12 Best Internet Security Software Shortlist
After meticulous evaluation, I've handpicked 12 internet security software that truly address your online challenges.
- Cisco Secure Firewall Threat Defense Virtual - Best for advanced threat protection
- AirMagnet Enterprise - Best for wireless network troubleshooting
- SonicWall - Best for real-time breach detection
- McAfee Virtual Network Security Platform - Best for integrated intrusion prevention
- Check Point IPS - Best for multi-layered protection strategy
- ThreatBlockr - Best for adaptive threat response
- Palo Alto VM-Series - Best for virtualized network security
- Blumira Automated Detection & Response - Best for rapid security event response
- CrowdSec - Best for community-powered security
- ExtraHop - Best for real-time data analytics
- AlienVault USM - Best for unified security management
- Trend Micro Hybrid Cloud Security - Best for hybrid cloud environments
Navigating the vast digital landscape, I've seen firsthand the relentless challenges of online threats. From hackers deploying ransomware to the elusive malware, adware, and spyware threats for webcam protection, the digital world can be a dangerous terrain. I lean heavily on real-time protection to guard my digital domain, as it ensures constant vigilance against malicious intrusions.
It's not just about antivirus protection; it's the comprehensive anti-malware and ransomware protection that secures every crevice of my operating system, maintaining optimal system performance. I used to grapple with the fear of online vulnerabilities, but with total security tools on my side, especially the anti-malware and best antivirus options, I now traverse the web with an assured stride.
What is Internet Security Software?
Internet security software is a suite of programs designed to safeguard users' computers and online activities from malicious dark web threats. Typically incorporating additional features like virus detection, firewall protection, and anti-phishing, this software plays a crucial role in defending against a broad spectrum of cyber-attacks.
The best internet security suites, which often combine the best antivirus software with tools like virtual private network or VPN services, apps, and a password manager, offer a defense mechanism. From individuals safeguarding personal data on home computers to large corporations protecting vast amounts of sensitive information, many users rely on internet security software. Their primary goal: ensure safe browsing, secure transactions, and the integrity of digital assets in an increasingly interconnected world.
Overview of the 12 Best Internet Security Software
1. Cisco Secure Firewall Threat Defense Virtual - Best for advanced threat protection
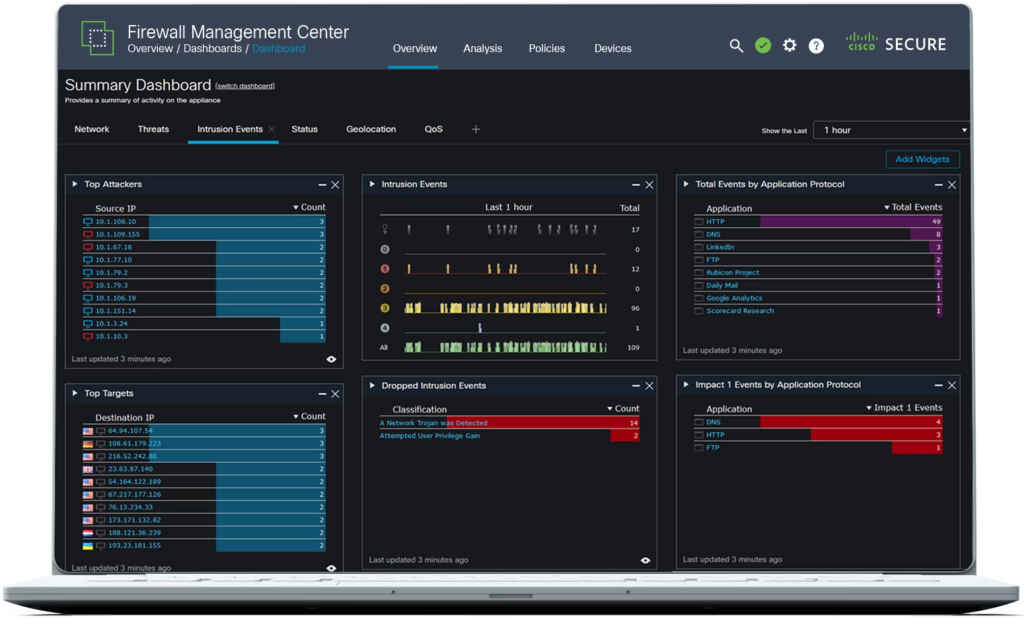
Cisco Secure Firewall Threat Defense Virtual is a comprehensive solution designed to safeguard organizations from cyber threats. This virtual firewall provides layered protection against sophisticated attacks, corroborating its position as being best suited for advanced threat protection.
Why I Picked Cisco Secure Firewall Threat Defense Virtual:
I chose the Cisco Secure Firewall Threat Defense Virtual after careful evaluation of several options in the market. This tool's advanced capabilities and Cisco's reputation in the cybersecurity domain helped determine its inclusion in the list, making it best for organizations that prioritize high-end security against sophisticated attacks.
