12 Best Encryption Key Management Software Shortlist
After careful evaluation, I've curated a list of the 12 best encryption key management software that are tailored to address your security system, needs.
- Townsend Security Alliance Key Manager - Best for centralized key lifecycle control
- WinMagic SecureDoc Enterprise Server - Best for enterprise-wide encryption needs
- Vormetric Data Security Platform - Best for robust data-at-rest protection
- Virtru - Best for data protection with privacy engineering
- Box KeySafe - Best for granular encryption controls in cloud storage
- Akeyless Vault Platform - Best for zero-trust encryption key management
- Azure Key Vault - Best for Azure cloud integration and security
- Cloud Key Management - Best for Google Cloud users seeking native key services
- Verimatrix Key Shield - Best for multifaceted cybersecurity solutions
- ManageEngine Key Manager Plus - Best for IT teams managing SSH and SSL keys
- AWS Key Management Service - Best for AWS ecosystem key management
- Oracle Cloud Infrastructure Vault - Best for Oracle-centric enterprise security
Navigating the realm of encryption key management can be intricate. From on-premises to cloud-based solutions, the choice often rests between maintaining data encryption manually or leveraging automation. When I delved into Windows systems, I was fascinated by the diversity of algorithms, including blockchain, integrated within various tools. Trust me, these tools are the answer to your data security challenges.
What Is an Encryption Key Management Software?
Encryption key management software ensures the secure generation, storage, distribution, rotation, and retirement of encryption keys in digital security systems. These tools play a crucial role in protecting sensitive information from unauthorized access and potential breaches.
Typically utilized by organizations handling confidential data, such as financial institutions, healthcare providers, and tech companies, this software helps maintain the integrity and privacy of data in transit and at rest. By managing and safeguarding cryptographic keys, these solutions enable businesses to uphold regulatory compliance and fortify their cybersecurity stance against potential threats.
A reliable cloud key management service meets compliance requirements, easily functions across data centers, and ensures encrypted data remains impenetrable. With enterprise key management, the significance of timely notifications and safeguarding the private key is paramount.
Overviews of the 12 Best Encryption Key Management Software
1. Townsend Security Alliance Key Manager - Best for centralized key lifecycle control
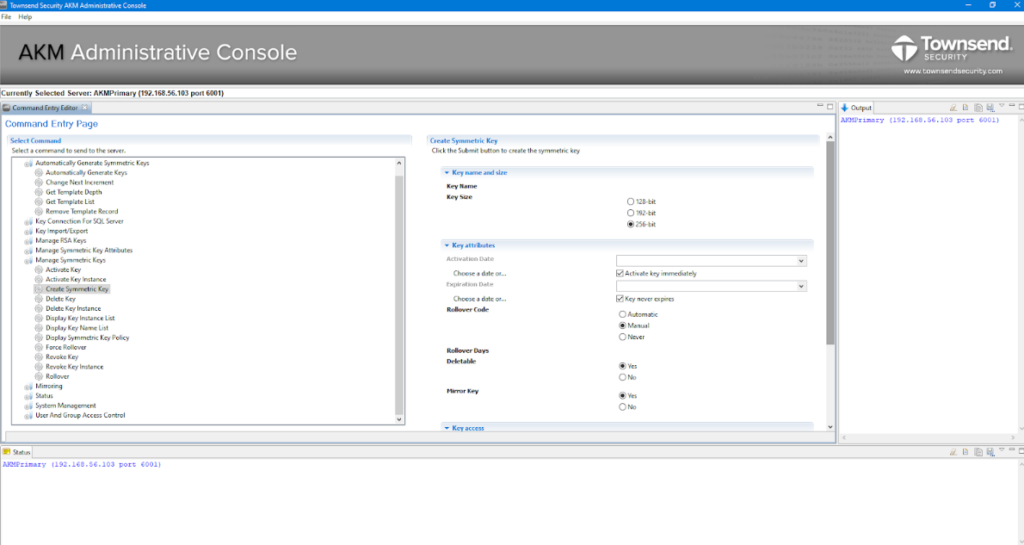
Townsend Security Alliance Key Manager is a robust tool that centralizes the management of encryption keys, ensuring secure generation, storage, distribution, and retirement. The platform specifically stands out for its emphasis on controlling the entire lifecycle of keys, affirming its position as best for centralized key lifecycle control.
Why I Picked Townsend Security Alliance Key Manager:
I chose Townsend Security Alliance Key Manager after carefully comparing various encryption key management solutions. Its focus on offering centralized control over every phase of key management, from generation to retirement, made it distinct in my judgment.
This centralized approach directly caters to organizations that demand streamlined processes, thus solidifying its role as the best choice for centralized key lifecycle control.
