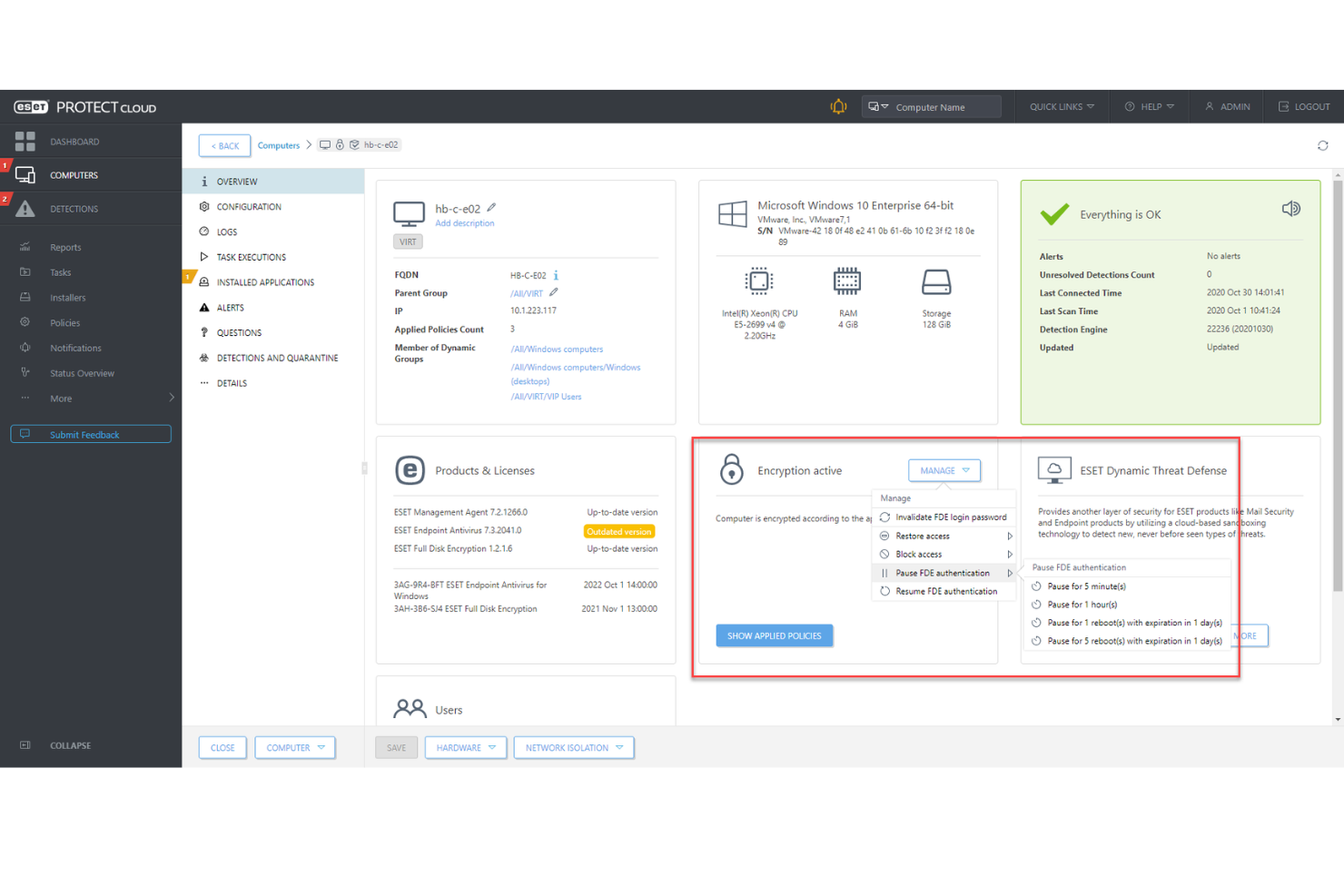
ESET PROTECT Complete is a security solution designed to provide businesses with robust protection against a wide range of cyber threats. Integrating encryption with endpoint security, the platform offers a unified approach to managing and securing corporate networks. It delivers features such as real-time threat detection, data protection, and device management, all through a single, user-friendly interface.
