12 Best Cloud Workload Protection Platforms Shortlist
After a thorough evaluation, I've curated a list of the 12 best cloud workload protection platforms aptly suited to address your specific challenges.
- Prisma Cloud - Best for comprehensive cloud security posture
- Trend Micro - Best for hybrid cloud protection
- Check Point CloudGuard - Best for advanced threat prevention
- Qualys - Best for vulnerability management
- CrowdStrike - Best for endpoint security integration
- Cisco Tetration - Best for data center protection
- Aqua Security - Best for container security
- Microsoft Azure Defender - Best for native Azure integrations
- Amazon Web Services (AWS) GuardDuty - Best for threat detection in AWS environment
- Fortinet - Best for integrated security architecture
- Sophos Cloud Optix - Best for visibility into cloud assets
- Bitdefender - Best for multi-layered security modules
Navigating the intricacies of cloud security can be a daunting task. That's where cloud workload protection platforms come into play. In essence, these tools safeguard your cloud-based assets and infrastructures from potential threats. The beauty of them? They not only bolster security but also simplify the complexities tied to managing multi-cloud environments.
I delved into countless options to address these challenges, and I'm eager to share those that truly stand out in alleviating these pain points.
What Is a Cloud Workload Protection Platform?
Cloud workload protection platforms (CWPP) are security solutions designed to safeguard workloads in cloud environments, including virtual machines, containers, and serverless computing. They provide a robust defense against potential threats by monitoring activities, ensuring configurations adhere to security policies, and detecting vulnerabilities.
Organizations of all sizes, especially those transitioning to or expanding their cloud infrastructure, deploy these platforms to ensure consistent security across their cloud-native applications and data, mitigating risks associated with unauthorized access, data breaches, and malware.
Overviews of the 12 Best Cloud Workload Protection Platforms
1. Prisma Cloud - Best for comprehensive cloud security posture
Prisma Cloud by Palo Alto Networks offers a dynamic cloud security solution that caters to public, private, and hybrid environments. Recognizing the expanding attack surface in cloud computing, this platform ensures that cloud workload security and posture are fortified at all layers.
Why I Picked Prisma Cloud:
In my journey of selecting the most capable tools, Prisma Cloud consistently surfaced as a top contender. I chose it because of its comprehensive approach to cloud security posture management (CSPM). When comparing and judging various platforms, Prisma Cloud stood out because of its expansive feature set and dedication to securing all types of cloud architectures. Given its dedication to a comprehensive cloud security framework, it’s clear to see why it's best for a robust cloud security posture.
Standout features & integrations:
Prisma Cloud boasts cloud-native application protection platform (CNAPP) capabilities which tackle both CSPM and runtime protection for apps. Features like real-time threat detection, prioritizing misconfigurations, and swift remediation mechanisms are part of its core offering. Integration-wise, the platform thrives with robust API connections, collaborating smoothly with major cloud services and providers such as AWS, GCP, and Azure.
Pricing:
Pricing upon request
Pros:
- Expansive multi-cloud security platform
- API integrations with major cloud providers improve its utility
- Prioritization of vulnerabilities coupled with remediation tools
Cons:
- Some users may find the dashboard a tad intricate
- Granular controls for specific cloud services might be a wish for certain advanced users
- Steeper learning curve for those new to cloud security tools.
2. Trend Micro - Best for hybrid cloud protection
Trend Micro provides a robust cloud security platform, designed to integrate with both on-premises and cloud environments. Its ability to merge traditional and cloud-based security measures positions it as a leader in hybrid cloud protection.
Why I Picked Trend Micro:
During my analysis and selection process, Trend Micro's approach to cloud security consistently caught my attention. The decision to pick this tool was influenced by its vast security features tailored specifically for hybrid environments. When judging and comparing with other security platforms, Trend Micro’s commitment to providing unparalleled protection in both on-premises and public cloud scenarios made it distinctly superior. Given these attributes, it’s evident why I hold the opinion that it's best for hybrid cloud protection.
Standout features & integrations:
Trend Micro offers real-time cloud workload security coupled with a specialized cloud security posture management (CSPM) system to quickly identify and remedy misconfigurations. Its vulnerability scanning tools and native security features further cement its position as a comprehensive security solution. In terms of integrations, Trend Micro excels with its API-centric approach, effortlessly collaborating with key cloud providers like AWS, GCP, and Azure, while also supporting tools used by DevOps and security teams.
Pricing:
Pricing upon request
Pros:
- Comprehensive hybrid security model encompassing both cloud and on-premises environments
- Strong API integrations, facilitating better collaboration with major cloud services
- Advanced cloud security posture management features for misconfiguration detection and remediation
Cons:
- For smaller businesses, the plethora of features might be overwhelming
- More integration documentation may be required for custom setups
- Some users might prefer a more streamlined dashboard experience.
3. Check Point CloudGuard - Best for advanced threat prevention
Check Point CloudGuard is a prominent cloud security solution dedicated to safeguarding public and multi-cloud deployments. With its primary focus on advanced threat prevention, it effectively minimizes the attack surface, making it a formidable tool against sophisticated cyber threats.
Why I Picked Check Point CloudGuard:
In the realm of cloud security, I selected Check Point CloudGuard for its reputation in combatting intricate threats. Through meticulous comparison and evaluation, it was evident that this platform possesses unparalleled capabilities in threat prevention. The depth and sophistication of its security tools, combined with the advanced threat intelligence it offers, solidified my judgment. This makes me confident in saying it's the best for advanced threat prevention.
Standout features & integrations:
Check Point CloudGuard shines with its cloud-native application protection platform (CNAPP) and real-time cloud security posture management (CSPM), crucial for rectifying misconfigurations swiftly. Its cybersecurity measures prioritize threat remediation, significantly reducing the potential attack surface. On the integration front, CloudGuard boasts an API-driven architecture, connecting with major cloud providers, such as AWS, Azure, and Google Cloud, and aligning with DevOps practices and workflows.