Standout Features & Integrations:
Alliance Key Manager boasts automated key rotation, stringent access controls, and real-time key mirroring, ensuring that keys are always available and secure. Moreover, it consistently adheres to industry benchmarks like FIPS 140-2 and PCI DSS, offering confidence to businesses needing to maintain strict compliance.
On the integration front, the platform easily melds with a vast array of enterprise applications and databases. Notably, SQL Server, Oracle, and MySQL work with this manager. Additionally, it offers out-of-the-box integrations with popular cloud ecosystems such as AWS and Azure, accommodating both hybrid and multi-cloud setups.
Pricing:
Pricing upon request
Pros:
- Comprehensive centralized key management functionality
- Adherence to rigorous industry compliance standards like FIPS 140-2 and PCI DSS
- Broad integration capabilities across enterprise applications, databases, and cloud solutions
Cons:
- Absence of readily available pricing details
- Potential complexity for smaller establishments
- Possible learning curve for those unfamiliar with key management systems
2. WinMagic SecureDoc Enterprise Server - Best for enterprise-wide encryption needs
The WinMagic SecureDoc Enterprise Server provides a comprehensive encryption solution tailored for expansive organizational infrastructures. Recognizing the diverse encryption requirements of vast enterprises, it is specifically crafted to serve the unique challenges of enterprise-wide encryption needs.
Why I Picked WinMagic SecureDoc Enterprise Server:
In the process of selecting the most effective encryption tools, I was particularly drawn to WinMagic SecureDoc Enterprise Server due to its capability to integrate across broad organizational setups.
What caught my attention was its flexibility to adapt and the robustness it offers to larger enterprises. Given its proficiency in handling large-scale encryption scenarios, I am convinced it stands as the best for enterprise-wide encryption needs.
Standout Features & Integrations:
SecureDoc Enterprise Server is endowed with multi-OS support, offering businesses the flexibility to work across various operating systems without hindrance. It employs full disk encryption, ensuring data-at-rest is as secure as it can be. Furthermore, its pre-boot network authentication feature stands out, providing an additional layer of security even before the OS loads.
For integrations, this platform boasts compatibility with a host of enterprise infrastructure elements, including Active Directory, LDAP, and SIEM systems. Moreover, its adaptability to various endpoints, be it PCs, servers, or mobile devices, ensures that enterprises have a holistic encryption solution in place.
Pricing:
Pricing upon request
Pros:
- Flexibility with multi-OS support
- Robust full disk encryption ensuring improved data-at-rest security
- Easy integration with various enterprise infrastructure elements
Cons:
- Pricing details are not directly accessible
- Might be overly complex for small businesses
- Requires technical proficiency for optimum utilization
3. Vormetric Data Security Platform - Best for robust data-at-rest protection
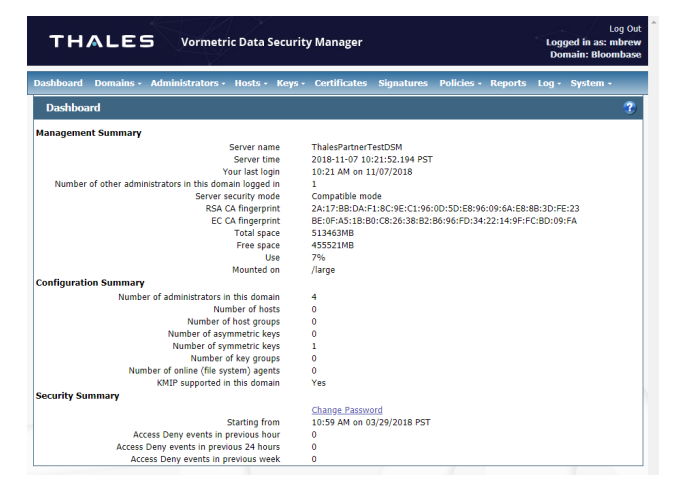
The Vormetric Data Security Platform stands as an encryption stalwart, focusing on defending data at rest. It acknowledges the necessity of safeguarding idle data, which often becomes an easy target for threats, and offers solutions tailored for this very purpose.
Why I Picked Vormetric Data Security Platform:
I chose the Vormetric Data Security Platform because, in the myriad of encryption tools, its dedication to protecting data at rest stood out to me. It's not just another encryption tool; it's a platform built with a deliberate focus.
As businesses grapple with varied threat vectors, Vormetric's emphasis on data-at-rest protection is both timely and critical, leading me to determine it as the best in this specific arena.
Standout Features & Integrations:
Vormetric shines with its Transparent Encryption, which offers encryption, access controls, and data access audit logging without re-engineering applications, databases, or infrastructure. Their Application Encryption allows developers to build encryption into applications effortlessly. The platform also incorporates a Data Masking feature that desensitizes data, thus reducing the risk of exposure.