Why I Picked ESET PROTECT Complete: As an encryption software, ESET PROTECT Complete excels in offering a seamless blend of data protection and threat prevention. It provides strong encryption capabilities that safeguard sensitive information against unauthorized access and breaches. The platform stands out for its ability to integrate encryption with a comprehensive suite of security features, including advanced machine learning algorithms for detecting emerging threats and cloud-based sandboxing technology for isolating and analyzing suspicious files.
ESET PROTECT Complete Standout Features and Integrations
Features include an advanced layer of defense that utilizes cloud-based analysis to evaluate the behavior of suspicious code and malware in a safe, virtualized environment. This feature stands out because it significantly reduces the time to detect new, never before seen threats, including zero-day threats, by making decisions in minutes rather than hours or days. It also provides detailed reports on the analyzed samples, offering insights into the behavior of potential threats.
Integrations include Microsoft Windows Defender Antivirus, Microsoft Windows Security, VMware vSphere, Microsoft Azure, Google Cloud Platform, Amazon Web Services, Kubernetes, Docker, Microsoft Active Directory, and Jira.
Pros and cons
Pros:
- Comprehensive reporting tools for in-depth security insights
- Advanced threat detection and response capabilities
- Lightweight system footprint ensures minimal impact on performance
Cons:
- Requires technical knowledge for advanced feature utilization
- Pricing can be high for smaller organizations
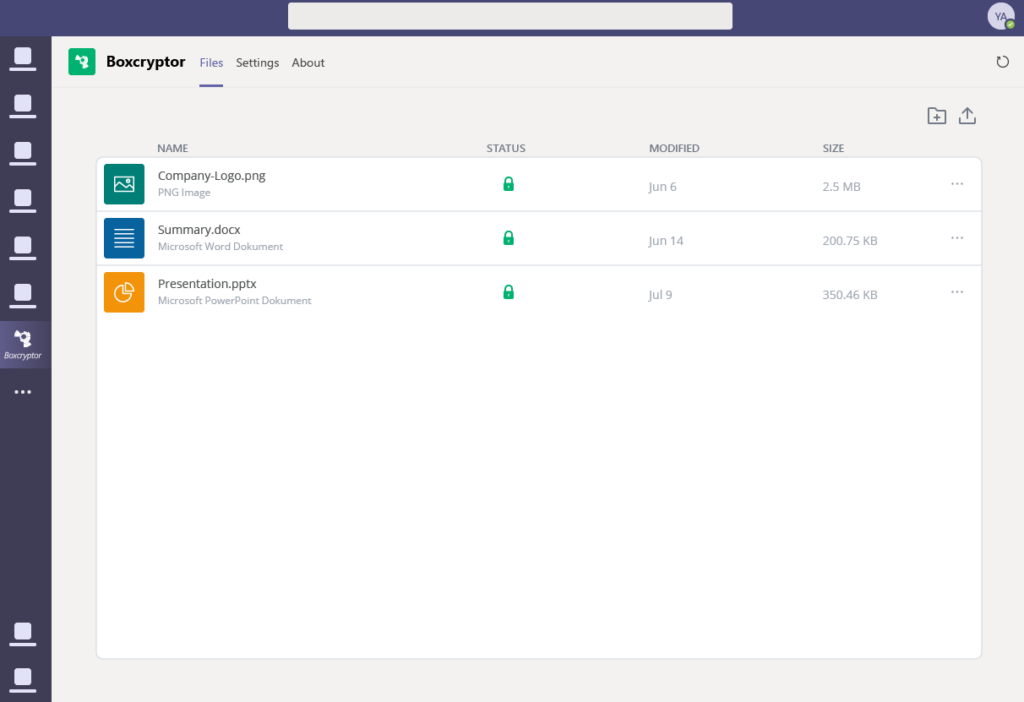
Boxcryptor is an encryption software tool that is specifically designed to protect your files in the cloud. It caters to users who want to ensure their data is secure across various cloud storage services. This feature of Boxcryptor makes it an ideal choice for anyone who uses multiple cloud platforms and wants consistent encryption across them.
Why I Picked Boxcryptor: In determining the best encryption software for cloud services integration, I chose Boxcryptor. Its unique compatibility with a wide range of cloud service providers sets it apart. I see it as the most capable tool for users who value integration and consistent security across various cloud platforms.