Pricing:
Pricing upon request
Pros:
- Comprehensive advanced threat prevention mechanisms backed by rigorous security controls
- Integration capabilities with major cloud services via its advanced API
- Utilizes cloud security posture management to swiftly address vulnerabilities
Cons:
- The broad scope of features might present a steeper learning curve for newcomers
- Initial setup and configuration might require a more specialized skill set
- Some businesses might find the platform more complex than needed for their operations.
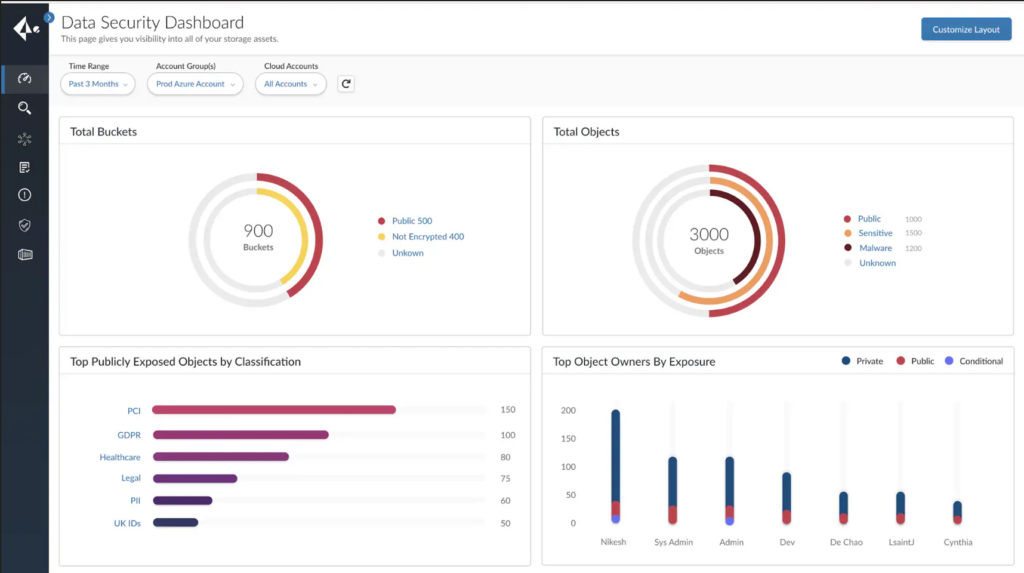
4. Qualys - Best for vulnerability management
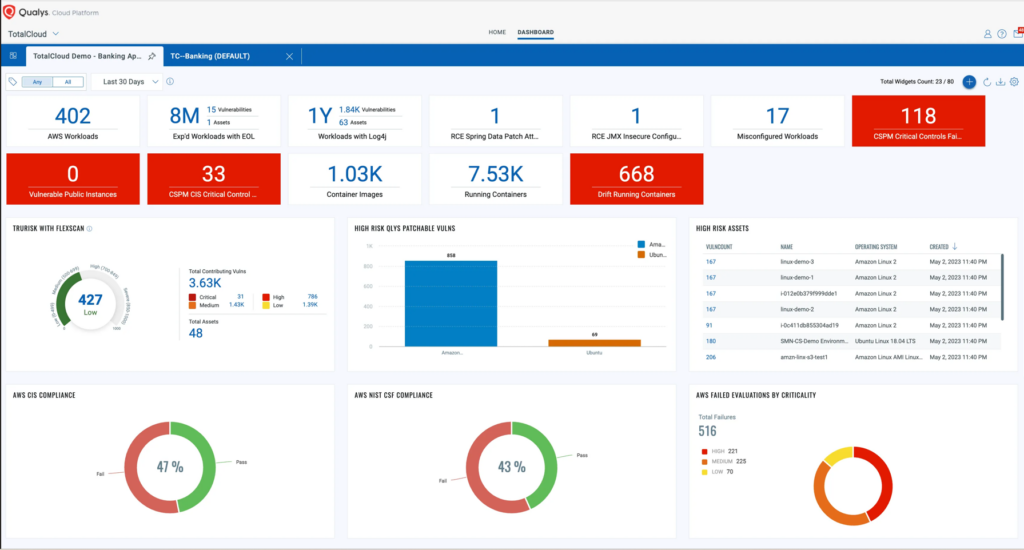
Qualys is a leading cloud-based security platform renowned for its meticulous vulnerability management capabilities. It is adept at scanning, detecting, and remediating vulnerabilities across diverse cloud and on-premises environments, solidifying its stance as best for vulnerability management.
Why I Picked Qualys:
Navigating through the maze of security platforms, I zeroed in on Qualys for its comprehensive approach to vulnerability scanning and management. While evaluating and comparing, what drew my attention was its unparalleled precision in identifying security flaws and its robust remediation mechanisms. These distinguishing traits positioned Qualys as the definitive choice for vulnerability management in my assessment.
Standout features & integrations:
Qualys showcases a comprehensive cloud security posture management (CSPM) system and is supported by real-time scanning for immediate detection of misconfigurations. Its vulnerability scanning extends to apps and serverless functions, allowing for a thorough assessment of the entire infrastructure. Integrating with a broad spectrum of cloud providers, including AWS, Azure, and Google Cloud, its API-driven nature complements automation efforts and fits perfectly within DevOps workflows.
Pricing:
Pricing upon request
Pros:
- Comprehensive vulnerability scanning across cloud and on-premises assets
- Offers cloud-native application protection platform (CNAPP) for multi-cloud environments
- Efficient integration with major cloud services through its API-driven nature
Cons:
- The vast range of tools and features might be overwhelming for smaller organizations
- There might be complexities in configuration and customization for specific needs
- Some users might face challenges in navigating its extensive reporting system.