Standout features & integrations:
The most significant features of this tool include its deep packet inspection, intrusion prevention system, and geo-filtering capabilities. Cisco Secure Firewall Threat Defense Virtual integrates with Cisco's security ecosystem and third-party threat intelligence platforms for maximum protection.
Pricing:
Pricing upon request
Pros:
- Comprehensive layered protection against a myriad of cyber threats and scams
- Integrates well with other Cisco security products and third-party platforms
- Real-time threat intelligence updates
Cons:
- May require skilled professionals for optimal configuration
- Integration with non-Cisco products may present slowdowns
- Potential high cost for smaller businesses due to brand premium.
2. AirMagnet Enterprise - Best for wireless network troubleshooting
AirMagnet Enterprise is a dedicated tool for monitoring, analyzing, and maintaining wireless networks. Its emphasis on troubleshooting capabilities ensures network administrators can pinpoint and address issues efficiently, underlining its expertise in wireless network troubleshooting.
Why I Picked AirMagnet Enterprise:
I selected AirMagnet Enterprise after a rigorous comparison of the wireless network tools available. I believe this tool is best for wireless network troubleshooting due to its specialized set of tools and its ability to provide detailed insights into network health and performance.
Standout features & integrations:
Key features of AirMagnet Enterprise include spectrum analysis, dedicated troubleshooting tools, and real-time alerts on potential network threats or issues. As for integrations, AirMagnet Enterprise works effectively with a range of network monitoring tools and is compatible with multiple wireless hardware vendors, ensuring versatility in diverse network environments.
Pricing:
Pricing upon request
Pros:
- Spectrum analysis allows for in-depth understanding of network performance
- Real-time alerts enable quick action on potential problems
- Compatibility with multiple wireless hardware vendors ensures flexibility in deployment
Cons:
- Might present a learning curve for those unfamiliar with advanced networking tools
- May be overkill for very small networks or basic use cases
- Cost could be prohibitive for some organizations due to its specialized nature.
3. SonicWall - Best for real-time breach detection
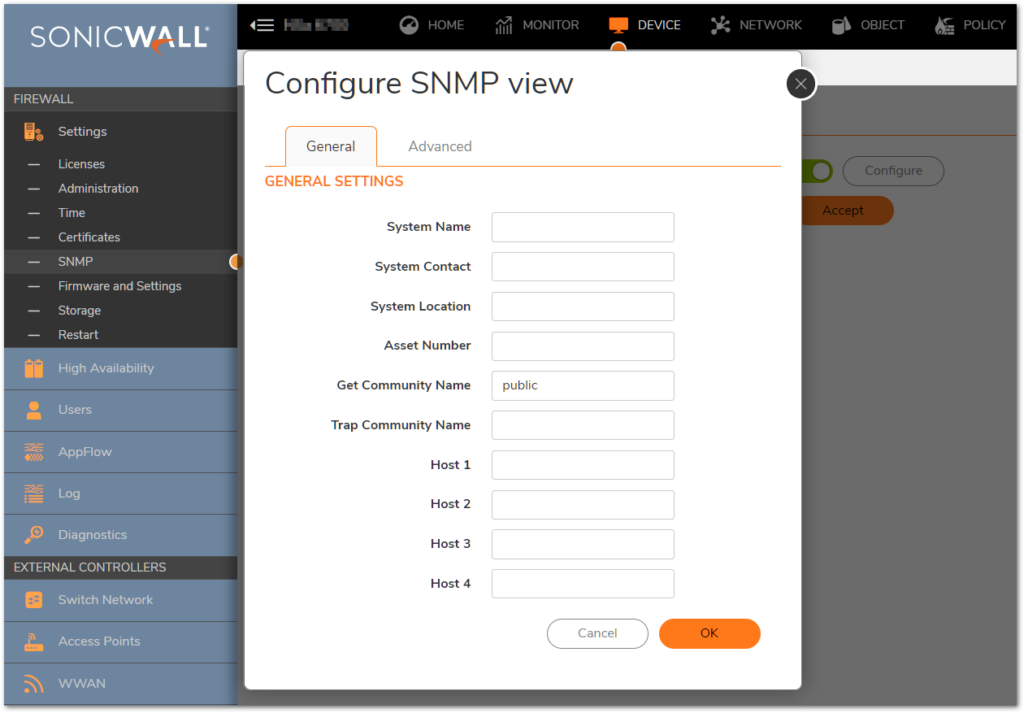
SonicWall offers a robust set of security solutions designed to protect organizations from a wide range of cyber threats. Its primary strength lies in delivering immediate alerts on potential breaches, making it a top choice for those prioritizing real-time breach detection.
Why I Picked SonicWall:
When selecting a security solution for this list, SonicWall stood out due to its proven track record and dedicated features tailored to detect breaches as they happen. manySonicWall is best for real-time breach detection given its timely response mechanism and detailed threat analysis.
Standout features & integrations:
SonicWall's most notable features include its advanced threat protection, intrusion prevention system, and high-speed SSL inspection. Regarding integrations, SonicWall can work with various network monitoring tools, and its Capture Advanced Threat Protection (ATP) service ensures compatibility with a multitude of threat intelligence platforms.