Standout features & integrations:
Boxcryptor offers end-to-end encryption, two-factor authentication, and file versioning to enhance data security. It provides robust security to more than 30 cloud storage providers.
Integrations include popular platforms like Dropbox, Google Drive, and OneDrive, ensuring users can enjoy secure data across various cloud storage services.
Pros and cons
Pros:
- Supports file versioning.
- Offers end-to-end encryption and two-factor authentication.
- Compatible with more than 30 cloud service providers.
Cons:
- Setting up two-factor authentication can be complex for new users.
- File versioning only available for selected cloud services.
- Requires an annual subscription for the best pricing.
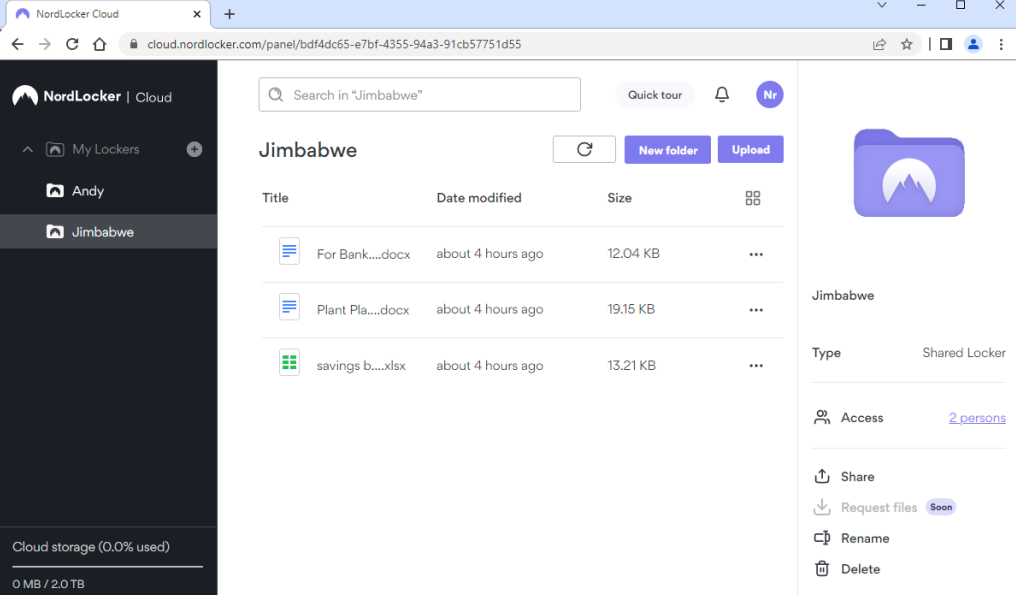
NordLocker is a reliable encryption software designed to provide advanced encryption for cloud storage. Its focus on cloud security makes it the go-to tool for those who require comprehensive protection for their cloud-based data.
Why I Picked NordLocker: NordLocker is my choice due to its emphasis on cloud storage encryption, which is crucial in our increasingly cloud-centric world. Its cloud-first approach offers a layer of security often overlooked by other encryption tools. This specialization is why NordLocker earns my vote as the best for cloud storage encryption.
Standout features & integrations:
NordLocker uses robust encryption standards (Argon2, AES256, ECC) to ensure the security of your cloud files. Features include zero-knowledge privacy, meaning only you can access your encrypted files, and easy sharing of encrypted files.
The software is deeply integrated with popular cloud services like Dropbox and Google Drive.
Pros and cons
Pros:
- Zero-knowledge privacy adds an additional layer of security.
- Deep integration with popular cloud services.
- Superior encryption for cloud storage.
Cons:
- The user interface may require a small learning curve for non-tech users.
- Requires annual commitment for the best pricing.
- Limited support for cloud services outside of the mainstream providers.
GnuPG, or GNU Privacy Guard, is an open-source encryption software designed to secure your data with high-grade encryption standards. As an open-source tool, it offers a high level of transparency and flexibility, making it a top choice for open-source enthusiasts.