5. CrowdStrike - Best for endpoint security integration
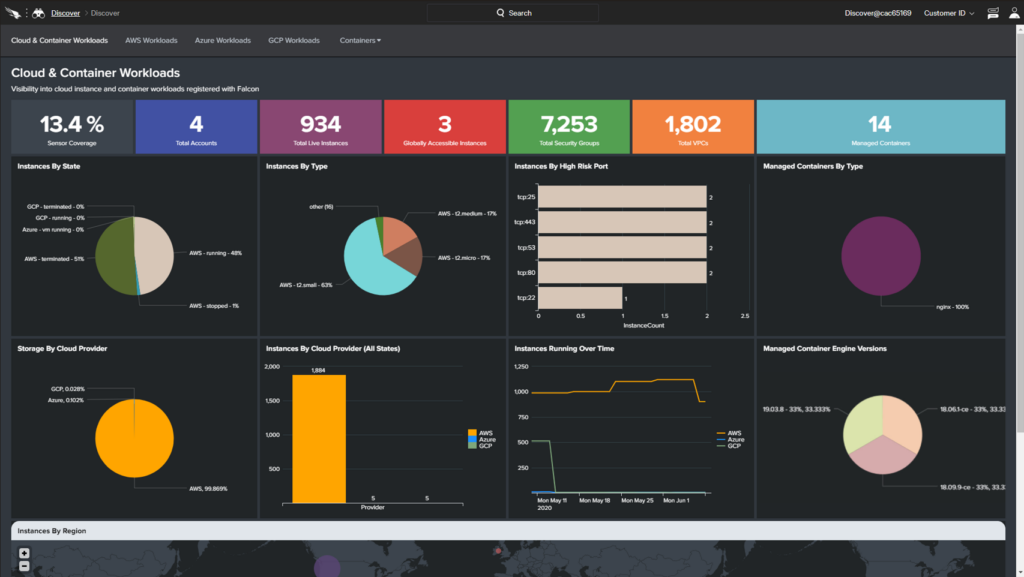
CrowdStrike is a premier cybersecurity firm that excels in delivering top-tier endpoint protection for organizations. With a focus on harnessing the power of the cloud, it offers comprehensive protection against threats, thereby earning its reputation as the best tool for endpoint security integration.
Why I Picked CrowdStrike:
In my pursuit of security platforms, CrowdStrike repeatedly emerged at the forefront. My selection was influenced by its adeptness in fusing the might of cloud computing with endpoint protection. Among the tools I assessed, CrowdStrike's unique approach in leveraging machine learning to counter threats and its cloud-native application protection platform (CNAPP) capabilities made it distinctively suitable. I firmly believe it to be the best for endpoint security integration due to these combined strengths.
Standout features & integrations:
CrowdStrike's cloud security posture management (CSPM) stands out, adeptly preventing misconfigurations. Another notable feature is its real-time remediation capabilities that respond swiftly to threats. Its integration prowess is remarkable, meshing well with key cloud providers like AWS, Google Cloud, and Azure. This, complemented by its API, ensures that automation and workflows align in a DevOps environment.
Pricing:
Pricing upon request
Pros:
- Robust endpoint protection leveraging cloud computing capabilities
- Real-time threat remediation, minimizing the attack surface
- Strong integrations with major cloud services, ensuring a comprehensive defense strategy
Cons:
- Might be perceived as complex for smaller businesses or those new to endpoint solutions
- While its features are expansive, some users might find the interface less intuitive than desired
- Dependency on the cloud may raise concerns for organizations leaning towards on-premises solutions.
6. Cisco Tetration - Best for data center protection
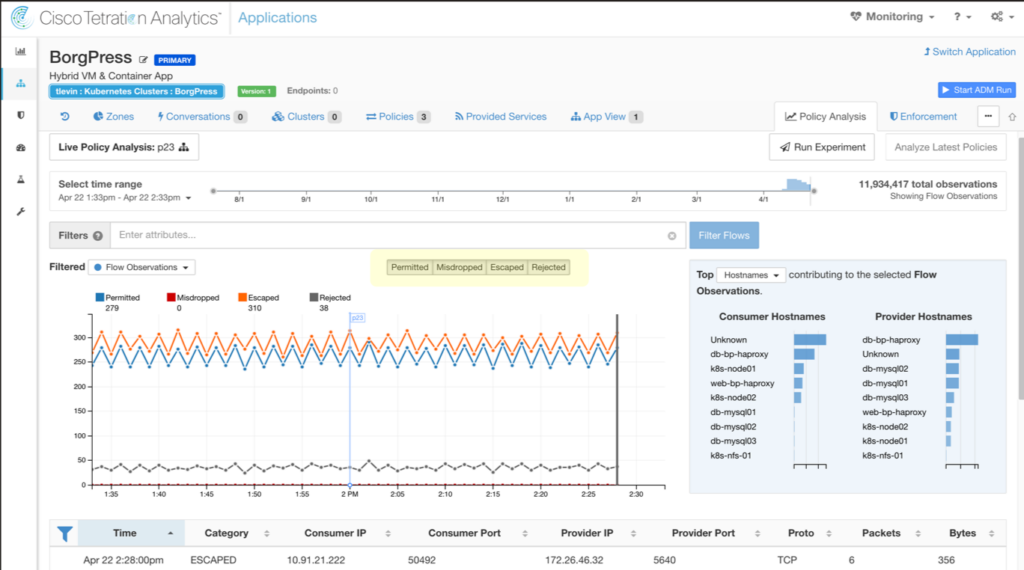
Cisco Tetration is a robust solution designed to provide unparalleled visibility, security, and compliance for applications running in data centers and cloud environments. By focusing on safeguarding critical data center resources, Tetration has positioned itself as an unparalleled choice for those aiming to prioritize data center protection.
Why I Picked Cisco Tetration:
When determining the right tools to shield data center resources, Cisco Tetration emerged as a top contender. Through a process of comparing and evaluating, I recognized the platform's advanced capabilities in micro-segmentation and its native security features. Its emphasis on ensuring a protected runtime environment for data center applications strongly justifies its standing as the best choice for data center protection.