Pricing:
Pricing upon request
Pros:
- Advanced threat protection provides a layered defense mechanism
- Intrusion prevention system aids in thwarting potential attacks
- High-speed SSL inspection allows for secure data transmission without compromising speed
Cons:
- The interface may be complex for new users
- Certain features might demand specialized training for full utilization
- Potential cost concerns for smaller enterprises due to its comprehensive feature set.
4. McAfee Virtual Network Security Platform - Best for integrated intrusion prevention
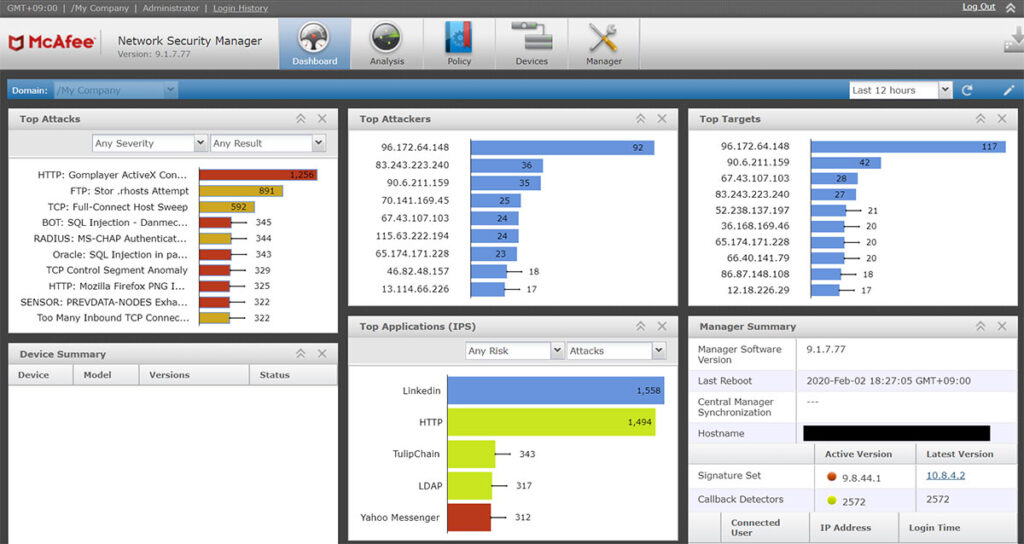
McAfee Virtual Network Security Platform delivers a comprehensive security solution that provides both detection and prevention against cyber threats in virtual environments.
Why I Picked McAfee Virtual Network Security Platform:
In my process of choosing a reliable network security platform, McAfee's offering surfaced as a top contender because of its holistic approach to intrusion prevention. I'm convinced that it's best for integrated intrusion prevention, given its focus on proactive countermeasures against potential breaches.
Standout features & integrations:
Key features of the McAfee Virtual Network Security Platform include real-time threat intelligence, advanced malware detection, and behavior analytics. On the integration front, the platform works in conjunction with McAfee's suite of security tools, enhancing its capabilities, and it also has built-in compatibility with various third-party network monitoring and management tools.
Pricing:
Pricing upon request
Pros:
- Real-time threat intelligence ensures up-to-date defense mechanisms
- Advanced malware detection can identify and neutralize even the most recent threats
- Behavior analytics aids in predicting and preempting potential threat vectors
Cons:
- Might be challenging for those not familiar with McAfee's ecosystem
- Deployment in very large networks could demand considerable resources
- Potential higher cost relative to more basic security solutions.
5. Check Point IPS - Best for multi-layered protection strategy
Check Point IPS is a multi-layered security system that defends networks from advanced threats and attacks. Its comprehensive approach targets vulnerabilities at different stages, providing effective protection.
Why I Picked Check Point IPS:
Check Point IPS emerged as a notable candidate due to its established reputation in the security domain. Its dedication to a multi-layered defense model sets it apart, covering potential gaps that single-layered systems might miss.
Standout features & integrations:
Check Point IPS is renowned for its threat intelligence capabilities, allowing for the timely identification and mitigation of risks. Additionally, the system's ability to provide granular control over security policies enhances its adaptability. Integration-wise, it pairs with the broader Check Point software suite, facilitating an interconnected security ecosystem.
Pricing:
Pricing upon request
Pros:
- Threat intelligence capabilities offer a proactive stance against vulnerabilities
- Granular control over policies ensures tailored security measures
- Extensive integration within the Check Point ecosystem augments overall defense mechanisms
Cons:
- Might have a steeper learning curve for newcomers
- Can be resource-intensive for smaller network infrastructures
- Occasional false positives may require manual oversight.
6. ThreatBlockr - Best for adaptive threat response
ThreatBlockr offers a dynamic security solution aimed at recognizing and mitigating cybersecurity threats. Its proficiency lies in its adaptive response mechanism, allowing it to quickly adjust and respond to varying threat landscapes, making it the top choice for an adaptable cybersecurity approach.
Why I Picked ThreatBlockr:
When determining the most capable tools for this list, ThreatBlockr caught my attention. Its unique adaptive response mechanism sets it apart, as not all tools possess this dynamism in threat mitigation. Given this strength, ThreatBlockr is the best option for those prioritizing adaptive threat response.