Why I Picked GnuPG (GNU Privacy Guard): I chose GnuPG for its commitment to open-source principles, allowing users to view and modify its code, and fostering a community-driven approach to data security. Its distinction lies in the way it embodies the open-source ethos, granting users not only the ability to secure their data but also the freedom to tailor their security measures. This tool stands as the best choice for open-source enthusiasts due to its unique blend of transparency, control, and robust encryption capabilities.
Standout features & integrations:
GnuPG impresses with its support for both symmetric and asymmetric encryption, giving users a range of security options. The software also enables the creation of secure tunnels, allowing for secure data transmission over the internet.
It integrates well with a variety of email clients, providing end-to-end encryption for email communications.
Pros and cons
Pros:
- Strong integration with email clients for secure communications.
- Offers both symmetric and asymmetric encryption.
- Open-source software allows for a high level of customization.
Cons:
- Lack of dedicated customer support due to its open-source nature.
- Requires some learning curve to fully exploit its features.
- The user interface might be challenging for non-technical users.
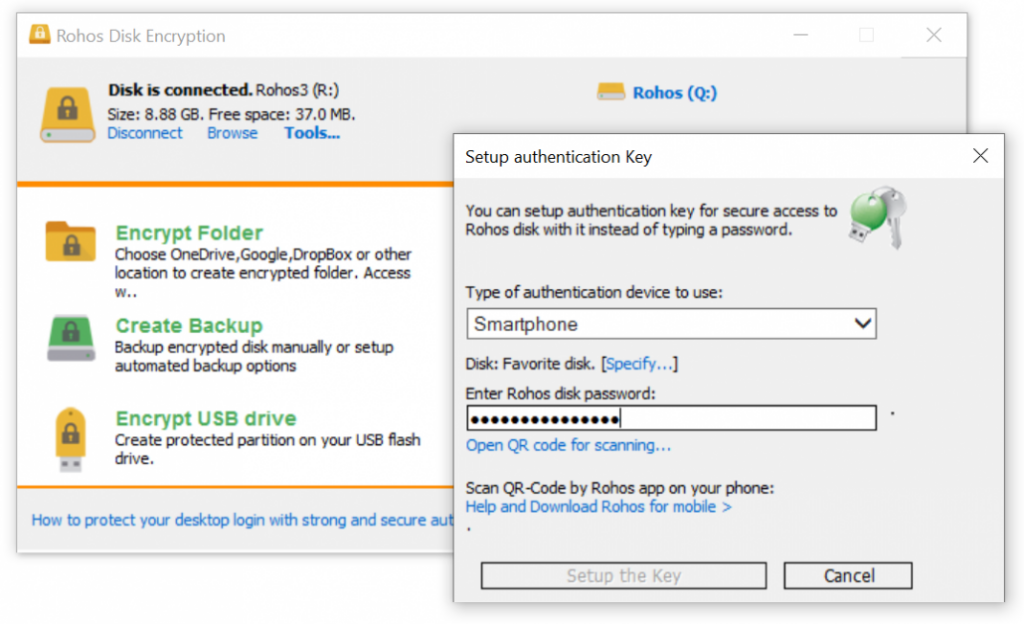
Rohos Disk Encryption is an encryption tool that excels in the creation of hidden and encrypted partitions on the computer or a USB flash drive. Its ability to create virtual encrypted disks makes it a suitable solution for users in need of encrypting and isolating sensitive data in a secure partition.
Why I Picked Rohos Disk Encryption: In selecting tools, I looked for unique attributes, and Rohos Disk Encryption distinguished itself with its virtual disk feature. This function allows users to establish encrypted and password-protected virtual disks effectively. Thus, it emerges as the best for creating virtual encrypted disks, a feature that provides an extra layer of security by segregating sensitive data in a separate, secure location.
Standout features & integrations:
Rohos Disk Encryption offers an automatic disk connection on system startup, which makes it user-friendly. It also provides a virtual keyboard to enter a password, protecting against potential keyloggers.
In terms of integrations, Rohos Disk Encryption works seamlessly with all Windows file systems and supports a variety of USB flash drives and memory cards.
Pros and cons
Pros:
- Compatibility with a wide range of storage devices.
- Automatic disk connection at system startup.
- Unique ability to create virtual encrypted disks.