Standout features & integrations:
Cisco Tetration stands out for its real-time application dependency mapping and vulnerability scanning, offering a comprehensive view of potential risks. Its cloud security posture management (CSPM) works diligently to identify and rectify misconfigurations. Integration-wise, Tetration is compatible with key cloud providers and platforms, including VMware, AWS, and GCP, ensuring flexibility for hybrid environments.
Pricing:
Pricing upon request
Pros:
- Offers deep visibility into data center workloads, illuminating the attack surface
- Micro-segmentation capability improves protection, reducing lateral movement of threats
- Flexible integration with major cloud providers and platforms ensures adaptability
Cons:
- The breadth of its features might come with a steep learning curve for some users
- For businesses only using a limited section of data center services, Tetration may seem excessive
- Some users might prefer more streamlined, purpose-specific solutions over its extensive suite.
7. Aqua Security - Best for container security
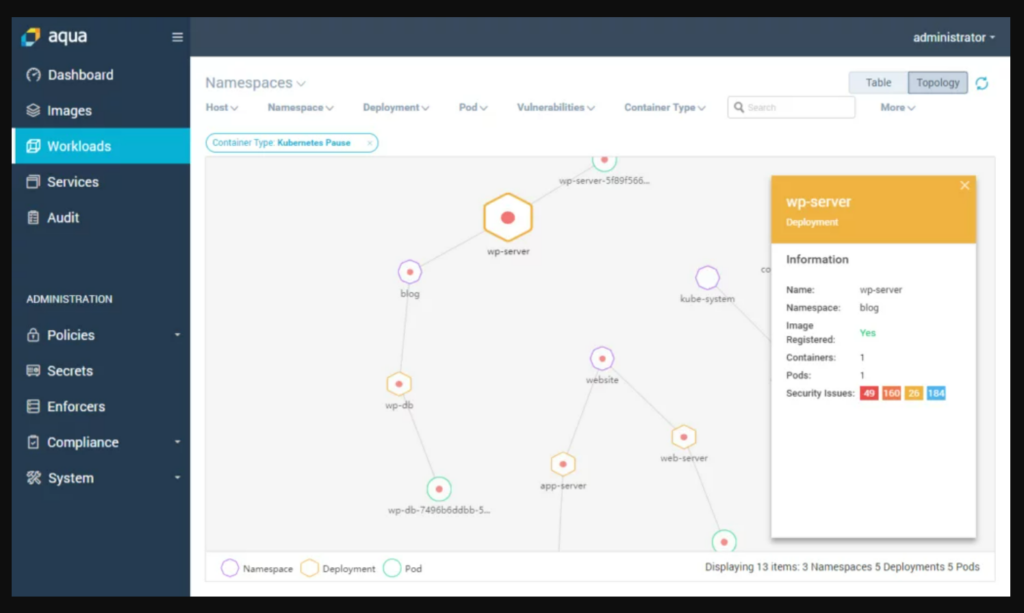
Aqua Security is a leading name when it comes to securing containerized applications throughout their lifecycle. It specializes in safeguarding workloads in cloud-native environments, making it an ideal choice for container security.
Why I Picked Aqua Security:
When I was selecting a tool for container security, Aqua Security consistently came up as a top choice based on numerous comparisons and opinions from industry experts. Judging its capabilities, it’s evident that its dedication to securing containers and the broader cloud-native ecosystem sets it apart. The decision to recognize Aqua Security as "Best for container security" stems from its advanced features and the security controls it places around these digital assets.
Standout features & integrations:
Aqua Security offers real-time monitoring and remediation of containerized applications, allowing security teams to identify and rectify vulnerabilities promptly. The platform's robust cloud security posture management (CSPM) helps in detecting and addressing misconfigurations before they can be exploited. Aqua integrates with various cloud providers, including AWS, GCP, and Azure, as well as with numerous DevOps tools through its versatile API.
Pricing:
Pricing upon request
Pros:
- Comprehensive container security, covering everything from image scanning to runtime protection.
- Provides cloud-native application protection platform (CNAPP) capabilities, ensuring holistic security for cloud-native ecosystems.
- Strong integrations with major cloud services, making implementation smoother for hybrid environments.
Cons:
- For smaller organizations, the plethora of features might seem overwhelming.
- Depending on the configuration and the environment, there might be occasional false positives in vulnerability scanning.
- Its focus on cloud-native might leave teams with more traditional setups looking for additional tools.
8. Microsoft Azure Defender - Best for native Azure integrations
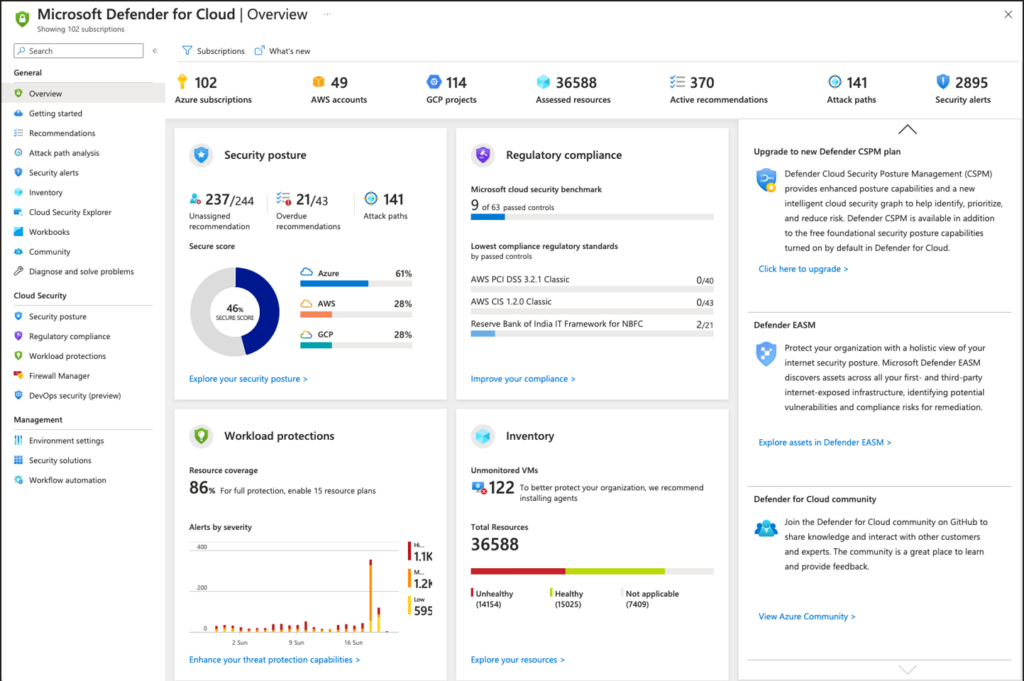
Microsoft Azure Defender is a comprehensive cloud security solution designed to offer protection for Azure workloads, including virtual machines, databases, and other Azure services. It's specially built for Azure, ensuring tailored security controls and native integrations within the Azure ecosystem.