Standout features & integrations:
One of ThreatBlockr's defining features is its real-time threat analysis, enabling the system to make prompt decisions in high-risk situations. As for integrations, ThreatBlockr collaborates efficiently with prominent security information and event management (SIEM) platforms, enhancing its data analytics capabilities.
Pricing:
Pricing upon request
Pros:
- Real-time threat analysis ensures timely reactions to potential risks
- Automated response configurations reduce dependency on manual oversight
- Efficient collaborations with leading SIEM platforms enhance its scope
Cons:
- Might not be suitable for businesses seeking a static security setup
- The adaptive nature might require occasional recalibrations
- Complex user interface can pose challenges for beginners.
7. Palo Alto VM-Series - Best for virtualized network security
Palo Alto VM-Series is tailored to safeguard virtualized environments from potential security threats. Focusing on the nuances of virtual networks delivers rigorous protection, making it particularly adept at ensuring virtualized network security.
Why I Picked Palo Alto VM-Series:
After sifting through various cybersecurity tools, Palo Alto VM-Series emerged as a compelling choice. Its dedication to securing virtualized networks, instead of a one-size-fits-all approach, truly set it apart. Given this specialized focus, I'm convinced that Palo Alto VM-Series is the "Best for virtualized network security", catering to organizations relying heavily on virtual infrastructure.
Standout Features & Integrations:
Palo Alto VM-Series shines with its Threat Prevention engine that detects and stops threats in virtual environments. Additionally, its WildFire feature offers cloud-based malware analysis. Regarding integrations, VM-Series blends with major cloud providers like AWS, Azure, and Google Cloud, ensuring protection remains consistent regardless of the virtual environment.
Pricing:
Pricing upon request
Pros:
- Focused Threat Prevention for virtualized settings
- Integration with major cloud providers ensures widespread compatibility
- WildFire offers an added layer of malware analysis and prevention
Cons:
- Might have a steeper learning curve for users new to Palo Alto Networks
- Primarily virtual-focused, which might not cater to hybrid environments
- Potential overhead costs associated with advanced features
8. Blumira Automated Detection & Response - Best for rapid security event response
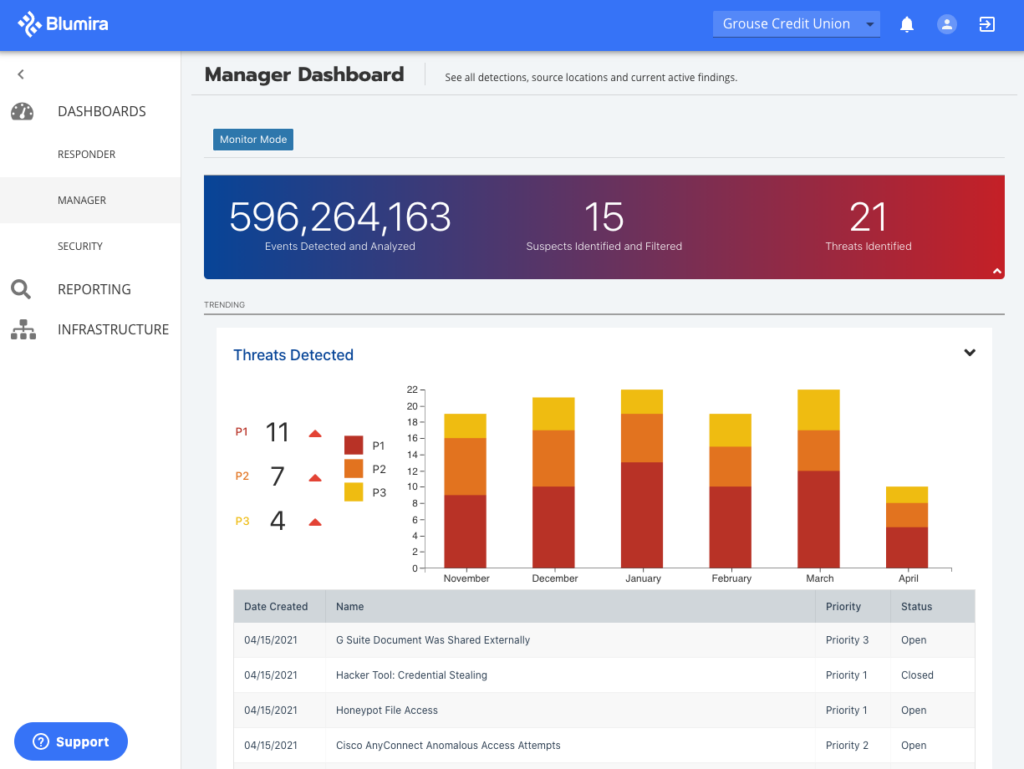
Blumira Automated Detection & Response is a solution designed to identify and promptly address security events. With an emphasis on swiftness and accuracy, this tool perfectly aligns with the imperative of rapid security event responses.
