12 Best Dark Web Monitoring Tools Shortlist
I've scoured the depths of the dark web so you don't have to. After evaluating dozens of tools, I've curated the 12 best dark web monitoring solutions tailored to solve your biggest cybersecurity challenges.
- LogMeOnce - Best for identity theft protection and multi-device support
- CYRISMA - Best for integrating with existing security stacks
- SpyCloud - Best for enterprise-level credential exposure detection
- ID Agent - Best for MSPs and resellers focusing on small businesses
- Cyberint - Best for real-time threat intelligence capabilities
- ImmuniWeb - Best for compliance-driven organizations needing GDPR and HIPAA audits
- ZeroFox - Best for brand protection and digital footprint tracking
- DarkIQ - Best for offering flexible alert configurations
- Webz.io - Best for its data visualization and dark web analysis
- Progress WhatsUp Gold - Best for network administrators seeking extended dark web monitoring
- Flare - Best for scalability, ideal for startups to Fortune 500 companies
- LastPass - Best for individual users requiring password management and dark web scans
Navigating the vast expanse of the internet is like maneuvering through an iceberg: what you see on the surface web through common search engines is just the tip. Below the surface lies the deep web and the darknet, where cybercriminals and hackers engage in illegal activities. These threat actors exploit the anonymity of these realms to trade personally identifiable information (PII), and sensitive data and launch various forms of cyberattacks like malware, ransomware, and scams.
What Are Dark Web Monitoring Tools?
Dark web monitoring tools are specialized software solutions designed to scan, identify, and alert users to threats lurking in the hidden recesses of the dark web. These tools are commonly used by individuals, corporations, and government agencies to proactively safeguard sensitive information such as personal credentials, intellectual property, and proprietary data. By continuously monitoring various dark web forums, marketplaces, and private networks, these tools help preempt cyber threats like identity theft, data breaches, and other forms of unauthorized access or exploitation.
The importance of dark web monitoring services is security tools that use machine learning and automation to proactively scan dark websites for any malicious activities related to your personal or business data. Security teams are always a step ahead of criminal activity and equipped to tackle issues before they escalate. Also finding your login credentials or IP addresses in dark corners where they shouldn't be, and allowing for rapid response before law enforcement gets involved.
Overviews of the 12 Best Dark Web Monitoring Tools
1. LogMeOnce - Best for identity theft protection and multi-device support

LogMeOnce is a cybersecurity tool designed to safeguard your digital identity by focusing on identity theft protection. It also offers robust multi-device support, which makes it versatile for users who frequently switch between different platforms.
Why I Picked LogMeOnce:
I selected LogMeOnce for this list due to its dual focus on identity theft protection and multi-device support. These two capabilities make it distinct in the crowded cybersecurity marketplace. It excels at protecting your digital identity across a variety of platforms, which is why it's best for identity theft protection and multi-device support.
Standout Features & Integrations:
One of the most crucial features of LogMeOnce is its Passwordless PhotoLogin, which allows you to gain access to your account without requiring a master password. Another compelling feature is the Anti-Theft system, which offers a range of functionalities from remote lock to data wipe.
For integrations, LogMeOnce provides out-of-the-box compatibility with Active Directory, LDAP, and a variety of SSO solutions, making it easier for enterprises to adopt it into their existing infrastructure.
Pricing:
Starting from $2.50/user/month (billed annually), LogMeOnce offers a competitively priced package for the features it delivers.
Pros:
- Robust identity theft protection features
- Extensive multi-device support
- Out-of-the-box integrations with enterprise solutions
Cons:
- Requires annual commitment for the most cost-effective plan
- Can be overwhelming for users unfamiliar with cybersecurity tools
- Limited customer support outside business hours
2. CYRISMA - Best for integrating with existing security stacks
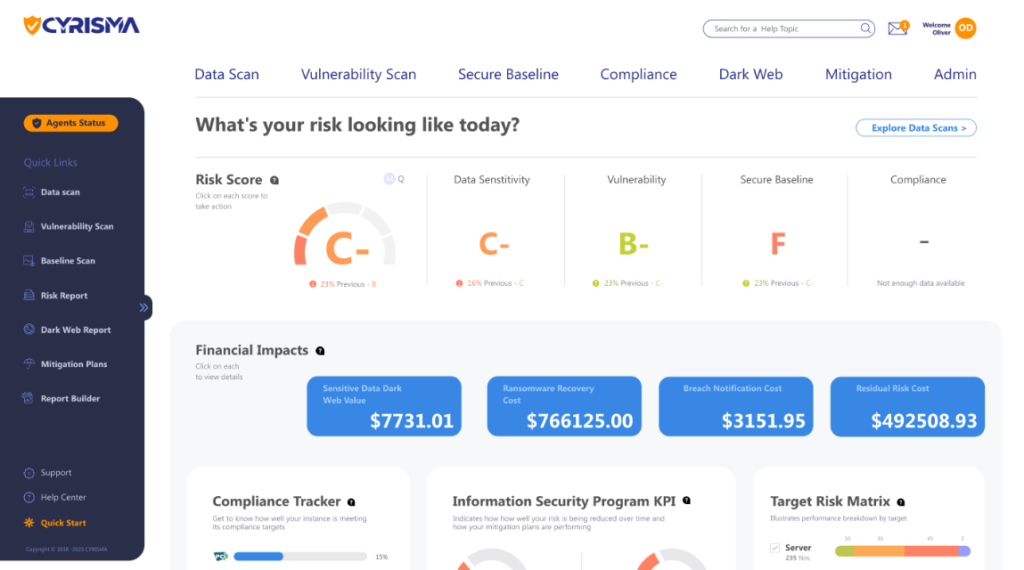
CYRISMA is a cybersecurity platform designed to safeguard digital assets by integrating with your existing security stacks. It aims to extend your cybersecurity capabilities by working in synergy with the tools you already have.