Why I Picked Microsoft Azure Defender:
In determining the best tool for Azure-native security, I couldn't overlook Microsoft Azure Defender. Comparing its features and native integrations with those of other security platforms, it was clear that Azure Defender stood out. This tool was particularly selected for the "Best for native Azure integrations" title due to its integration and optimized functionalities within the Azure environment.
Standout features & integrations:
Azure Defender excels in offering real-time threat protection, ensuring that cloud workloads remain secure against the ever-evolving cyber threat landscape. With its robust cloud security posture management (CSPM) capabilities, it can identify and prioritize misconfigurations, making remediation more streamlined. Given that it's a product of Microsoft, Azure Defender offers unparalleled integrations within the Azure environment, from Azure VMs to serverless functions and other Azure cloud services.
Pricing:
Pricing upon request
Pros:
- Deeply integrated with the Azure ecosystem, offering native security features tailored for Azure services.
- Provides robust cloud security posture management (CSPM) capabilities.
- Offers real-time threat protection for a range of Azure resources.
Cons:
- May not be as effective for multi-cloud or hybrid environments that use multiple cloud providers.
- The focus on Azure-native integrations means organizations not using Azure as their primary cloud might find limited utility.
- For users new to the Azure platform, there could be a learning curve in understanding and managing its features.
9. Amazon Web Services (AWS) GuardDuty - Best for threat detection in AWS environment
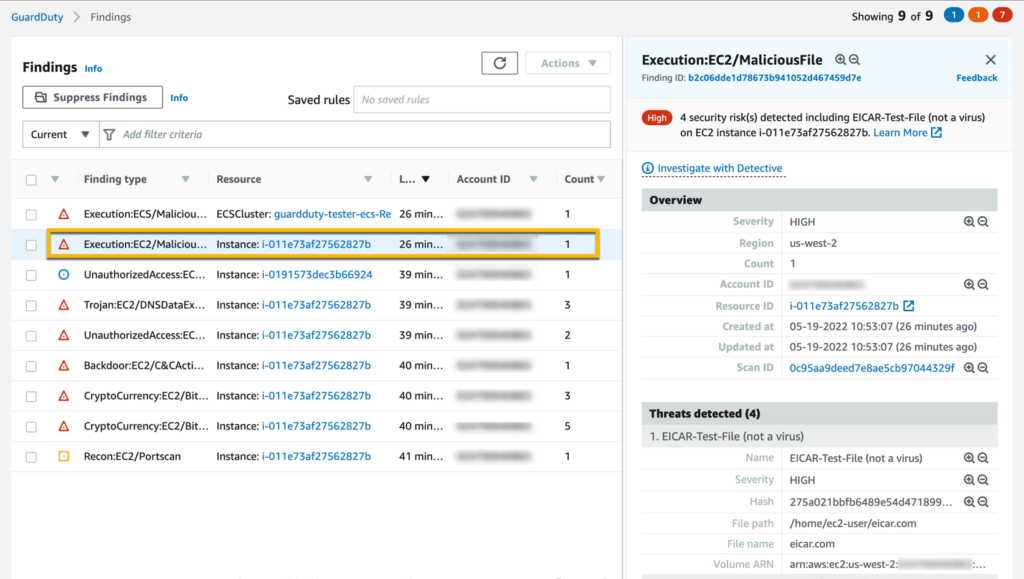
Amazon Web Services (AWS) GuardDuty is a cloud-native application protection platform that offers intelligent threat detection for AWS accounts and workloads. Leveraging machine learning, GuardDuty continuously analyzes AWS data sources to identify unusual activities, making it indispensable for AWS security.
Why I Picked AWS GuardDuty:
When it came to selecting the right tool for threat detection within the AWS environment, AWS GuardDuty was my foremost choice. Judging its capabilities against other cloud security solutions, I observed its distinct advantage in terms of native integration and its specialization in the AWS ecosystem. My opinion is that this tool is the "Best for threat detection in AWS environment" due to its adeptness at identifying AWS-specific threats and its in-depth understanding of AWS architectures.
Standout features & integrations:
AWS GuardDuty shines in real-time threat detection, identifying potential threats from sources such as VPC Flow Logs, AWS CloudTrail event logs, and DNS logs. Its use of machine learning allows for the pinpointing of potential threats without the need for user-defined rules or custom configurations. Additionally, its native integration with other AWS services ensures streamlined security operations and easier remediation workflows within the AWS environment.
Pricing:
Pricing upon request
Pros:
- Native to AWS, allowing for specialized threat detection tailored to AWS services.
- Utilizes machine learning for advanced threat detection without custom rules.
- Integration with a broad array of AWS services for comprehensive security controls.
Cons:
- Limited to the AWS environment, potentially making it less suitable for multi-cloud or hybrid deployments.