Why I Picked Blumira Automated Detection & Response:
In my quest for a security tool that was both effective and prompt, Blumira stood out. Among a myriad of solutions, the sheer speed and precision of Blumira's detection and response mechanisms captured my attention. This focus on quick, accurate responses convinces me of its standing as the "Best for rapid security event response.”
Standout Features & Integrations:
Blumira boasts a robust detection mechanism that uses behavioral analytics to spot anomalies. Its streamlined response workflow ensures that once threats are identified, they are dealt with expeditiously. Integration-wise, Blumira is compatible with various platforms, including AWS, Office 365, and various endpoint protection solutions.
Pricing:
Pricing upon request
Pros:
- Utilizes behavioral analytics for heightened detection accuracy
- Swift response workflow aids in rapid threat mitigation
- Broad compatibility with platforms like AWS and Office 365
Cons:
- Might necessitate training for optimal utilization
- The efficiency could vary depending on the network environment
- Potential additional costs for advanced features or larger networks
9. CrowdSec - Best for community-powered security
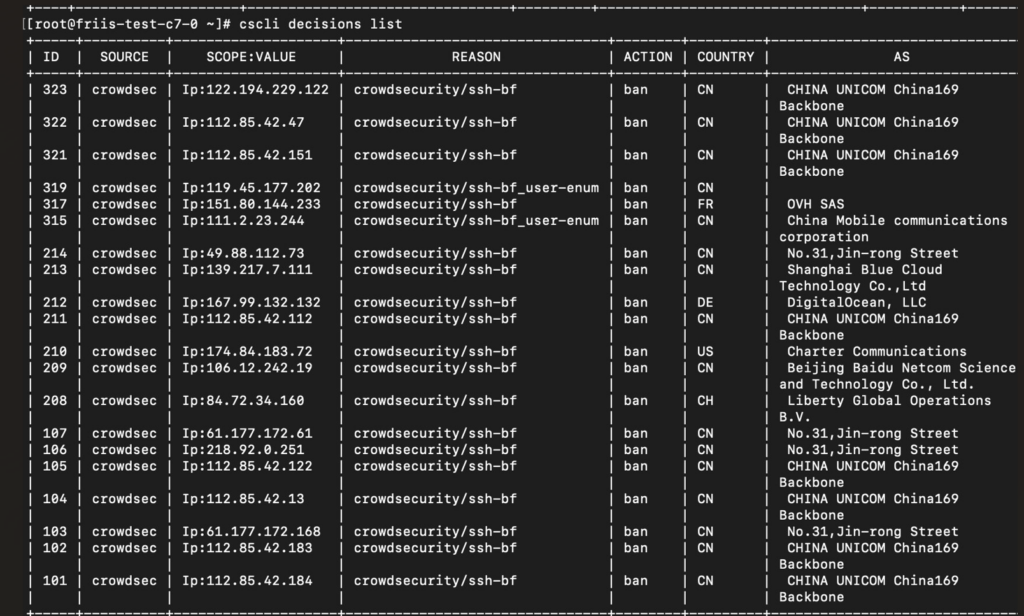
CrowdSec is an open-source, community-driven security solution that detects and responds to threats using collective intelligence. Its foundation on the principle of community collaboration enhances the security approach and resonates with the idea of community-powered security.
Why I Picked CrowdSec:
When determining which tool to recommend, CrowdSec caught my attention due to its unique community-driven model. The power of collective intelligence and knowledge-sharing among users make it distinctly different from other security tools on the market. This firm reliance on the community is precisely why I believe it deserves the title "Best for community-powered security".
Standout Features & Integrations:
CrowdSec leverages a behavior analysis system to pinpoint malicious activities. It also has a bouncer system, which allows automated responses to identified threats, ensuring timely action. Regarding integrations, CrowdSec is compatible with popular platforms like WordPress, Nginx, and Docker, expanding its applicability across various environments.
Pricing:
From $10/user/month (billed annually)
Pros:
- Emphasizes the power of collective intelligence for enhanced detection
- Broad compatibility with major platforms enhances adaptability
- Bouncer system ensures swift and automated responses
Cons:
- Being open-source, might need dedicated resources for optimal maintenance
- Some features might be complex for new users
- Reliance on community can sometimes delay updates or patches
10. ExtraHop - Best for real-time data analytics
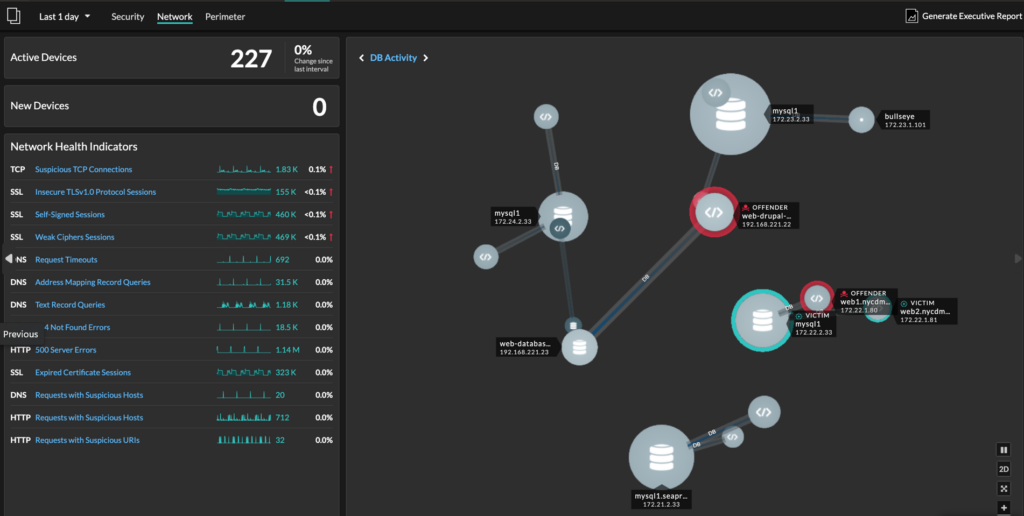
ExtraHop provides real-time data analytics for businesses to quickly understand their operations and security status. It excels in handling large data sets for immediate insights.