Why I Picked CYRISMA:
I chose CYRISMA because of its focus on blending with existing security stacks, making it an ideal extension rather than a replacement. This unique approach sets it apart and makes it ideal for organizations that already have some level of cybersecurity infrastructure. It is best for those who are looking to integrate new capabilities with their existing security stacks.
Standout Features & Integrations:
CYRISMA offers features like asset classification, vulnerability management, and compliance tracking. It also offers threat intelligence that can be tailored to specific industry needs.
For integrations, it works well with SIEM solutions, firewalls, and other intrusion detection systems, underlining its suitability for integration with existing security stacks.
Pricing:
From $20/user/month, with a minimum requirement of 5 seats.
Pros:
- Works well with existing security stacks
- Offers tailored threat intelligence
- Comprehensive feature set including compliance tracking
Cons:
- Minimum requirement of 5 seats may not suit smaller operations
- Can be complex to set up
- Not suited for those looking for a standalone solution
3. SpyCloud - Best for enterprise-level credential exposure detection
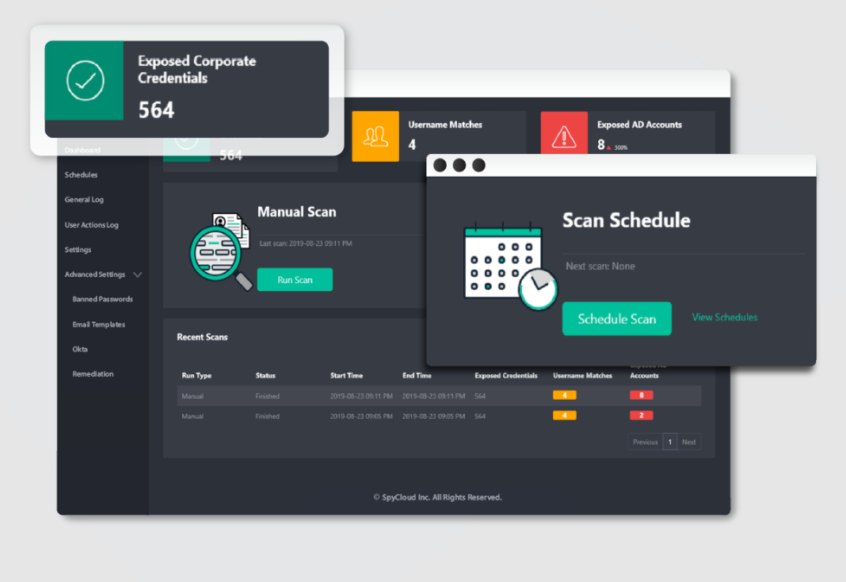
SpyCloud specializes in enterprise-level credential exposure detection to protect against account takeover and fraud. Its services are geared towards large enterprises that are at high risk of credential attacks.
Why I Picked SpyCloud:
I picked SpyCloud because of its robust capabilities in credential exposure detection specifically designed for enterprise-level operations. The tool excels at identifying exposed credentials in real time, making it best for enterprise-level credential exposure detection.
Standout Features & Integrations:
SpyCloud offers automated remediation and real-time alerts among its standout features. Its data feeds can be integrated with SIEM systems, making it an excellent addition to enterprise-level cybersecurity efforts.
Pricing:
Pricing upon request.