Cons:
- One-time fee may be off-putting for users seeking monthly plans.
- Requires more technical understanding to use effectively.
- Lacks explicit software integrations.
Sophos SafeGuard Encryption is a comprehensive data protection solution that provides persistent file encryption, securing data across different platforms and devices. It offers extensive security features that can cater to the complex requirements of enterprise-level operations, thus making it best suited for companies needing robust, large-scale data protection.
Why I Picked Sophos SafeGuard Encryption: I picked Sophos SafeGuard Encryption as the best choice for enterprise-level security after comparing it with other options. Its capacity to protect data across a wide variety of devices and platforms stands out, giving it the edge for companies that operate on a larger scale.
Standout features & integrations:
Sophos SafeGuard Encryption provides a centralized management platform, enabling easy control over data encryption across multiple devices. Features like full-disk encryption, file encryption, and data exchange protection provide a comprehensive security package.
The software integrates well with other Sophos security products, creating a cohesive enterprise-level security environment.
Pros and cons
Pros:
- Well-integrated with other Sophos security products.
- Offers centralized management for easy control.
- Provides comprehensive security across various devices and platforms.
Cons:
- Setup and configuration might require a professional or IT support.
- Could be overwhelming for smaller businesses.
- Pricing information is not directly available.
7-Zip is a versatile encryption software that excels in its ability to integrate file compression with encryption. This integration allows users to compress files for efficient storage and transmit them securely, making it the best tool for integrated file compression.
Why I Picked 7-Zip: I selected 7-Zip for its dual functionality of file compression and encryption, which sets it apart from many other encryption tools. It's the combination of these two crucial features that makes 7-Zip a unique addition to this list. For users seeking to conserve storage space while maintaining data security, 7-Zip emerges as the best choice for integrated file compression.
Standout features & integrations:
7-Zip's notable features include strong encryption using the AES-256 standard and a high compression ratio in its 7z file format. It also supports a wide range of formats for compression and decompression.
Integrations are plentiful, with 7-Zip working seamlessly with Windows Shell, providing a useful command-line version, and offering localization for up to 87 languages.
Pros and cons
Pros:
- Extensive support for different file formats.
- Strong encryption with AES-256.
- Effective integration of encryption and compression.
Cons:
- Open-source nature might not provide the level of support some businesses require.
- Lack of native macOS and Linux support.
- The user interface can be less intuitive compared to other tools.
Secure IT is an encryption application that's designed to safeguard your files with top-notch encryption methods. It's specifically crafted for file encryption, making it an ideal choice for those in need of robust file protection solutions.
Why I Picked Secure IT: I picked Secure IT for this list after judging its performance in providing robust file encryption. It has a unique compression and encryption combination, making it stand out from the competition and justifying its position as the best for robust file encryption.
Standout features & integrations:
Secure IT provides 448-bit encryption, which is one of the most powerful encryptions in the market. The software's inbuilt compression feature significantly reduces the size of your files while encrypting them.
It does not have explicit integrations, but it operates independently of your file storage method, meaning it can work with any storage solution, including cloud services.
Pros and cons
Pros:
- One-time payment, no recurring fees.
- Inbuilt file compression during encryption saves storage space.
- Strong 448-bit encryption guarantees secure file protection.
Cons:
- The user interface may seem outdated to some users.
- Lacks advanced features found in enterprise-grade encryption software.
- No specific integrations with other software or services.
CryptoForge is a security software designed for encrypting files and folders. The tool is known for its multi-layered encryption ability, which assures that the user's data has multiple layers of security, making it highly resistant to breaches.
Why I Picked CryptoForge: I selected CryptoForge for this list because of its ability to provide a unique multi-layered encryption process, which is not common among most encryption tools. This tool goes above and beyond by not only encrypting data but doing so across multiple layers, which significantly increases the security of the encrypted data. Hence, I believe it's the best for users who prioritize robust, multi-layered data encryption.
Standout features & integrations:
CryptoForge offers strong features including up to 448-bit encryption, a file shredder for complete data deletion, and text encryption for secure communication. Its built-in compression minimizes the file size post-encryption.