Why I Picked ExtraHop:
While comparing different tools, I selected ExtraHop because of its unmatched capability to deliver on-the-fly data analysis. Its prowess in crunching large datasets quickly and offering actionable insights makes it stand apart. Given its emphasis on real-time processing, it's clear why this tool is best suited for real-time data analytics.
Standout Features & Integrations:
ExtraHop shines with its advanced machine-learning capabilities, allowing it to detect anomalies and provide proactive alerts. Additionally, its deep packet inspection offers granular visibility into network traffic, assisting businesses in identifying potential issues before they escalate. Integrating with platforms such as AWS, Microsoft Azure Windows 10, even Linux, and Google Cloud, ExtraHop ensures its utility across diverse infrastructure environments.
Pricing:
Pricing upon request
Pros:
- Advanced machine learning offers proactive anomaly detection
- Deep packet inspection provides detailed network visibility
- Broad cloud compatibility ensures adaptability to various infrastructures
Cons:
- Might be over-complex for small businesses with simpler needs
- Initial setup can be intricate for those unfamiliar with the domain
- Depending on deployment, it might require dedicated resources for optimal performance
11. AlienVault USM - Best for unified security management
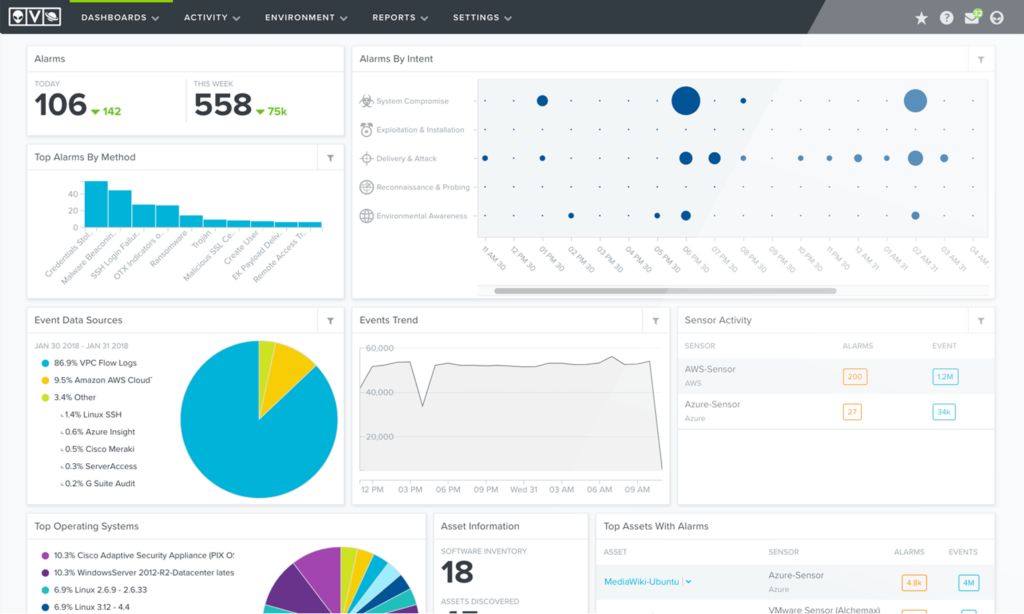
AlienVault USM offers all-in-one security management for businesses, delivering extensive operations and unified protection.
Why I Picked AlienVault USM:
When determining which tools to include on this list, AlienVault USM came forward due to its holistic approach to security. Its integrated suite, comprising asset discovery, vulnerability assessment, intrusion detection, and more, offers a distinct advantage. Based on my judgment, the very essence of this tool provides a 'unified' platform makes it optimal for businesses seeking comprehensive security management.
Standout Features & Integrations:
AlienVault USM boasts a centralized dashboard that provides a bird's-eye view of an organization's security posture. Its in-built threat intelligence, updated regularly, ensures that organizations are always prepared against emerging threats. AlienVault USM integrates with various third-party tools, including those for SIEM, logging, and ticketing, fortifying its position as a versatile security solution.