Pros:
- Specializes in enterprise-level credential exposure detection
- Automated remediation and real-time alerts
- Easily integrates with SIEM systems
Cons:
- Pricing information not readily available
- Geared towards large enterprises, not suitable for smaller operations
- Could be overkill for organizations with basic security needs
4. ID Agent - Best for MSPs and resellers focusing on small businesses
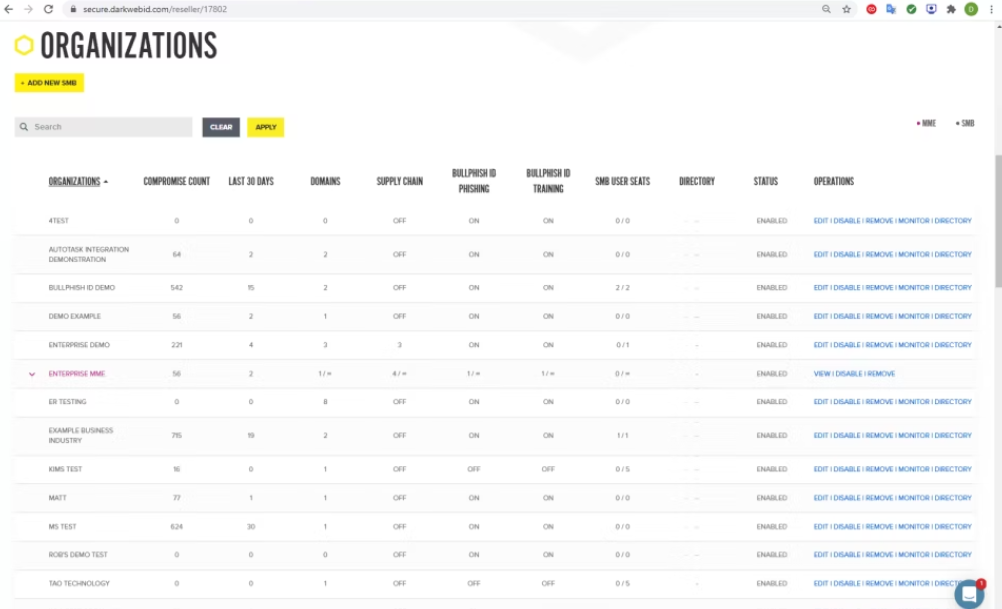
ID Agent offers cybersecurity solutions tailored for Managed Service Providers (MSPs) and resellers who focus on small businesses. The platform provides a variety of tools to monitor and manage cybersecurity threats for clients.
Why I Picked ID Agent:
I chose ID Agent because it provides a comprehensive suite of cybersecurity tools specifically designed for MSPs and resellers. This specialization makes it stand out from general-purpose cybersecurity platforms. It’s best for MSPs and resellers who are primarily focusing on small businesses, given its tailored features and scalable solutions.
Standout Features & Integrations:
ID Agent offers features like dark web monitoring, phishing simulations, and security awareness training. Its toolset is designed to help MSPs provide comprehensive security services to their clients.
For integrations, ID Agent can integrate with popular PSA and RMM platforms, enabling MSPs to offer layered security services.
Pricing:
From $25/user/month (min 5 seats).
Pros:
- Tailored for MSPs and resellers
- Comprehensive feature set including dark web monitoring
- Integrates well with PSA and RMM platforms
Cons:
- The minimum 5-seat requirement might be a constraint for smaller MSPs
- Pricing can be on the higher side for small businesses
- Not suitable for general-purpose or enterprise-level cybersecurity needs
5. Cyberint - Best for real-time threat intelligence capabilities
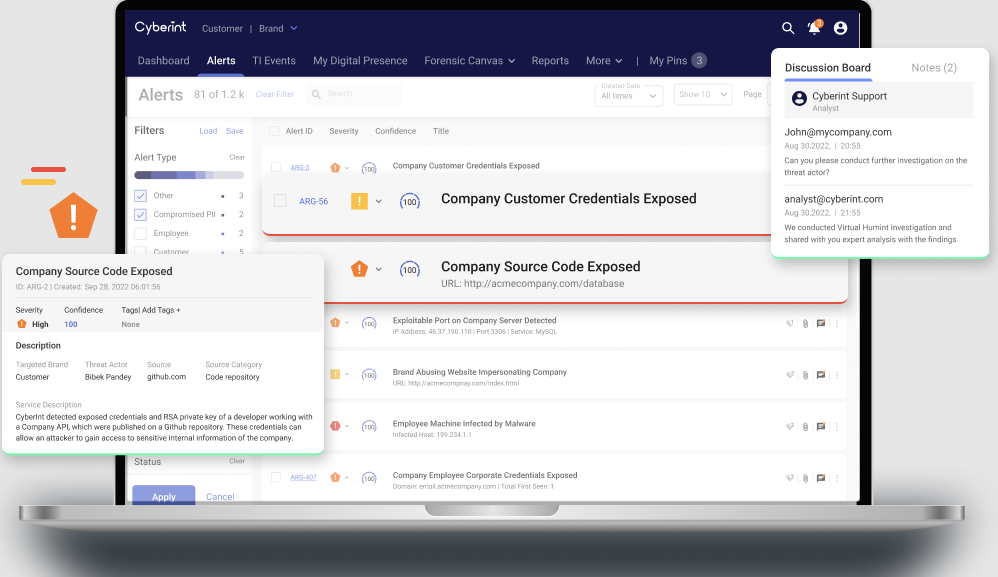
Cyberint specializes in providing real-time threat intelligence capabilities to safeguard against cyber threats. The platform provides comprehensive insights and analytics to identify and tackle cybersecurity threats as they occur.