- Requires an understanding of AWS-specific configurations and structures.
- While it offers automated findings, some organizations may require manual review and verification of these findings.
10. Fortinet - Best for integrated security architecture
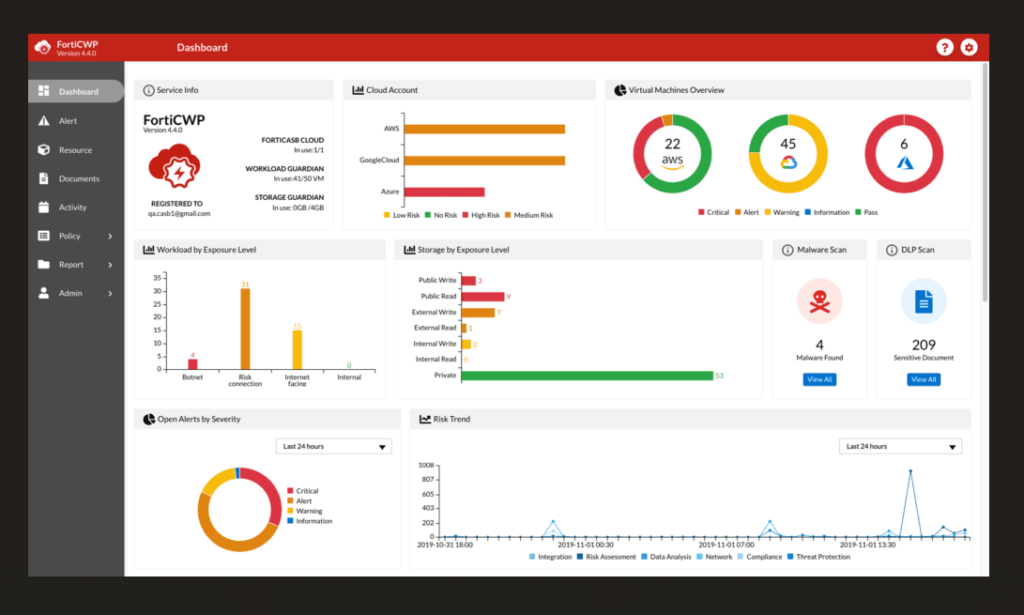
Fortinet provides a broad range of cybersecurity solutions, covering networks, endpoint, applications, data center, and cloud. With its commitment to integrated security architecture, Fortinet ensures comprehensive protection across various platforms and environments, aligning perfectly with the tag of being "best for integrated security architecture."
Why I Picked Fortinet:
In the realm of cybersecurity, myriad tools promise comprehensive protection, yet choosing Fortinet became evident as I compared and judged its offerings against others. It was the integrated security architecture of Fortinet that truly caught my attention, marking a distinction from its competitors. I believe that Fortinet's robust integrated architecture makes it the "Best for integrated security architecture" because it effectively consolidates multiple security controls, leading to a more unified defense mechanism.
Standout features & integrations:
Fortinet shines with its FortiGate next-generation firewalls, which provide both network and security features in a unified platform. The Fortinet Security Fabric integrates various security tools, allowing for real-time threat intelligence sharing and automated workflows. Beyond this, the platform's capabilities in cloud security posture management (CSPM) and cloud-native application protection ensure secure multi-cloud deployments.
Regarding integrations, Fortinet integrates with public cloud providers such as AWS, Google Cloud, and other IaaS platforms. Furthermore, it collaborates efficiently with VMware for virtualized environments and offers API integrations for improved automation and remediation capabilities.
Pricing:
Pricing upon request
Pros:
- Comprehensive integrated security architecture, consolidating various security controls.
- Compatibility with major public cloud providers ensures cloud workload security.
- Fortinet Security Fabric improves the collaboration between security tools for real-time intelligence sharing.
Cons:
- May require dedicated expertise for configuration and management, especially in complex environments.
- The vast array of products and features might be overwhelming for smaller businesses.
- Some users might face challenges while implementing specific integrations or features in hybrid environments.
11. Sophos Cloud Optix - Best for visibility into cloud assets
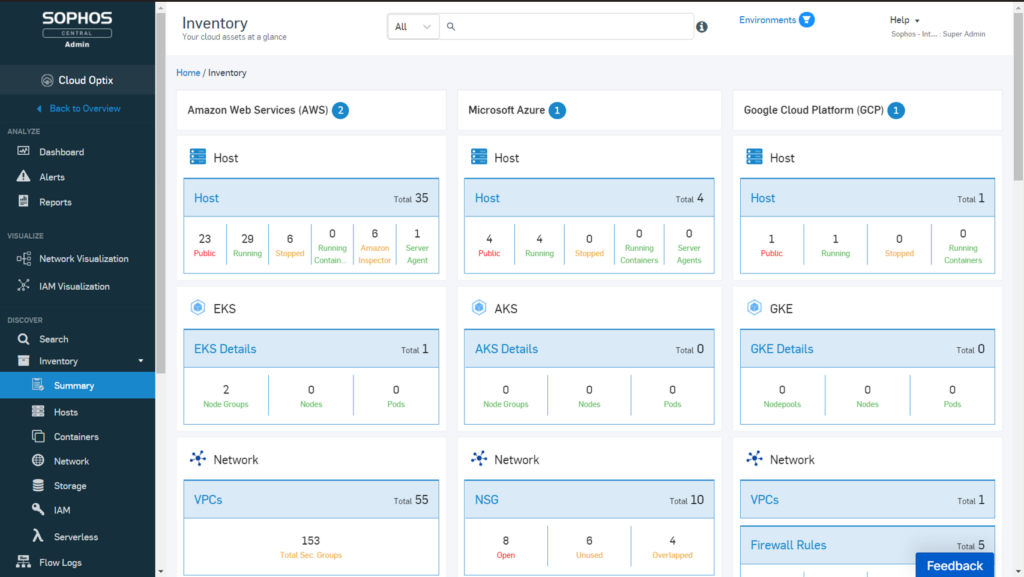
Sophos Cloud Optix delivers a potent cloud security platform that provides organizations with comprehensive visibility and analytics for their cloud environments. Its prowess in offering unparalleled insight into cloud assets and their configurations underscores its designation as "best for visibility into cloud assets."