Pricing:
Pricing upon request
Pros:
- Centralized dashboard offers clear visibility into security operations
- Regularly updated threat intelligence ensures proactive defense
- Wide-ranging third-party integrations augment its versatility
Cons:
- Might pose a learning curve for smaller teams or those new to unified security platforms
- Some features could be overwhelming for organizations with basic security needs
- Depending on the scale of deployment, hardware requirements might be significant
12. Trend Micro Hybrid Cloud Security - Best for hybrid cloud environments
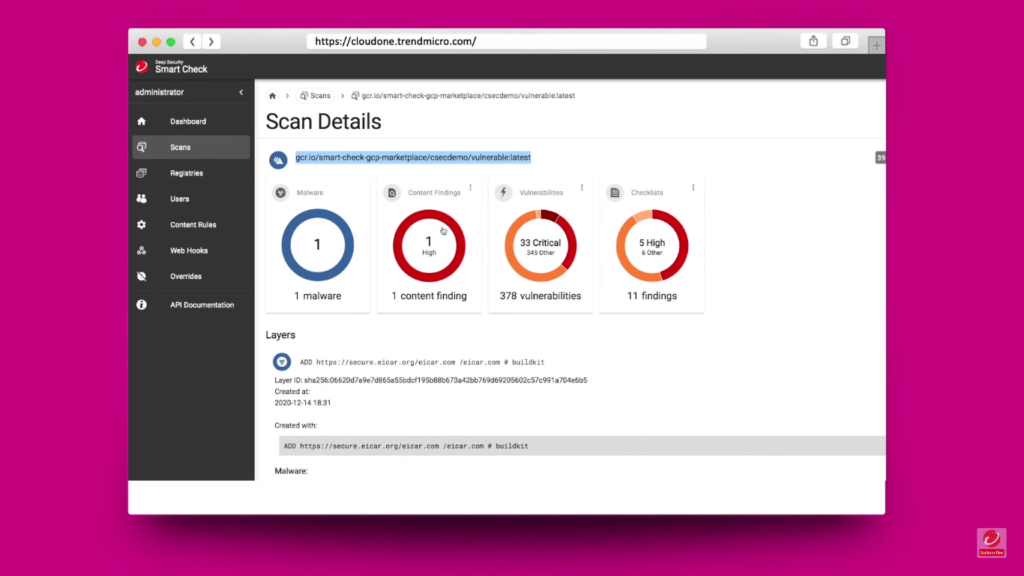
Trend Micro Hybrid Cloud Security offers a reliable solution to protect applications and data in hybrid cloud environments. It's highly recommended for those using hybrid cloud contexts.
Why I Picked Trend Micro Hybrid Cloud Security:
In selecting tools for this list, Trend Micro Hybrid Cloud Security resonated strongly due to its specialized focus on the hybrid cloud. I determine that this tool is particularly adept at securing hybrid cloud systems, which are inherently complex and present unique challenges.
Standout Features & Integrations:
Trend Micro's solution excels with its Deep Security feature, which offers a suite of capabilities from intrusion detection to vulnerability protection. Its built-in automation also reduces manual input, facilitating smoother security operations. Notably, the platform integrates effectively with major cloud service providers such as AWS, Azure, and Google Cloud, which ensures that security measures align well with cloud infrastructure operations.
Pricing:
Pricing upon request
Pros:
- Specialized focus on the intricacies of hybrid cloud security
- Deep Security feature provides a comprehensive range of protection mechanisms
- Integrations with major cloud providers enable security operations
Cons:
- Businesses without hybrid environments might find some features redundant
- The learning curve might be steep for those unfamiliar with cloud-specific threats
- Potential over-reliance on automation could reduce visibility for some users
Other Noteworthy Internet Security Software
Below is a list of additional internet security software that I shortlisted, but did not make it to the top 12. Definitely worth checking them out.
- Forcepoint Next-Gen Firewall - Good for behavior-driven threat protection
- Armor Anywhere - Good for scalable cloud security solutions
- FireEye Network Security and Forensics - Good for advanced threat intelligence
- Ossec - Good for open-source intrusion detection
- Corelight - Good for comprehensive network traffic analysis
- vSRX - Good for virtualized firewall protection
- B1 Platform by CloudCover - Good for multi-cloud security automation
- 5nine Cloud Security - Good for Hyper-V and Azure cloud protection
- Sophos Firewall - Good for synchronized security responses
- Check Point Next Generation Firewalls (NGFWs) - Good for multi-layered protection strategies
- pfSense - Good for customizable open-source firewall solutions
- WatchGuard Network Security - Good for user-focused security services
- VMware NSX - Good for network virtualization and security
- NG Firewall - Good for combined network control features
- Perimeter 81 - Good for firewall as a service connectivity
Selection Criteria for Choosing Internet Security Software
When it comes to selecting the ideal network security software, the criteria aren't straightforward. Having navigated through countless options in this domain, I've done independent tests and evaluated many of these tools. After trying out more than 50 tools, I've zeroed in on certain specific functionalities and criteria that truly matter. Let's delve deeper into what I was really looking for:
Core Functionality
- Threat Detection: The primary purpose of a security tool, which involves identifying and classifying potential threats or anomalies.