Integration-wise, Vormetric is adaptable. It aligns with most of the popular infrastructure services, cloud providers, and big data platforms. This ensures that businesses can implement robust encryption without overhauling their existing setups.
Pricing:
Pricing upon request
Pros:
- Transparent Encryption ensures easy integration without disruption
- Dedicated focus on data-at-rest protection
- Easy adaptability with existing infrastructures and cloud setups
Cons:
- Pricing not transparent
- Might be complex for organizations with minimal technical expertise
- Potential for latency in data access due to extensive encryption processes
4. Virtru - Best for data protection with privacy engineering
Virtru offers an innovative approach to data protection by harnessing the power of privacy engineering. As organizations navigate the complexities of securing sensitive information, Virtru emerges as a beacon, addressing both encryption needs and the principles of privacy engineering.
Why I Picked Virtru:
In my journey of selecting encryption and privacy tools, Virtru distinctly captured my attention due to its blend of encryption and privacy engineering. I determined that its distinctive marriage of data protection with an engineering approach toward privacy sets it apart in the saturated market.
Given the escalating significance of both privacy and data protection, Virtru's dedication to intertwining the two makes it the best for businesses seeking a comprehensive privacy-centric data protection solution.
Standout Features & Integrations:
Virtru's patented Trusted Data Format (TDF) ensures that data remains encrypted at all points in its lifecycle. Additionally, its Data Protection Platform provides granular access controls and revocation capabilities, giving users direct oversight of their data's accessibility. Their Secure User-First Policy ensures the protection of user data while facilitating easy sharing.
As for integrations, Virtru is known to work hand in hand with popular platforms such as Google Workspace and Microsoft 365. These integrations ensure that businesses can leverage Virtru's capabilities without having to depart from their primary operational platforms.
Pricing:
Pricing upon request
Pros:
- Integration of encryption with privacy engineering principles
- Comprehensive integrations with mainstream platforms like Google Workspace and Microsoft 365
- Granular control over data accessibility
Cons:
- Pricing isn't transparently listed
- Some learning curves for non-technical users
- Dependency on third-party platforms for full functionality
5. Box KeySafe - Best for granular encryption controls in cloud storage
Box KeySafe provides businesses with robust encryption controls tailored to their cloud storage needs. By putting the power of encryption key management in the hands of users, it ensures that data stored in the cloud remains in the control of its rightful owner. This strong emphasis on granular control makes it exceptionally apt for organizations keen on refining their encryption processes in the cloud.
Why I Picked Box KeySafe:
When I embarked on comparing various encryption solutions, Box KeySafe caught my eye due to its unique approach to cloud storage encryption. The tool's ability to grant businesses autonomy over their encryption keys was the determining factor in my selection.
Based on its ability to offer nuanced control over encryption in the cloud environment, I am confident that Box KeySafe stands as the best for businesses wanting precision control over their encrypted cloud data.
Standout Features & Integrations:
One of Box KeySafe's most striking features is its dedicated hardware security module (HSM) which ensures an organization's encryption keys are protected at all times. Additionally, its comprehensive audit logs provide organizations with clear insights into their encryption key usage, bolstering transparency.
In terms of integrations, Box KeySafe fits into the larger Box ecosystem, enabling businesses to benefit from a broad range of Box services. This compatibility ensures businesses can access encrypted files on the go and collaborate securely with their teams.
Pricing:
Pricing upon request
Pros:
- User-managed encryption keys offer businesses unparalleled control
- Easy integration with the broader Box ecosystem
- Detailed audit logs for transparency on encryption key usage
Cons:
- Not a standalone solution; reliant on the Box ecosystem
- Can be challenging to set up without technical expertise
- Limited compatibility outside of Box's offerings
6. Akeyless Vault Platform - Best for zero-trust encryption key management
Akeyless Vault Platform provides businesses with a comprehensive solution for managing their encryption keys, grounded in the zero-trust security model. By embracing this model, Akeyless ensures that data is encrypted and decrypted without exposing the encryption keys, which directly aligns with the principle of not trusting any entity inside or outside of the system.
Why I Picked Akeyless Vault Platform:
In my journey of selecting encryption key management platforms, Akeyless Vault Platform consistently stood out. The primary reason I chose this tool is its unwavering commitment to the zero-trust model, a security approach that resonates with the current cybersecurity landscape.
Given its emphasis on not exposing encryption keys even during the encryption or decryption processes, I believe it's undoubtedly the best for those prioritizing zero-trust encryption key management.