Why I Picked Cyberint:
I selected Cyberint for its exceptional focus on real-time threat intelligence capabilities. The platform excels in providing timely and actionable insights, making it stand out for businesses that require up-to-the-minute threat data. It's best for organizations looking for real-time threat intelligence capabilities.
Standout Features & Integrations:
Cyberint offers real-time threat intelligence feeds, incident response capabilities, and digital risk protection. These features make it highly effective for proactively tackling cyber threats.
For integrations, Cyberint works well with various SIEM solutions and threat intelligence platforms, enhancing its value as a real-time threat intelligence solution.
Pricing:
Pricing upon request.
Pros:
- Focuses on real-time threat intelligence
- Offers incident response capabilities
- Integrations with SIEM solutions
Cons:
- Pricing information is not transparent
- May be too specialized for small businesses
- Requires a team with expertise in threat intelligence to fully leverage its capabilities
6. ImmuniWeb - Best for compliance-driven organizations needing GDPR and HIPAA audits
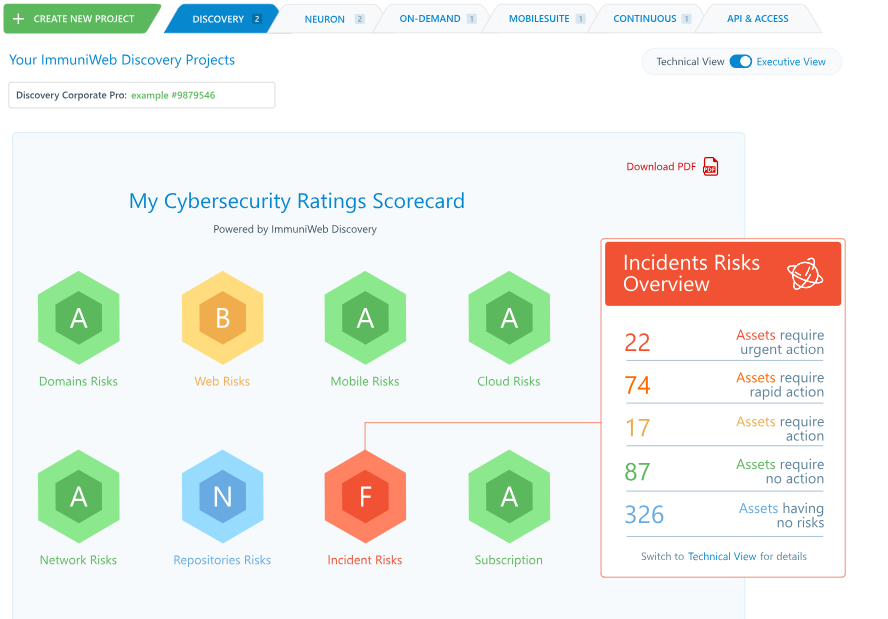
ImmuniWeb is a cybersecurity platform that specializes in compliance audits, particularly GDPR and HIPAA. It’s designed to help organizations navigate complex compliance requirements effectively.
Why I Picked ImmuniWeb:
I picked ImmuniWeb for its strong focus on compliance audits, including GDPR and HIPAA. This focus makes it particularly suitable for organizations that are driven by compliance needs. It is best for those needing specialized audits for GDPR and HIPAA compliance.
Standout Features & Integrations:
ImmuniWeb offers features like web application scanning, mobile application scanning, and compliance assessments, making it a comprehensive tool for any compliance-driven organization.
For integrations, ImmuniWeb can work with existing GRC (governance, risk management, and compliance) platforms and SIEM solutions.
Pricing:
From $50/user/month (billed annually).
Pros:
- Specializes in compliance audits for GDPR and HIPAA
- Offers comprehensive scanning features for web and mobile applications
- Integrates well with existing GRC platforms
Cons:
- Annual billing could be a commitment issue for some organizations
- May not be suitable for organizations without specialized compliance needs
- Could be expensive for smaller businesses
7. ZeroFox - Best for brand protection and digital footprint tracking
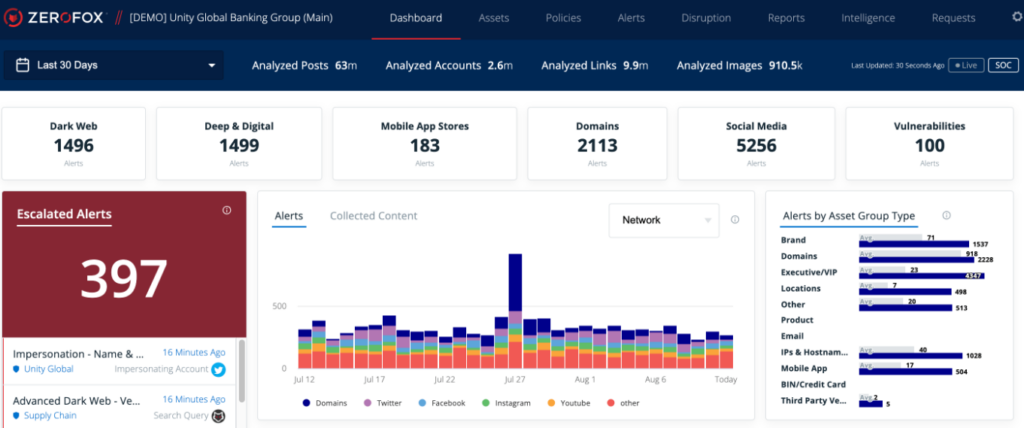
ZeroFox specializes in digital risk protection, focusing on brand protection and tracking digital footprints across various online platforms. Its capabilities make it especially useful for businesses that are concerned about brand reputation and exposure online.