- Protection & Prevention: Not only detect but prevent unauthorized access or data breaches.
- Response & Mitigation: In the event of a security issue, the tool should have measures to immediately respond and mitigate the risk.
- Continuous Monitoring: The tool should be able to monitor network traffic and user activities 24/7.
Key Features
- Behavioral Analytics: This means the tool uses AI or similar technologies to understand the normal behavior and flag anomalies.
- Multi-cloud Compatibility: Given the rise of hybrid and multi-cloud infrastructures, the software should be compatible with various cloud service providers.
- End-to-End Encryption: Ensuring data, both at rest and in transit, is encrypted.
- Role-Based Access Control (RBAC): An essential feature where access to network resources is granted based on roles within an organization.
- Advanced Threat Intelligence: Tools should provide insights and context, enabling proactive defense strategies.
- Integrated Incident Management: Ability to handle an incident from detection to resolution within the same platform.
Usability
- Intuitive Dashboard: For a security tool, real-time data visualization is crucial. A centralized dashboard that gives an overview of all network activities, threats, and status reports can be invaluable.
- Flexible Alert Configurations: The tool should allow customization of alerts based on the severity of threats or based on specific network segments.
- Streamlined Onboarding: Especially for complex enterprise solutions, there should be a structured training program, learning library, or tutorials to get users started.
- Robust Customer Support: Given the critical nature of security tools, round-the-clock support, preferably with a live response option, is essential.
- Configurable Role-Based Access: As mentioned earlier, an employee management tool should have role-based access that promotes ease of use to set up and modify efficiently.
The above criteria are based on the essentials, but remember, the best fit will always depend on an organization's specific requirements and existing infrastructure.
Most Common Questions Regarding Internet Security Software (FAQs)
What are the benefits of using internet security software?
Internet security software offers a myriad of advantages for both individuals and organizations:
- Malware Protection: These tools safeguard your devices, such as Mac and iPhone for apple, against viruses, worms, trojans, and other malicious software.
- Data Theft Prevention: By encrypting your data and monitoring network traffic, they prevent unauthorized access and data breaches. One example is safeguarding threat for identity stealing, promoting identity theft protection.
- Safe Online Transactions: Enhance security during online banking, shopping, or any transaction that involves sensitive information.
- Phishing Protection: Detect and block fake social media websites or emails that try to steal your personal information.
- Parental Controls: Some tools offer features to restrict and monitor children's internet usage, ensuring they have a safe online experience.
How much do internet security software tools typically cost?
The cost of internet security software can vary widely based on the features offered, the number of devices covered, and whether they cater to individual or corporate needs.
What are the common pricing models for these tools?
Most internet security software tools follow one of these pricing models:
- Subscription-Based: Often billed monthly or annually, covering updates and customer support.
- Per Device Licensing: Pricing is determined by the number of devices you want to protect.
- Freemium: Basic protection is offered for free, with advanced features available in paid versions.
What's the typical price range for these tools?
The price can range anywhere from free versions to upwards of $100 per year for premium individual suites. Enterprise-level solutions can go into the thousands, depending on the size of the organization and the extent of features required.
Which are some of the cheapest and most expensive software options?
The most affordable options often include tools like Avast Free Antivirus or AVG AntiVirus Free. On the higher end of the spectrum, solutions like Norton 360 Deluxe or McAfee Total Protection can be more expensive due to the comprehensive protection they offer.
Are there any free internet security software options?
Yes, there are several free options available. Avast Free Antivirus, AVG AntiVirus Free, and Kaspersky Free offer basic protection against common threats. However, investing in a paid version is often recommended for advanced features and comprehensive protection.
Other Internet Security Software-Related Reviews
Summary
Securing your Wi-Fi or internet is crucial nowadays. Our buyer's guide streamlines security software choices, empowering you to make an informed decision based on your requirements and long-term efficacy.
Key Takeaways:
- Core Functionality Matters: Before diving into the plethora of features, first ensure that the software covers your fundamental security needs. Whether it's firewall protection, intrusion detection, or real-time monitoring, prioritize the non-negotiable core functions for your environment.
- Usability and Support: Even the most feature-rich software can fall short if it's not user-friendly or lacks proper support. Look for intuitive interfaces tailored to the specific demands of security tasks. Additionally, robust customer support can be invaluable, especially during critical moments.
- Pricing Transparency: While it's tempting to lean towards the most affordable option, it's crucial to understand the pricing model. Whether it's per user, per device, either a laptop or computer a mobile device on Android and iOS, or a different model altogether, be clear on what you're paying for. Additionally, always be on the lookout for hidden costs or potential price hikes in the future.
What Do You Think?
While we've endeavored to provide a comprehensive guide, the realm of internet security software is vast and ever-evolving. We value the collective knowledge of our readers. If there's a tool you've found invaluable and you think it deserves a spot on our list, please let us know. Your suggestions help us refine our guides and serve the community better. We look forward to your recommendations!