While it does not provide any explicit software integrations, it is compatible with any application that uses Windows file I/O functions, broadening its utility across various systems and programs.
Pros and cons
Pros:
- One-time payment for lifetime usage.
- Offers text encryption for secure communication.
- Provides robust, multi-layered data encryption.
Cons:
- Not the cheapest option for individuals on a tight budget.
- Advanced features might require a learning curve.
- Lacks explicit software integrations.
Kruptos 2 Professional is an encryption tool designed to protect sensitive data stored on your computer or cloud servers. Its prime focus on safeguarding files and folders makes it especially apt for individual users or businesses that primarily require protection at the file level.
Why I Picked Kruptos 2 Professional: The reason I chose Kruptos 2 Professional for this list is its dedication to file and folder protection. In my comparison with other tools, Kruptos stood out for its thorough and specific security measures that guard individual files and folders, demonstrating its distinctiveness and suitability for the 'best for file and folder protection' title.
Standout features & integrations:
Kruptos 2 Professional comes with powerful features, including 256-bit encryption, a file shredder, and a password analyzer. The tool seamlessly works with cloud storage services like Google Drive and Dropbox, allowing you to secure your files before uploading them.
Pros and cons
Pros:
- One-time payment with free future updates.
- Compatibility with popular cloud services like Google Drive and Dropbox.
- Strong 256-bit encryption provides robust security.
Cons:
- No multi-user licensing options; each license is for a single user.
- Lack of enterprise-level features might be a limitation for larger businesses.
- Does not have a monthly subscription option.
Other Encryption Software
Below is a list of additional Encryption Software tools that I shortlisted but did not make it to the top 12. Definitely worth checking them out.
Related Software & Tool Reviews
If you still haven't found what you're looking for here, check out these other types of tools that we've tested and evaluated.
- Network Monitoring Software
- Server Monitoring Software
- SD-Wan Solutions
- Infrastructure Monitoring Tools
- Packet Sniffer
- Application Monitoring Tools
Selection Criteria For Best Encryption Software
Selecting encryption tools requires a nuanced approach, focusing on functionality and how it meets specific use cases crucial to each buyer's unique needs. Through personal trials and research, I've developed this set of criteria for evaluating encryption tools based on their ability to address these needs effectively.
Core Encryption Software Functionality: 25% of total weighting score
To be considered for inclusion on my list of the best encryption tools, the solution had to fulfill common use cases. These include:
- Securing sensitive data both at rest and in transit
- Ensuring regulatory compliance for data protection standards
- Providing user-friendly key management and recovery options
- Facilitating secure file sharing and collaboration
- Offering scalable solutions that grow with the business
Additional Standout Features: 25% of total weighting score
- Identifying tools that offer unique encryption methods, such as homomorphic encryption or quantum-resistant algorithms.
- Recognizing solutions with advanced data protection features, like automatic encryption of files upon creation.
- Valuing integrations with other security tools to enhance overall data protection strategies.
- Appreciating innovative user access controls, such as biometric authentication for key retrieval.
- Highlighting tools with exceptional performance efficiency, minimizing impact on system resources.
Usability: 10% of total weighting score
- Preference for tools with intuitive interfaces, allowing users to easily encrypt and decrypt data without extensive training.
- Value in drag-and-drop functionality for encrypting files and folders.
- Appreciation for clear, concise dashboard displays that provide quick access to encryption status and alerts.
Onboarding: 10% of total weighting score
- Looking for quick setup processes that facilitate immediate use of the tool.
- Emphasizing the availability of comprehensive training materials, such as videos, tutorials, and documentation.
- Appreciating interactive product tours and responsive chatbots that guide new users through the tool's features and functionalities.
Customer Support: 10% of total weighting score
- Assessing availability and responsiveness of support teams through various channels (e.g., live chat, email, phone).
- Valuing detailed FAQ sections and community forums for peer-to-peer assistance.
- Considering the presence of a dedicated account manager for enterprise clients.
Value For Money: 10% of total weighting score
- Evaluating the pricing structure against the feature set provided, looking for competitive rates that offer substantial encryption capabilities.
- Considering flexible pricing plans that accommodate businesses of different sizes and requirements.
- Assessing the availability of free trials or demos to test the tool before committing financially.