Standout Features & Integrations:
A defining feature of Akeyless Vault Platform is its Distributed Fragments Cryptography, ensuring that keys remain split and never exist as a whole. Additionally, it offers an automated rotation of secrets and keys, minimizing the risk of key exposure over time.
For integrations, Akeyless Vault Platform is compatible with a variety of DevOps tools and cloud platforms. This means businesses can streamline their workflows, whether they're working with AWS, Azure, Google Cloud, or Kubernetes, to name a few.
Pricing:
Pricing upon request
Pros:
- Adherence to the zero-trust security model for robust protection
- Distributed Fragments Cryptography ensures encryption keys never exist in their entirety
- Broad compatibility with major cloud platforms and DevOps tools
Cons:
- Might present a learning curve for businesses new to zero-trust concepts
- Integration might require technical expertise for the setup
- The platform’s features might be overwhelming for smaller organizations or teams
7. Azure Key Vault - Best for Azure cloud integration and security
Azure Key Vault is Microsoft's dedicated solution for securely managing cryptographic keys, secrets, and certificates used by cloud applications and services. Given its integration capabilities with other Azure services, it offers an intuitive environment for businesses already vested in the Azure ecosystem, making it optimal for Azure cloud integration and security.
Why I Picked Azure Key Vault:
I selected Azure Key Vault after comparing multiple key management platforms. It consistently emerged as a tool that offers a unique blend of integration, convenience, and security for those who are committed to the Azure platform.
The decision was clear; for businesses deeply invested in Azure, this tool stands out as the best for ensuring both integration and paramount security within the Azure cloud.
Standout Features & Integrations:
Azure Key Vault shines with features like hardware security modules (HSMs) that meet FIPS 140-2 Level 2 standards, ensuring the highest level of security for cryptographic keys. Furthermore, the platform provides centralized management for application secrets which can reduce the potential points of exposure.
When it comes to integrations, Azure Key Vault's true strength lies in its cohesiveness with other Azure services. Whether it's Azure Active Directory for identity services, Azure DevOps for continuous delivery, or Azure Policy for cloud governance, businesses have a plethora of options to ensure streamlined workflows.
Pricing:
Pricing upon request
Pros:
- Deep integration with Azure services ensures a cohesive cloud experience
- Hardware security modules offer top-tier cryptographic protection
- Centralized management reduces potential security vulnerabilities
Cons:
- Might not be the best choice for businesses not using the Azure ecosystem
- Configuration and deployment might require Azure-specific knowledge
- Potential for additional costs when leveraging certain features or integrations
8. Cloud Key Management - Best for Google Cloud users seeking native key services
Cloud Key Management is Google Cloud's premier tool for the handling and management of cryptographic keys within its ecosystem. For businesses already leveraging Google Cloud's suite of services, this solution provides an in-house key management option that's tuned for maximum compatibility and ease of integration.
Why I Picked Cloud Key Management:
Upon examining various key management tools, I found that Cloud Key Management offered distinct advantages for those deeply embedded in the Google Cloud environment. Its native compatibility with Google Cloud services combined with robust security features placed it a notch above the rest for this particular audience.
For Google Cloud users, this tool is evidently the best for receiving dedicated, native key services without the friction of third-party integrations.
Standout Features & Integrations:
Cloud Key Management boasts of a hierarchical key management system, allowing businesses to define and manage keys at both project and organizational levels. Additionally, it uses Hardware Security Modules (HSMs) under the hood, ensuring compliance with high-security standards for cryptographic operations.
Integration-wise, it excels when combined with other Google Cloud services. From Google Cloud Storage, and Compute Engine to BigQuery, users can effortlessly integrate cryptographic operations, benefiting from the tool's compatibility with the Google Cloud ecosystem.