Why I Picked ZeroFox:
I chose ZeroFox because it offers unique features aimed specifically at brand protection and tracking digital footprints. This specialization gives it an edge in addressing issues that companies concerned about brand safety face. I believe it's best for brand protection and digital footprint tracking due to its robust set of features in these areas.
Standout Features & Integrations:
ZeroFox provides features like real-time alerts for brand impersonation, data leak tracking, and customer engagement protection.
For integrations, ZeroFox supports various social media platforms and CRM solutions, allowing businesses to centralize their brand protection initiatives.
Pricing:
From $29/user/month (min 10 seats).
Pros:
- Specializes in brand protection
- Offers robust digital footprint tracking
- Wide range of integrations including social media platforms
Cons:
- The minimum 10-seat requirement could be limiting for small businesses
- Pricing may be steep for some organizations
- May not offer broader cybersecurity features found in comprehensive platforms
8. DarkIQ - Best for offering flexible alert configurations
DarkIQ is designed to provide cybersecurity intelligence with an emphasis on flexible alert configurations. This makes it suitable for organizations that require granular control over threat alerts.
Why I Picked DarkIQ:
I selected DarkIQ for its exceptional focus on flexible alert configurations. This tool stands out for its customization options, which are crucial for organizations requiring specific alert settings. I hold the opinion that it's best to offer flexible alert configurations because of this feature set.
Standout Features & Integrations:
DarkIQ offers features like real-time threat alerts, customizable dashboards, and the ability to filter alerts based on severity or type.
For integrations, DarkIQ can integrate with popular SIEM and SOAR solutions, making it compatible with existing cybersecurity stacks.
Pricing:
Pricing upon request.
Pros:
- The high degree of flexibility in alert configurations
- Can integrate with SIEM and SOAR solutions
- Customizable dashboards for better visibility
Cons:
- Pricing information is not transparent
- May require a learning curve to fully utilize its features
- Limited utility for organizations not requiring complex alert configurations
9. Webz.io - Best for its data visualization and dark web analysis
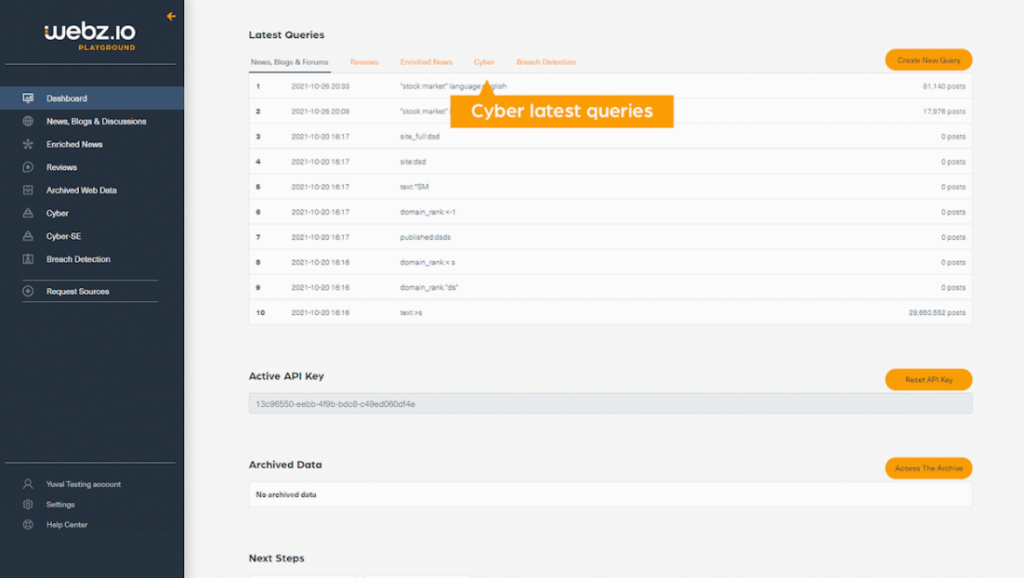
Webz.io offers cybersecurity solutions that focus on data visualization and dark web analysis. This tool is particularly effective for organizations that need insights into the hidden parts of the internet.