Why I Picked Sophos Cloud Optix:
Navigating the vast landscape of cloud security tools, I found myself selecting Sophos Cloud Optix, given its impressive feature set and customer feedback. Its distinct focus on providing crystal-clear visibility into cloud assets, coupled with intelligent analytics, marked it as unique in my judgment. I determined that Sophos Cloud Optix stands tall as the "Best for visibility into cloud assets" primarily due to its unparalleled prowess in monitoring and visualizing cloud assets across multiple platforms.
Standout features & integrations:
Sophos Cloud Optix boasts advanced features like cloud security posture management (CSPM) that identifies misconfigurations and prioritizes remediation efforts. Moreover, its machine learning-powered analytics help security teams monitor the entire cloud environment, detect anomalies, and reduce the attack surface by eliminating vulnerabilities.
In terms of integrations, Sophos Cloud Optix collaborates with major public cloud providers, including AWS, GCP, and VMware. It also offers API integrations, improving automation and streamlining cloud services for real-time data syncing and monitoring.
Pricing:
Pricing upon request
Pros:
- Comprehensive visibility into cloud assets across multiple cloud providers.
- Robust CSPM capabilities to identify and rectify misconfigurations swiftly.
- Integration with major cloud providers and API support facilitates improved monitoring and automation.
Cons:
- May have a steeper learning curve for those unfamiliar with cloud-native application protection platforms (CNAPP).
- Some users may desire more granular control over specific features or configurations.
- While it integrates with major cloud providers, organizations with hybrid environments may require additional configuration or tools.
12. Bitdefender - Best for multi-layered security modules
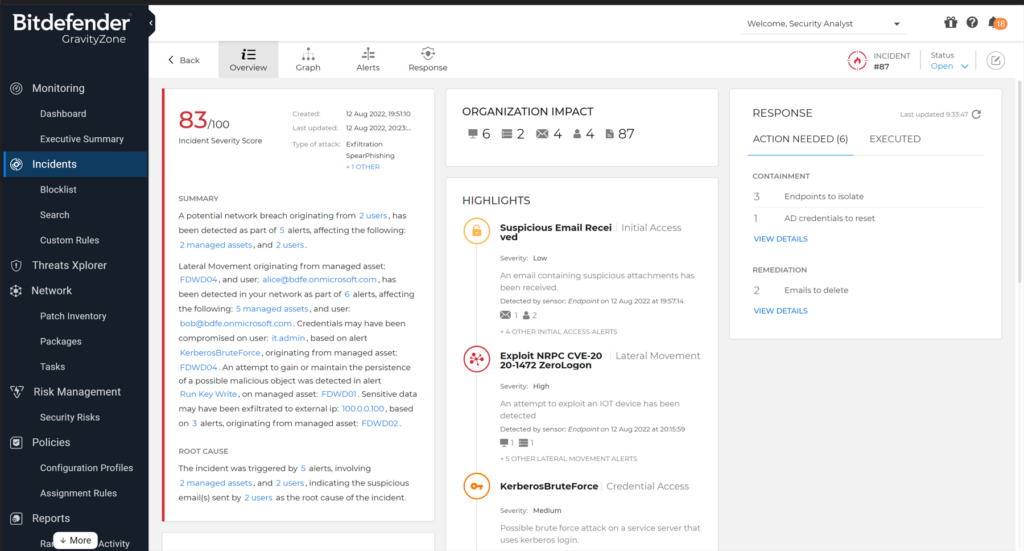
Bitdefender is a global cybersecurity leader offering a range of protection solutions for both individuals and organizations. Known for its robust, multi-layered security modules, Bitdefender provides comprehensive defense against a wide array of threats, making it a top pick for those seeking intricate and reliable security layers.
Why I Picked Bitdefender:
In my journey of evaluating various security tools, Bitdefender stood out, compelling me to select it for its reputation and performance. Judging by its features, customer feedback, and my own comparative analysis, it's evident that Bitdefender's intricate security modules set it apart. I am convinced that Bitdefender is the "Best for multi-layered security modules" due to its ability to offer numerous protective layers, effectively reducing the attack surface and guarding against diverse threats.
Standout features & integrations:
Bitdefender is lauded for its multi-layered approach to cybersecurity, encompassing anti-malware, firewall, endpoint protection, and cloud security posture management (CSPM). Its real-time protection capabilities combined with advanced machine learning techniques ensure swift detection and remediation of threats.
On the integration front, Bitdefender collaborates effectively with major public cloud providers, allowing for improved cloud security solutions. Its API integrations facilitate automation and improve workflows, catering to both on-premises and cloud-based environments.
Pricing:
Pricing upon request
Pros:
- Comprehensive multi-layered security offering protection against a variety of threats.
- Effective integrations with major cloud providers and versatile API support.
- Advanced machine learning techniques bolstering real-time threat detection.
Cons:
- The plethora of features might be overwhelming for users seeking simple protection solutions.
- While its cloud integrations are commendable, some businesses might require specific configurations for hybrid environments.
- Requires periodic updates to ensure protection against the latest threats, which might disrupt some users.
Other Cloud Workload Protection Platforms
Below is a list of additional cloud workload protection platforms that I shortlisted, but did not make it to the top 12. Definitely worth checking them out.
- Tanium - Good for unified endpoint management
- Nutanix Flow - Good for software-defined networking
- Lacework - Good for polygraph-based anomaly detection
- Fugue - Good for cloud infrastructure drift prevention
- Radware - Good for application delivery and security
- Alert Logic - Good for managed threat detection
- Sysdig Secure - Good for container and Kubernetes security
- Intezer - Good for genetic malware analysis
- Juniper Networks - Good for scalable network infrastructure solutions.