Pricing:
Pricing upon request
Pros:
- Native to Google Cloud, offering optimal compatibility
- Hierarchical management provides structured control over keys
- Built on top of secure HSMs for improved cryptographic operations
Cons:
- Tailored specifically for Google Cloud, making it less flexible for multi-cloud strategies
- Some features might present a learning curve for new users
- Costs can accumulate when paired with other Google Cloud services
9. Verimatrix Key Shield - Best for multifaceted cybersecurity solutions
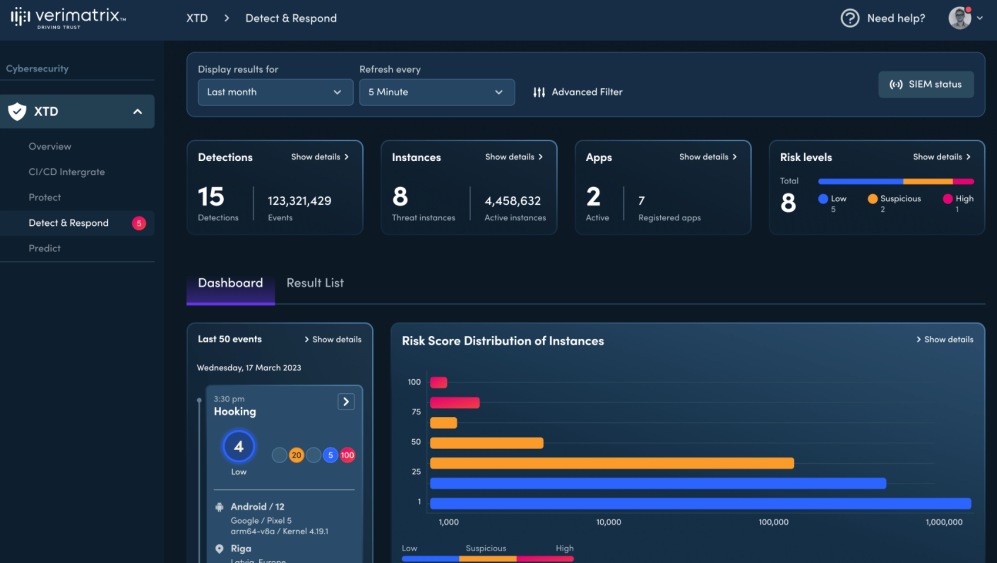
Verimatrix Key Shield is a comprehensive key management platform that goes beyond traditional offerings, ensuring businesses have the tools they need to safeguard sensitive data. Given the increasing cyber threats businesses face today, this platform provides a multifaceted approach to cybersecurity, aligning with the needs of modern enterprises.
Why I Picked Verimatrix Key Shield:
In determining which tool to highlight, Verimatrix Key Shield caught my attention due to its broad approach to cybersecurity. It doesn't just stop at key management; its features encompass a wider range of security solutions, making it different from more narrow-focused tools.
For businesses looking for an all-in-one security solution without compromising on individual features, Verimatrix Key Shield stands out as the best choice.
Standout Features & Integrations:
One of Verimatrix Key Shield's primary features is its adaptive security framework, which continuously evolves based on the threats detected, providing businesses with dynamic protection. Additionally, its deep analytics feature offers insights into potential vulnerabilities, empowering businesses to take proactive measures.
Verimatrix Key Shield has been designed to integrate smoothly with a range of business tools and platforms. Key integrations include various cloud providers, databases, and other enterprise software solutions, ensuring that businesses can maintain a consistent security posture across their operations.
Pricing:
Pricing upon request
Pros:
- Comprehensive cybersecurity solutions beyond just key management
- Adaptive security framework adjusts to evolving threats
- Rich analytics for insights into potential vulnerabilities
Cons:
- Might be overkill for small businesses with specific needs
- Integration with some niche tools might require additional configuration
- As with all-inclusive solutions, there's potential for unused features
10. ManageEngine Key Manager Plus - Best for IT teams managing SSH and SSL keys
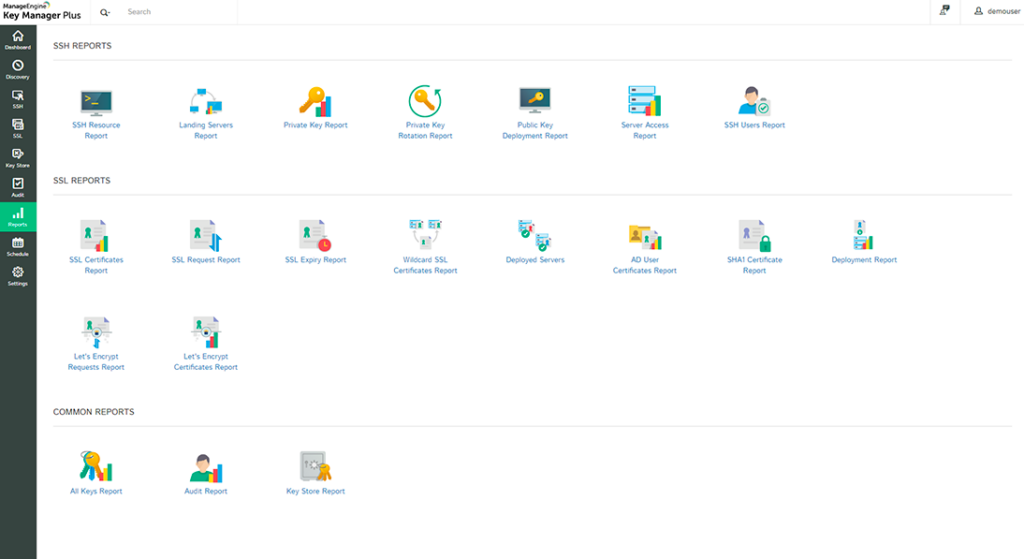
ManageEngine Key Manager Plus offers specialized tools that streamline the complex task of managing SSH and SSL keys. Recognizing the pivotal role these keys play in IT security, this platform provides an integrated solution to ensure IT teams can easily oversee and maintain their encryption keys.