Why I Picked Webz.io:
I picked Webz.io because of its strength in data visualization and dark web analysis. In comparing it to other options, I found that its features provide a compelling reason for organizations seeking these specific capabilities. It's best for its data visualization and dark web analysis.
Standout Features & Integrations:
Webz.io offers features like dark web monitoring, data visualizations for easier comprehension of threats, and real-time analytics.
As for integrations, Webz.io can be integrated with various threat intelligence platforms and SIEM solutions to provide a comprehensive cybersecurity landscape.
Pricing:
From $35/user/month (billed annually).
Pros:
- Specializes in data visualization and dark web analysis
- Integrates with various threat intelligence platforms
- Offers real-time analytics for immediate insights
Cons:
- Billed annually, making it a longer-term commitment
- May not be suitable for organizations without a need for dark web analysis
- Pricing could be prohibitive for smaller organizations
10. Progress WhatsUp Gold - Best for network administrators seeking extended dark web monitoring
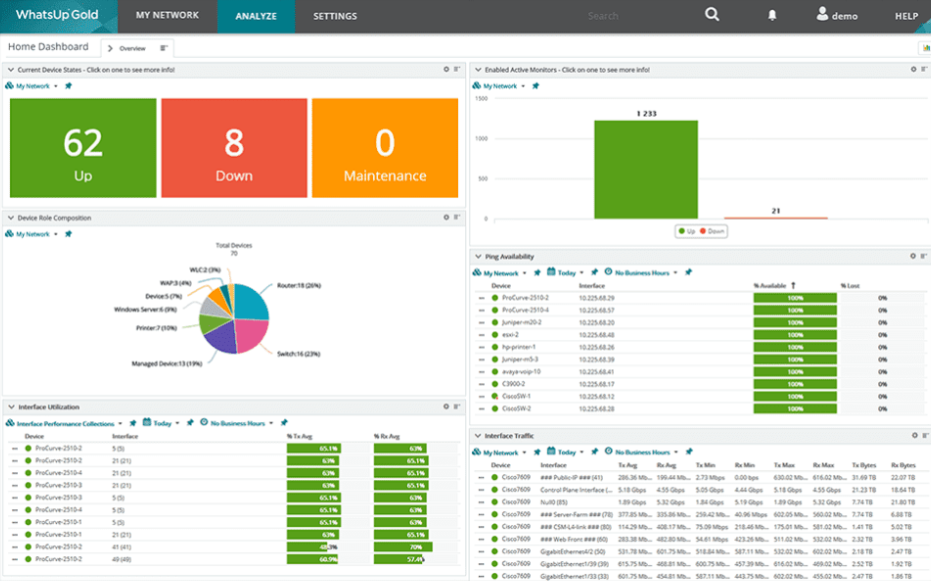
Progress WhatsUp Gold focuses on network monitoring and includes an extended feature set for dark web monitoring. Its suite of tools is particularly beneficial for network administrators who require both traditional network oversight and dark web monitoring.
Why I Picked Progress WhatsUp Gold:
I selected Progress WhatsUp Gold based on its unique blend of network monitoring capabilities and dark web analytics. This tool caught my eye for its ability to give network administrators a two-fold benefit: network performance metrics and dark web insights. Therefore, I think it's best for network administrators who are seeking extended dark web monitoring.
Standout Features & Integrations:
The platform provides features like network discovery, real-time alerts, and dark web monitoring to detect leaked credentials or data.
For integrations, Progress WhatsUp Gold can interface with SNMP, JMX, WMI, and a variety of other standard network protocols.
Pricing:
From $245/user/month (billed annually).
Pros:
- Offers both network monitoring and dark web analysis
- Can integrate with various network protocols
- Real-time alerts for network and dark web incidents
Cons:
- High starting price might deter smaller organizations
- Complexity may result in a steeper learning curve
- Billed annually, requiring a longer-term commitment
11. Flare - Best for scalability, ideal for startups
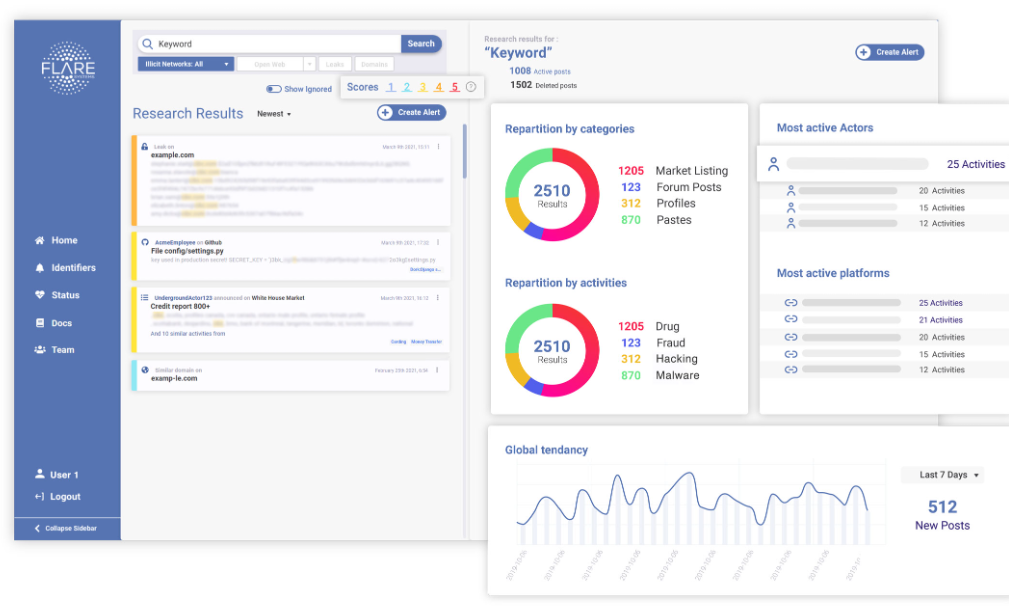
Flare is a cybersecurity platform designed with scalability in mind, making it suitable for businesses of all sizes, from startups to Fortune 500 companies.