Customer Reviews: 10% of total weighting score
- Analyzing feedback for mentions of reliability, performance, and ease of use.
- Paying attention to comments on customer support responsiveness and helpfulness.
- Taking note of user testimonials regarding the tool's impact on meeting compliance requirements and improving data security.
Through this approach, I aim to guide software buyers toward selecting encryption tools that not only meet their immediate security needs but also offer value, ease of use, and scalability to support their business as it grows and evolves.
Trends in Encryption Software For 2024
In 2024, the encryption software market has witnessed significant innovations and shifts, reflecting the evolving landscape of cybersecurity and the increasing complexity of threats. As businesses continue to prioritize the protection of sensitive data against breaches and cyber-attacks, understanding the latest trends in encryption software and technology is crucial.
Through an analysis of product updates, press releases, and release logs from leading tools, several key trends have emerged, highlighting the direction in which encryption technologies are moving. Here's an overview of the trends I'm seeing:
Trends in Encryption Software and Technology
- Increased Adoption of Quantum-Resistant Algorithms: With the looming threat of quantum computing, there's a significant push towards developing and integrating quantum-resistant algorithms into encryption software. These algorithms are designed to withstand attacks from quantum computers, ensuring long-term data security.
- Enhanced Key Management Solutions: The complexity and importance of managing encryption keys have led to the development of more sophisticated key management solutions. These systems offer enhanced security, ease of use, and flexibility, addressing the challenges of key lifecycle management.
- Homomorphic Encryption: One of the most novel functionalities emerging is homomorphic encryption, which allows computations to be performed on encrypted data without decrypting it. This offers unprecedented data privacy and security, especially for businesses dealing with sensitive information.
Evolving and In-Demand Features
- Automated Compliance Reporting: With stringent regulatory requirements, encryption tools now often include automated compliance reporting features. These tools help businesses ensure they meet data protection standards, reducing the risk of non-compliance penalties.
Less Demanded Features
- Traditional Encryption Methods: With the advent of more advanced techniques, traditional encryption methods are becoming less favored. Businesses are looking for cutting-edge solutions that offer stronger security against sophisticated cyber threats.
These innovations reflect the ongoing effort to meet the complex needs of businesses in protecting their sensitive information against an ever-evolving threat landscape. As we move further into 2024, these trends are expected to shape the priorities and investments of IT professionals in encryption technologies, ensuring businesses can confidently secure their data in an increasingly digital world.
What is Encryption Software?
Encryption software is a category of security tools designed to protect data by converting it into a coded format that can only be read with a key. These tools are commonly used by IT professionals, cybersecurity experts, and data privacy officers to safeguard sensitive information. Businesses use this type of software to secure data in transit and at rest, ensuring that confidential information remains protected from unauthorized access and breaches.
Features like robust encryption algorithms, key management systems, and secure file sharing support the safeguarding of sensitive data, compliance with regulatory standards, and the prevention of data breaches. Overall, encryption software provides a critical layer of security that helps maintain the confidentiality and integrity of data across various digital environments, offering peace of mind in an increasingly interconnected world.
Features of Encryption Software
Here are some critical features that I look for in encryption software:
- Strong Encryption Algorithms: The foundation of any encryption software. Strong algorithms ensure that the encrypted data remains secure against brute force attacks and other decryption attempts. This is vital for safeguarding sensitive business information from unauthorized access.
- Easy Integration with Existing Systems: Facilitates seamless security enhancement. Encryption software should easily integrate with your current systems to protect data without disrupting existing workflows, thereby maintaining productivity while enhancing security.
- Comprehensive Data Protection: Safeguards all types of data. Whether it's emails, files, or databases, the software should offer comprehensive protection to secure all forms of sensitive business data from potential threats.
- High Performance and Efficiency: Maintains system performance. It's important that the encryption software operates efficiently without significantly impacting system performance, ensuring that business operations continue smoothly.
- Scalability: Grows with your business. As your business expands, your encryption needs will evolve. Scalable software can adapt to increased demands without compromising security or performance.
- User-Friendly Interface: Ensures ease of use. A user-friendly interface allows employees to securely manage and share encrypted data without requiring extensive training, thus reducing the risk of human error.