Why I Picked ManageEngine Key Manager Plus:
When selecting a tool for key management, I looked for software that addressed specific challenges IT teams often encounter. ManageEngine Key Manager Plus was my choice due to its focus on SSH and SSL keys. Given the intricacies involved in handling these types of keys, I found this tool to be a robust solution for IT teams.
Its ability to hone in on these specific key types distinguishes it from broader key management tools.
Standout Features & Integrations:
ManageEngine Key Manager Plus excels with its automated key rotation feature, reducing manual labor and enhancing security. The platform also offers detailed audit trails, ensuring teams can track key usage and modifications for compliance purposes.
Integration-wise, ManageEngine Key Manager Plus is designed to work with a variety of IT infrastructure tools and platforms. Notable integrations include support for leading SSH clients, web servers, and network devices, facilitating a more unified IT security approach.
Pricing:
Pricing upon request
Pros:
- Tailored specifically for managing SSH and SSL keys
- Automated key rotation boosts efficiency and security
- Comprehensive audit trails aid in compliance
Cons:
- Might be overly specialized for organizations needing broader key management solutions
- User interface might have a learning curve for new users
- Some advanced features could be unnecessary for smaller teams
11. AWS Key Management Service - Best for AWS ecosystem key management
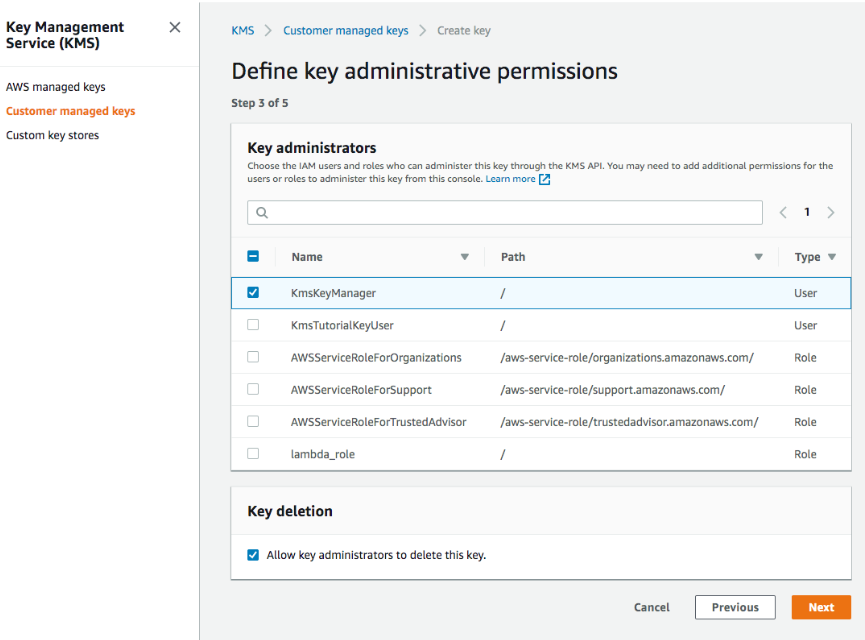
AWS Key Management Service (KMS) is a managed service that allows users to easily create and manage cryptographic keys used for data protection. Being a part of the vast AWS ecosystem, this service ensures effective and efficient key management specifically tailored for AWS-based applications and services.
Why I Picked AWS Key Management Service:
In determining the right tools for this list, I gave importance to native integration capabilities. AWS Key Management Service was an evident choice for me because of its integration and optimization within the AWS environment. I believe it's best for those deeply invested in the AWS ecosystem because having a key management system from the same provider can simplify many operational aspects, from billing to technical support.
Standout Features & Integrations:
AWS KMS offers centralized management of cryptographic keys, with permissions that can be finely tuned using AWS Identity and Access Management (IAM). Additionally, it supports both symmetric and asymmetric keys, providing flexibility based on the use case.
Being an AWS service, KMS integrates effortlessly with most AWS services like Amazon S3, Amazon RDS, AWS Lambda, and many others. This means data stored or processed in these services can be encrypted with keys managed in KMS, streamlining security across multiple AWS services.
Pricing:
Pricing upon request
Pros:
- Native AWS integration simplifies usage for AWS-based applications.
- Support for both symmetric and asymmetric keys provides versatility.