Why I Picked Flare:
I chose Flare because of its ability to scale efficiently, accommodating a wide range of company sizes. In my judgment, its adaptability sets it apart, making it a highly versatile tool. I believe it's best for scalability, from startups to large enterprises.
Standout Features & Integrations:
Flare offers features like threat detection, endpoint security, and customizable alerts, all while scaling to the needs of the organization.
For integrations, it can mesh well with existing IT infrastructure, including popular cloud services and endpoint security solutions.
Pricing:
From $30/user/month.
Pros:
- Highly scalable, suitable for varying company sizes
- Customizable alerts based on threat levels
- Integrates easily with existing IT infrastructure
Cons:
- May offer features that smaller companies don't require
- Lack of specialization in any single area
- May require IT expertise for full utilization
12. LastPass - Best for individual users requiring password management and dark web scans
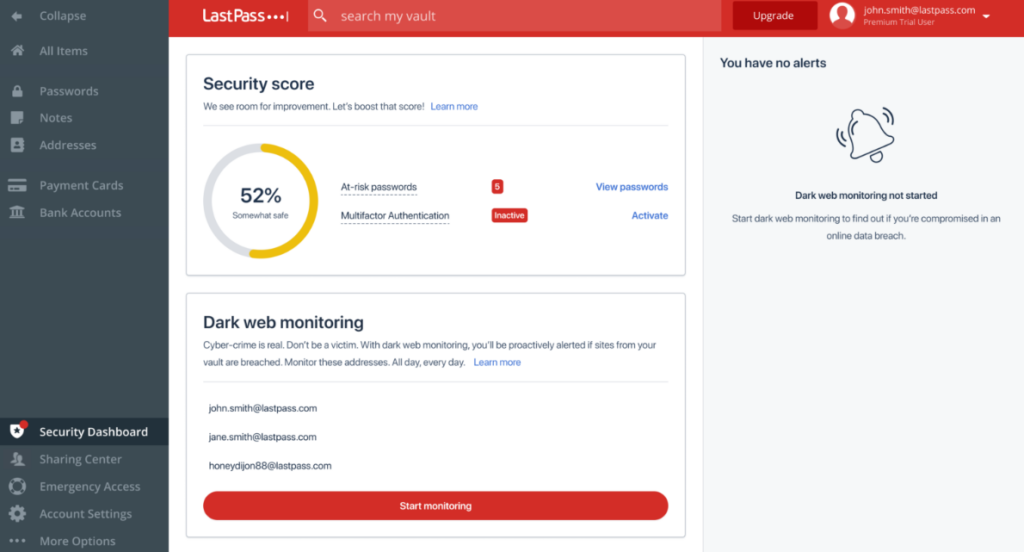
LastPass is a password management tool that offers additional features for dark web scanning, making it a comprehensive option for individual users who need both.
Why I Picked LastPass:
I picked LastPass for its combination of password management and dark web scanning features. When I compared it to similar offerings, I found LastPass provides a broader range of features catering to individual users. I consider it best for individual users requiring password management and dark web scans.
Standout Features & Integrations:
LastPass provides features like secure password storage, password sharing, and dark web scans for leaked credentials.
The tool integrates with browsers for easy password retrieval and can also integrate with other single sign-on solutions.
Pricing:
From $3/user/month (billed annually).
Pros:
- Offers both password management and dark web scans
- Easy-to-use browser integrations
- Affordable pricing
Cons:
- Limited scalability for large organizations
- Billed annually, not monthly
- Some users may find the interface less intuitive than competitors’
Other Notable Dark Web Monitoring Tools
Below is a list of additional dark web monitoring tools that I shortlisted, but did not make it to the top 12. These are definitely worth checking out.