- Robust Key Management: Central to encryption security. Effective management of encryption keys is essential, as lost or stolen keys can lead to data breaches. The software should offer secure storage and recovery options for keys.
- Multi-Platform Support: Covers all devices and platforms. With businesses using a variety of devices and operating systems, encryption software must support all platforms to ensure comprehensive data protection.
- Compliance with Regulations: Meets legal requirements. The software should help your business comply with relevant data protection regulations, such as GDPR or HIPAA, to avoid legal penalties and maintain customer trust.
- Regular Updates and Support: Keeps the software effective. Regular updates ensure that the encryption software remains effective against new threats, while reliable support helps resolve any issues promptly.
Selecting encryption software with the right mix of these features not only ensures that your information remains secure from external threats, but also reinforces the trust your clients place in your ability to safeguard their data.
Benefits of Encryption Software
In an era where data breaches and cyber threats are rampant, encryption software stands as a critical line of defense for users and organizations alike. It serves as an essential tool for safeguarding sensitive information, ensuring that data remains confidential and secure from unauthorized access. Below are five primary benefits of utilizing encryption software:
- Enhanced Data Security: Encryption software significantly elevates the security level of data stored on devices or transmitted over networks. By converting sensitive information into encrypted form, it protects against unauthorized access and data breaches, ensuring that only authorized individuals can view the data.
- Regulatory Compliance: Many industries are subject to strict regulatory requirements for data protection. Encryption software helps businesses comply with these regulations, such as GDPR or HIPAA, by providing the necessary tools to secure personal and sensitive information, thereby avoiding potential legal penalties and fines.
- Protection for Remote Work: With the rise of remote work, encryption software ensures that data remains secure, even when accessed from various, potentially insecure, locations. It creates a secure environment for data access and sharing, essential for maintaining the integrity of information outside the traditional office space.
- Data Integrity: Beyond confidentiality, encryption software also ensures the integrity of data. It protects information from being altered or tampered with by unauthorized parties, ensuring that the data received is exactly as it was sent, without any modifications.
- Competitive Advantage: In today's digital landscape, customers value privacy and security. By employing encryption software, businesses can enhance their reputation as trustworthy guardians of customer data, offering a competitive edge in markets where data security is a significant concern.
Adopting encryption software is not just about adhering to best practices in cybersecurity; it's about taking proactive steps to secure the lifeblood of your organization—its information. As businesses continue to navigate the complexities of digital transformation, the role of encryption in safeguarding digital assets becomes increasingly critical, offering a clear pathway to achieving both operational excellence and customer trust.
Costs & Pricing For Encryption Software
Encryption software offers various plans and pricing options tailored to meet different needs, from individual users safeguarding personal data to large organizations protecting vast amounts of sensitive information. Understanding the common types of plans and what they typically include will help you make an informed decision that aligns with your security requirements and budget constraints.
Plan Comparison Table For Encryption Software
Here's an overview of typical pricing structures of encryption software:
| Plan Type | Average Price | Common Features |
|---|---|---|
| Free | $0 | Basic encryption capabilities, limited data volume, community-based support |
| Individual | $50 - $100/year | Advanced encryption features, single user license, email support, limited cloud storage integration |
| Small Business | $100 - $250/year | Multi-user licenses, team collaboration tools, priority support, increased cloud storage options |
| Enterprise | $250 - $500+/year | Customizable encryption solutions, unlimited user licenses, dedicated support, full cloud storage integration, compliance management tools |
Selecting the right plan requires a balance between understanding the level of security needed and the budget available. Consider starting with a free plan to get a feel for the software, then upgrade as your needs grow and become more complex.
Encryption Software Frequently Asked Questions
If you’ve still got questions about encryption software, check out these answers to common questions other buyers have!
Are there any free encryption software options?
Yes, there are several free encryption software options available. Examples include VeraCrypt and BitLocker, which offer free encryption features.
What Do You Think?
Certainly, while I've done my best to provide a comprehensive list of top encryption software, the tech industry is always evolving, with new tools cropping up regularly. If you've come across a tool that you believe should have made it to this list, I'd love to hear from you.
Please feel free to share your recommendations and experiences, as your input can help enrich this guide for everyone.