- Fine-grained access control using AWS IAM.
Cons:
- Might not be the best option for non-AWS environments.
- The pricing model can be complex based on key usage and API calls.
- Initial setup might require a thorough understanding of AWS services and IAM policies
12. Oracle Cloud Infrastructure Vault - Best for Oracle-centric enterprise security
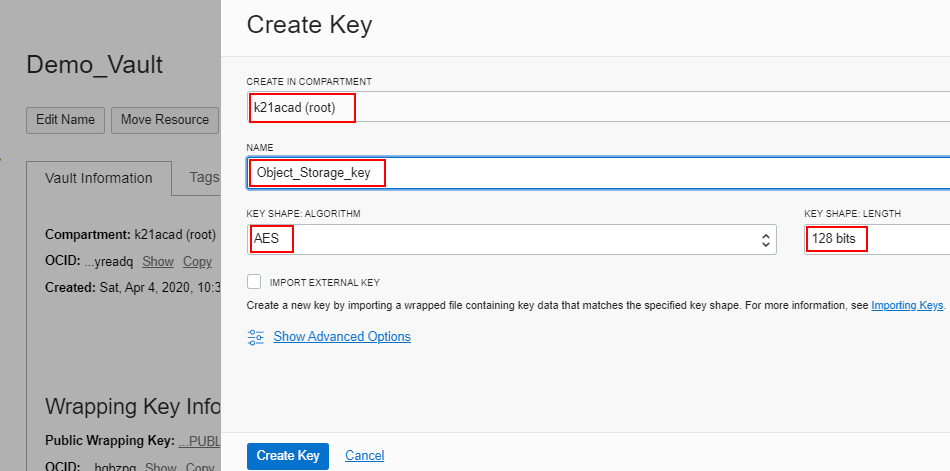
Oracle Cloud Infrastructure Vault provides centralized key management, facilitating the protection and control of sensitive data across Oracle Cloud applications. Designed with Oracle platforms in mind, this tool offers a comprehensive security solution for enterprises heavily invested in Oracle services.
Why I Picked Oracle Cloud Infrastructure Vault:
When selecting key management tools for this compilation, I sought tools that provided specialized advantages for particular ecosystems. Oracle Cloud Infrastructure Vault caught my attention due to its dedicated optimization for Oracle platforms.
I determined it's best suited for organizations rooted in the Oracle landscape because aligning their key management with their main tech stack simplifies processes and enhances compatibility.
Standout Features & Integrations:
Oracle Cloud Infrastructure Vault offers Hardware Security Module (HSM) backed keys, ensuring top-tier security for cryptographic operations. Furthermore, it provides automated rotation policies, allowing organizations to enforce timely key rotations without manual intervention.
Integration-wise, this tool is finely tuned to work with a variety of Oracle Cloud services, including Oracle Cloud Infrastructure Databases, Object Storage, and Oracle Kubernetes Engine. This ensures a unified security posture across various Oracle Cloud components.
Pricing:
Pricing upon request
Pros:
- Specialized for Oracle platforms, ensuring tighter integration and fewer compatibility issues.
- Hardware Security Module-backed keys offer robust cryptographic security.
- Automated rotation policies promote consistent security hygiene.
Cons:
- Might not be the primary choice for non-Oracle environments.
- Potential learning curve for those unfamiliar with Oracle's cloud interface.
- Custom integrations outside of Oracle's ecosystem might need extra configuration
Other Noteworthy Encryption Key Management Software
Below is a list of additional encryption key management software that I shortlisted but did not make it to the top 12. They are definitely worth checking out.
- AWS CloudHSM - Good for AWS-native hardware security modules
- HashiCorp Vault - Good for flexible secret management across platforms
- Doppler SecretOps Platform - Good for centralized environment secrets management
- TokenEx - Good for cloud tokenization and data security
- Keyfactor Signum - Good for scalable certificate management
- GnuPG - Good for free, open-source encryption
- Futurex Excrypt Key Management - Good for enterprise-grade key lifecycle management
- NetLib Security Encryptionizer Key Manager - Good for easy database encryption
- Entrust KeyControl - Good for cohesive encryption key control
- IBM Guardium Key Lifecycle Manager - Good for robust encryption key lifecycle governance
- FAMIS 360 - Good for facilities and space management
- Fortanix Data Security Manager - Good for comprehensive data protection
- Promaster Key Manager - Good for locksmith business management
Selection Criteria for Choosing the Best Encryption Key Management Software
When it comes to selecting the right key management software, not all tools are created equal. Having worked in the tech industry for several years, I have seen and tested a plethora of key management tools. I've evaluated dozens of key management tools, but in this case, I was really looking for robust security features coupled with user-friendly interfaces.