- uBreach - Good for email exposure monitoring
- Flashpoint Intelligence Platform - Good for intelligence-driven security decisions
- InsecureWeb - Good for scanning and assessing website vulnerabilities
- Defendify All-In-One Cybersecurity Solution - Good for small businesses looking for an all-in-one solution
- Ontic - Good for real-time threat detection and management
- PhishLabs - Good for dark web phishing attack monitoring
- Recorded Future - Good for organizations requiring predictive threat analytics
- ZeroFox - Good for brand protection on the dark web
- Constella Intelligence API - Good for identity monitoring through API integrations
- DarkOwl - Good for extensive dark web data monitoring
- Sixgill - Good for automated dark web intelligence collection
Selection Criteria For Choosing Dark Web Monitoring Tools
I've evaluated dozens of dark web monitoring tools, and the ones listed here are those that particularly stood out. While many options on the market offer basic functionality, I was really interested in those that offer comprehensive features tailored for specific use cases. My criteria for selection are discussed in detail below.
Core Functionality
- Dark Web Scanning: The tool should be able to scan the dark web efficiently for any traces of your personal or business information.
- Real-Time Alerts: Timely updates on any suspicious activity are essential for immediate action.
- Threat Intelligence: Gathering data on potential threats is vital, as it allows users to understand the level of risk involved.
- Compliance Checks: For businesses, the tool should offer GDPR, HIPAA, or other regulatory compliance audits and checks.
Key Features
- Multi-Channel Scanning: Beyond just the dark web, the tool should scan forums, marketplaces, and even social media for stolen data or threats.
- User-Friendly Dashboards: For easy threat assessment and management, dashboards that display real-time data are beneficial.
- Custom Alerts: Customization of what constitutes a 'threat' to your organization allows for more accurate monitoring.
- API Integration: The ability to integrate the tool within your existing security infrastructure can be valuable.
- Data Enrichment: Additional information related to the threats detected can help in better understanding the threat landscape.
Usability
- Intuitive Interface: For this type of software, a straightforward and easily navigable interface helps users act quickly on threats.
- Onboarding Process: Given the complexity of dark web threats, a well-guided onboarding process, possibly through tutorial videos or a dedicated customer success agent, can be helpful.
- Customer Support: 24/7 customer support is often necessary for immediate threat mitigation.
- User Role Management: Especially in larger organizations, role-based access to different functionalities ensures that only authorized personnel can take specific actions.
Most Common Questions Regarding Dark Web Monitoring Tools
What are the benefits of using dark web monitoring tools?
- Threat Identification: These tools scan the dark web for any stolen data or threats against your organization.
- Real-Time Alerts: You receive immediate notifications for any suspicious activity, allowing you to act quickly.
- Compliance Management: Some of these tools help you maintain compliance with various regulations like GDPR or HIPAA.
- Customization: You can tailor the features like alerts and dashboards to your specific needs.
- Data Enrichment: These tools often provide additional context or information related to the threats detected, making it easier to assess the level of risk.
How much do these tools cost?
The cost of dark web monitoring tools can vary widely based on their feature sets, the size of your organization, and the number of users. Pricing models may include per-user, per-month charges, one-time setup fees, or a base fee plus additional costs for extra features.
What are the pricing models?
Pricing models can range from a simple per-user, per-month fee to more complex structures that involve base fees, additional feature costs, and one-time setup fees. Some may offer discounts for annual commitments.
What is the typical range of pricing?
Prices can range from as low as $10/user/month to as high as several hundred dollars per user per month for enterprise-grade solutions.
Which is the cheapest software?
The lowest-priced options generally start around $10/user/month but may have limited features.
Which is the most expensive software?
Enterprise-level solutions with advanced features can go up to several hundred dollars per user per month.
Are there any free tool options?
Some tools offer limited free versions or trials, but these are generally not sufficient for comprehensive dark web monitoring.
Can these tools integrate with my existing security infrastructure?
Many of these tools offer API integrations that allow you to incorporate them into your existing cybersecurity framework, thereby streamlining threat detection and response.
Other Data Management Tool Reviews
Summary
Choosing the right dark web monitoring tool is crucial for safeguarding your organization's data and reputation. This guide has walked you through various factors you should consider, from core functionalities to usability, and provided FAQs to address your immediate questions.
Key Takeaways
- Match functionality to needs: Not all dark web monitoring tools are created equal. Some excel at real-time threat alerts, while others are tailored for compliance or customization. Select a tool that aligns with your specific requirements.
- Evaluate cost and pricing structure: Understand that these tools can have diverse pricing models and costs can add up quickly. Be sure to get a clear picture of all fees, not just the per-user, per-month costs.
- Consider usability and support: Beyond features and price, the tool's usability can make or break your experience. Look for intuitive interfaces and robust customer support to ensure a smooth operation.
What Do You Think?
If you've used or know of any dark web monitoring tools that you believe should have made it onto this list, I'd love to hear your recommendations. Your input could help make this guide even more comprehensive and useful for others. Feel free to drop your suggestions in the comments section or reach out directly. Thank you for reading.