Selection Criteria for Cloud Workload Protection Platforms
Over the years, the expansion of cloud assets has led businesses to prioritize their security. In my journey, I've evaluated dozens of cloud workload protection platforms. Specifically, I was on the hunt for tools that integrate with private clouds, prioritize sensitive data protection, and adhere to the zero-trust security model. While many tools made impressive promises, only a few truly stood out in terms of core functionality, features, and usability. Here's a breakdown of what I looked for:
Core Functionality:
- Protection Across Various Cloud Models: The tool should cater to public, private, and hybrid cloud environments.
- Zero Trust Implementation: In line with Gartner's recommendations, the platform should implement a zero trust architecture, where every request is authenticated and validated.
- Data Safeguarding: Emphasis on protecting sensitive data, ensuring it remains uncompromised.
- Agentless Deployment: The ability to deploy the solution without the need to install agents on target systems.
Key Features:
- Real-time Threat Detection: Identifying threats as they emerge, not after the fact.
- Automated Compliance Checks: Assessing the environment against compliance standards and generating actionable reports.
- Integrated Firewall: A built-in firewall that protects the cloud environment from unwanted intrusions.
- Micro-segmentation: Dividing the cloud environment into secure segments to reduce the attack surface.
- Behavioral Analytics: Monitoring for unusual patterns or behaviors that might indicate a security breach.
Usability:
- Intuitive Dashboard: The dashboard should provide a comprehensive overview of the cloud environment's security posture, with easily accessible features.
- Role-based Access: It's essential that the tool offers role-based access that's straightforward to configure, ensuring that users only see what's relevant to their role.
- Efficient Onboarding: For such a sophisticated tool, there should be a well-structured learning library, training program, or wiki to help users get acquainted quickly.
- Proactive Customer Support: Given the evolving nature of threats, support teams should be agile, knowledgeable, and ready to assist.
By focusing on these criteria, I was able to sift through the multitude of available tools and zero in on those that truly offer value in safeguarding cloud workloads.
Most Common Questions Regarding Cloud Workload Protection Platforms
What are cloud workload protection platforms?
Cloud workload protection platforms (CWPPs) are security solutions designed to protect applications, data, and workloads running in cloud environments. They ensure that workloads, whether in IaaS, PaaS, or SaaS models, remain secure and compliant.
What are the benefits of using cloud workload protection platforms?
Using cloud workload protection platforms offer numerous advantages:
- Enhanced Security: They provide real-time protection against threats and misconfigurations in cloud environments.
- Comprehensive Visibility: Users gain a holistic view of their cloud assets, reducing the chances of oversight.
- Automated Compliance: Many CWPPs help in automating compliance checks, ensuring that workloads adhere to regulatory standards.
- Optimized Workflows: Integration capabilities, often through APIs, streamline security operations and improve DevOps workflows.
- Flexibility and Scalability: These platforms can easily scale with the growth of cloud assets, providing consistent protection.
How much do these tools typically cost?
Pricing for cloud workload protection platforms can vary significantly based on their features, the size of the organization, and the specific needs of the business. Some tools might offer a pay-as-you-go model while others could have a fixed monthly or annual subscription.
Can you explain the different pricing models for CWPPs?
Certainly. CWPPs often come with a variety of pricing models:
- Subscription-Based: A fixed fee is charged monthly or annually.
- Usage-Based: Pricing is based on the volume of cloud resources or workloads protected.
- Freemium: Basic features are provided for free, with advanced capabilities available at a premium.
- Perpetual License: A one-time fee provides indefinite use of the software.
What's the typical range of pricing for these platforms?
The pricing can range from free (for freemium models with basic functionalities) to several hundred dollars per user/month for more advanced and comprehensive solutions. Enterprise-grade solutions with extensive features can cost even more.
Which are some of the cheapest and most expensive software in this category?
While specific tools and their pricing can vary over time, as of my last training cut-off in 2021, some of the more affordable options include tools like "Orca Security" or "Illumio" for basic plans. On the higher end, platforms like "Palo Alto Networks' Prisma Cloud" or "VMware's CloudHealth" tend to be more expensive due to their extensive feature sets.
Are there any free tool options available?
Yes, some CWPPs offer freemium models where users can access basic functionalities for free. However, for more advanced features or larger workloads, a premium might be charged. Always check the specific tool's website for the most up-to-date information on its offerings.
Other Cloud Workload Protection Platforms Reviews
Summary
In the rapidly evolving digital landscape, securing cloud assets has never been more critical. Cloud Workload Protection Platforms (CWPPs) are specifically designed to fortify applications, data, and workloads in cloud environments. With features ranging from real-time threat protection to automated compliance checks, these platforms offer a robust line of defense for organizations looking to safeguard their cloud-based operations. However, with a myriad of options available, understanding the benefits, pricing models, and individual tool capabilities is essential in making an informed decision.
Key Takeaways for Your Buyer's Guide:
- Consider Your Needs First: The best CWPP for an organization hinges on specific requirements, such as the scale of cloud assets, compliance needs, and integration preferences.
- Pricing Flexibility: Different CWPPs offer varied pricing models, from subscription-based to usage-based. It's crucial to understand and align with the financial structure that suits your organization's budget and growth projections.
- Look Beyond Price: While cost is an essential factor, diving deep into features, scalability, integration capabilities, and user feedback can provide a comprehensive view, ensuring you choose a tool that offers genuine value.
What do you think?
Absolutely, the landscape of cloud workload protection platforms is vast and ever-evolving. While I've put my best foot forward to curate this list, there's always the possibility of a hidden gem that's escaped my radar.
If you've come across a tool that deserves a mention or have personal experiences with one that's made a significant impact on your operations, please do share. Your insights and recommendations are invaluable, and together, we can create a more comprehensive and beneficial resource for everyone.