After trying out more than 20 tools, these were my favorites, and here's a breakdown of the criteria I used:
Core Functionality
- Encryption Standards: The tool should support multiple encryption standards, ensuring adaptability and future-proofing.
- Key Rotation: Automated capabilities to change keys at specified intervals or under certain conditions.
- Key Storage: Safe and secured storage options for both active and backup encryption keys.
- Key Retrieval: Fast and secure methods to retrieve encryption keys when needed.
- Audit Trails: The ability to track who accessed what key and when ensuring traceability.
Key Features
- Multi-Tenancy: Allows distinct users or user groups to hold their keys, isolated from one another, enhancing security.
- Hardware Security Module (HSM) Integration: Ensures physical security by integrating with external HSMs, providing an added layer of protection.
- Endpoint Security: Protects the endpoints, making sure keys remain safe even in distributed environments.
- Lifecycle Management: Manages the entire life cycle of a key, from creation to retirement.
- Access Controls: Implements robust role-based or attribute-based access controls to manage who can access which key.
Usability
- Intuitive Dashboard: A clean dashboard that visualizes key metrics, threats, and operational statuses at a glance.
- Search and Filtering: Offers users the ability to easily search for a specific key or filter based on attributes, time frames, or other relevant criteria.
- Easy Onboarding: Tools should come with step-by-step setup guides, wizards, or templates to ease the initial setup process.
- Contextual Help: Inline help, tooltips, or a knowledge base that guides users through processes without them having to leave the application.
- Responsive Support: Fast-responding customer support that understands the intricacies and urgency associated with key management issues.
- Training Programs: Comprehensive tutorials, webinars, or courses that equip users to harness the full power of the tool.
Most Common Questions Regarding Encryption Key Management Software
What are the benefits of using encryption key management software?
There are numerous advantages to employing encryption key management software, including:
- Improved Security: These tools provide robust encryption methodologies ensuring that sensitive data remains protected.
- Auditability: They offer audit trails, which log every access to the encryption keys, ensuring transparency and traceability.
- Centralized Control: They centralize the management of keys, allowing for a more streamlined operation and consistent application of security policies.
- Scalability: As organizations grow, the software can handle an increased number of keys without compromising performance or security.
- Compliance: Many of these tools assist in adhering to various regulatory standards and mandates related to data protection.
How much does encryption key management software typically cost?
The pricing of encryption key management software varies widely based on its feature set, scalability, and target market. Most tools employ one of the following pricing models:
- Per User/Seat: Charging is based on the number of users or seats.
- Feature-based: Pricing tiers depend on the features provided at each level.
- Volume-based: Charges are levied based on the number of keys or the amount of data being managed.
- Subscription: A recurring fee, usually monthly or annually.
The typical range for such software can be anywhere from $5/user/month to over $500/month for enterprise-level solutions.
Which are the cheapest and most expensive encryption key management software?
While exact prices can change based on current market trends, as of my last research, GnuPG is among the more affordable options as it's an open-source tool. On the higher end of the spectrum, enterprise-grade solutions like IBM Guardium Key Lifecycle Manager or Oracle Cloud Infrastructure Vault often come with a heftier price tag due to their comprehensive feature set and scalability.
Are there any free encryption key management tools available?
Yes, there are free options available. GnuPG, for instance, is a free encryption and signing tool. While it may not have the extensive feature set of paid solutions, it's a reliable choice for smaller organizations or individual users. However, it's crucial to understand the limitations and ensure that any free tool aligns with your security requirements.
Other Data Protection Software Reviews
- Encryption Software
- Password Manager Software
- Network Access Control Software
- Cybersecurity Software
Summary
Choosing the best encryption key management software can be a daunting task, given the myriad of options available. The article delved into the intricacies of such tools, highlighting their crucial role in data protection, streamlining operations, and ensuring compliance. Making the right choice involves understanding core functionalities, discerning essential features, and assessing usability tailored to your specific needs.
Key Takeaways
- Prioritize security & compliance: The primary function of any encryption key management tool is to enhance data protection. Ensure your choice aligns with regulatory standards relevant to your industry or region.
- Usability matters: A tool's interface, ease of onboarding, and customer support can significantly influence its utility. Consider solutions that offer a balance between functionality and user-friendly interfaces.
- Consider pricing & scalability: While budget is essential, investing in a scalable solution that grows with your organization's needs is crucial for long-term value.
What Do You Think?
While I've tried to be comprehensive in my review, the tech landscape is vast and ever-evolving. If you believe I've overlooked an encryption key management software that deserves mention, please reach out. I value your insights and I am always eager to learn about new and emerging tools in the field. Your suggestions help ensure that my guide remains updated and relevant for all.
